Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- Deployment & Management
- :
- Re: QlikSense: SAML / FEDERATED SECURITY / SECURE ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
QlikSense: SAML / FEDERATED SECURITY / SECURE TOKENS
In White paper for QlikView:
SAML / FEDERATED SECURITY / SECURE TOKENS There are a number of different security systems that can make use of secure tokens to sign users into a range of systems. There are several different standards and sets of terminology around this approach such as SAML (Security Assertion Markup Language) and federated security such Active Directory Federation Services. Although each is different the approach from a QlikView perspective is similar. Here is how it typically works… In this approach, due to the level of integration required, a custom login page can be created to use the security API in QlikView. Although this mechanism is relatively simple to use it does require some knowledge of programming and this configuration is not ‘out of the box’. There are examples on how to implement this approach available on the QlikView Community. 3 The advantage of this approach is again to conform to an organization’s standard way for securing services. It again does require that an organization has in place a security system that offers this kind of functionality but QlikView has an approach for integrating with a range of vendors’ solutions. QlikView Server 8. User received QlikView content CLOUD 1. User requests QlikView content Custom Login Page 2. User redirected to Login System 5. Request QlikView content with token 4. Redirect user to QlikView with token 3. Login Against Login System 6. Validate token Login System CUSTOMER SITE/INTERNET 7. Token is OK and provide username/groups QlikView and the Cloud | 13 With Active Directory Federation Services (ADFS) it is possible for users to seamlessly log in to a non-domain cloud server without being prompted to log in as their internal Windows credentials are used during the process of logging in. This gives an excellent user experience and ADFS is often implemented within organizations alongside their regular Active Directory which means there is no requirement for an additional SSO product or set of users.
Has anyone seen this for QlikSense?
- « Previous Replies
-
- 1
- 2
- Next Replies »
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are looking for how you can set up Qlik Sense SAML with ADFS, here are some videos I created that go through the process of configuring and implementing Sense SAML with ADFS.
If you are interested in implementing security with Qlik Sense in a similar way to the way it is possible in QlikView, check out this video on the proxy API. You can use ticketing if you want.
Hope this helps.
Jeff G
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jeff,
Thank you so much for the videos on SAML with adfs.
I built a prototype based on the videos and it is working well. I'm curious if you could describe any trouble spots when doing this on an existing adfs deployment. I'm sure there is a wide variety of deployment scenarios with this but just describe some common issues.
It occurs to me that your videos use the certificates from the Qlik Sense server. In the case of an existing ADFS deployment do I have to use certificates from the ADFS server on Qlik?
Thanks for whatever insight you can provide
Thanks Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Chris,
I'm a big proponent of using certs from trusted authorities. If you have a cert on ADFS, you may have to issue another for the Qlik server, but then the virtual proxy for SAML is using the updated server cert.
So short answer is you can use either, but if you want to use the certs you have for ADFS that are trusted (not self-signed) you can likely make a go of it.
jg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jeff,
I am now at a client impelmenting ADFS with SAML on Qlik Sense and everything is looking good but I am getting 400 errors from sense.
As I said in my earlier post the ADFS environment is fairly mature all I can tell right now is that the virtual proxy does not like the saml request from the adfs server. I'm curious which of the final power shell tasks were specifically needed to make Sense work as opposed to the ones you were doing to avoid errors with the self signed certs?
One more thing in the Qlik Proxy security audit log I am seeing the following error
Command=Authenticate request;Result=-2147467259;ResultText=Error: The I/O operation has been aborted because of either a thread exit or an application request
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just came across this post as i am looking to do ADFS and this has been great information. I was just wondering, what options would be needed to remove the need for the users to enter their username and password? So its streamless once they access the url for the hub
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jessey,
Are you talking about replacing windows authentication popup when entering Qlik Sense? If not, how do you envision users authenticating (identity verification) before forwarding on to Qlik Sense.
There are lots of ways to make the auth process seamless, but at some point a user credential needs to be passed to Qlik Sense to identify the user who will access the solution. That can happen in code, but requires the credential to come from somewhere.
jg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
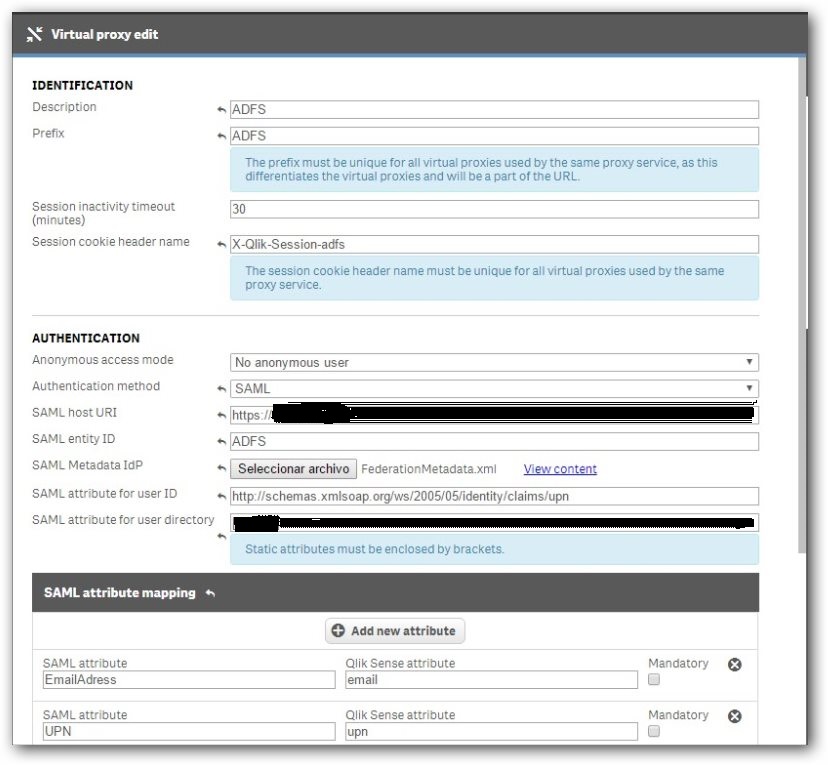
Jeff,
I am now at a client implementing ADFS with SAML on Qlik Sense and everything is looking good but I am getting 400 errors from sense. My ADFS environment is fairly mature all I can tell right now is that the virtual proxy does not like the saml request from the adfs server. I use the certificates of the ADFS enviroment to sign and decrypt, not the certificate of my QlikSense site.
Here is my virtual proxy configuration:
Can you help me?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jeff,
I am now at a client implementing ADFS with SAML on Qlik Sense and everything is looking good but I am getting 400 errors from sense. My ADFS environment is fairly mature all I can tell right now is that the virtual proxy does not like the saml request from the adfs server. I use the certificates of the ADFS enviroment to sign and decrypt, not the certificate of my QlikSense site.
Here is my virtual proxy configuration:
Can you help me?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are running into 400 errors it's likely 1 of 3 things.
1. The roledescriptor elements have not been removed from the federation metadata file before uploading to Qlik Sense.
2. Because you are using lower than Qlik Sense 2.0.7 or 2.2 and endpoint is set to use SHA256 signing encryption it's failing.
3. You are attempting Identity Provider initiated flow instead of service provider initiated flow. Qlik sense supports SP initiated flow only.
jg
- « Previous Replies
-
- 1
- 2
- Next Replies »