Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- No Email Address listed for Users in Qlik Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
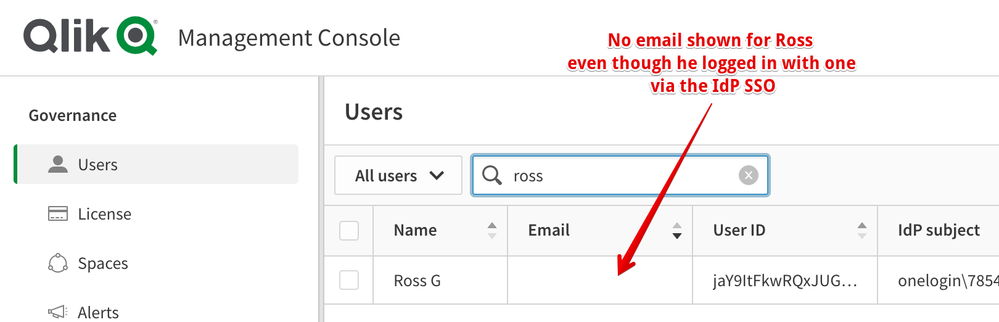
No Email Address listed for Users in Qlik Cloud
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No Email Address listed for Users in Qlik Cloud
May 10, 2022 3:01:03 PM
Jan 13, 2021 7:58:57 AM
Users listed under the Management console do no show the Email address associated with the user.
Environment
- Qlik Sense Enterprise SaaS
Disclaimer: The information below is subject to change as the Identity Providers continue to expand their solutions.
Cause
The identity provider (IdP) either has not provided evidence to Qlik Sense that the user's email address has been verified, or Qlik Sense has failed to process the specific IdP's non-standard claim name that indicates that the email has actually been verified.
Some Identity Providers allow the administrators to create users without a validation process. This is convenient but not recommended for security reasons, as the identity associated with an unverified email address is less trusted. Other vendors require a verification process but then may not supply the email_verified claim information to Qlik Sense Enterprise SaaS (a violation of the OpenId Connect specification perhaps?). Still others do it well but the name of the claim is not the standard name.
How do the popular Identity Provider vendors handle the email_verified claim?
The following vendors are known to have an email verification process that when exercised by the Identity Provider administrator provides the email_verified claim to Qlik Sense Enterprise SaaS at login without any special mapping:
- Okta, Auth0, Onelogin (v2), Google Identity, IBM Security Verify
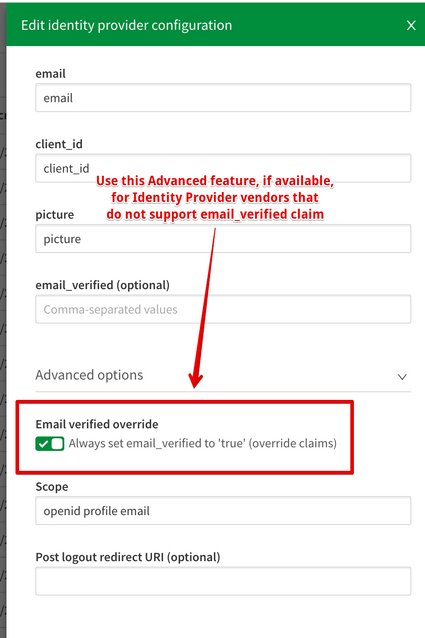
The following vendors support an email verification process but do not provide the necessary email_verified claim easily and so can be fixed within Qlik Sense Enterprise SaaS via the Email Verified Override toggle:
- Azure AD
Resolution
There is one official resolution that consists of ensuring that the specific IdP has verified the user's email address and has been configured to indicate this with the claim "email_verified":true.
Note that two workaround are included further down in the article in the case of the IdP not providing a standard email verification claim field or simply not supporting it.
It's difficult to provide blanket instructions on how to configure proper email verification as each Identity Provider vendor handles it differently. Details for each Identity Provider vendor tested to work with Qlik Sense Enterprise SaaS (there are many!) is beyond the scope of this article or Qlik Support, and should be performed by the administrator. We recommend a search for email_verified within your Identity Providers documentation on the web or look for other Qlik Community articles on this topic for the Identity Provider vendor of interest.
In order to confirm the issue lies on the IdP's claim response, logon with the specific user to the Qlik Sense SaaS tenant, open a new browser tab, and use the following URL to retrieve the claims provided by the IdP:
https://<tenantName>.<region>.qlikcloud.com/api/v1/diagnose-claims
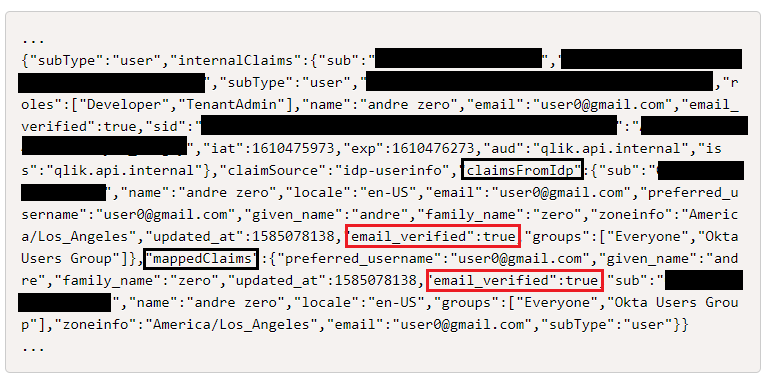
Here's an example JSON string response:
In the response above we see "email_verified":true in three places, for which we care only to the ones under the claimsFromIdp and mappedClaims lists.
With a response from the IdP such as the one above, it would be expected that the user's Email field would be populated with the user's email in the Management Console.
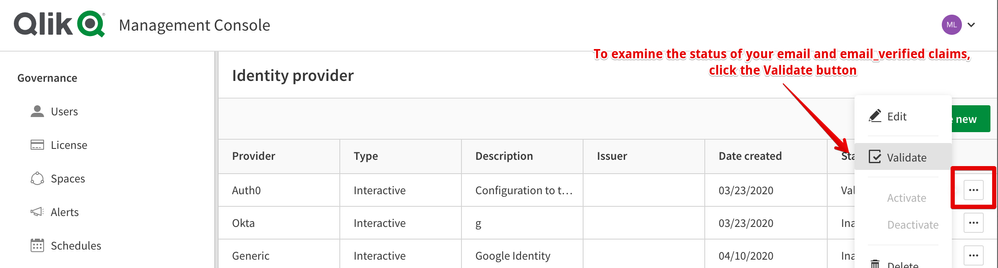
Another way to check on the above is to login with the specific user to the Management Console and under Identity Providers click on the Validate option.
Example:
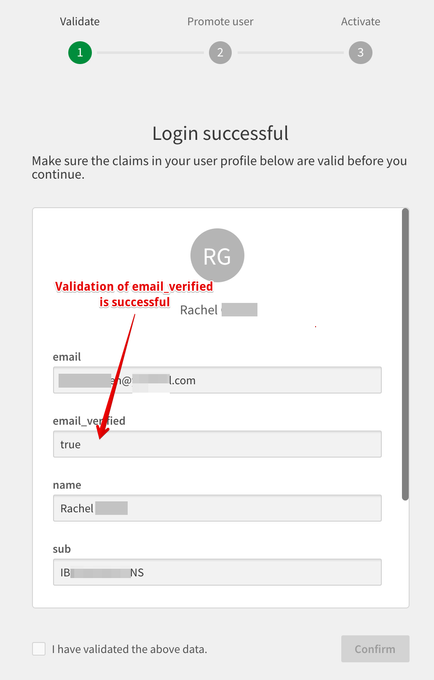
After supplying login credentials, the claims validation page will appear and show the email address and either email_verified as true, or a warning message.
Workaround(s):
1. If the IdP is providing email_verified claim but has named it different, adjust the Claims Mapping under the Identity Provider configuration via the Management Console.
Example:
2. If the IdP does not support the email_verfied claim, set the option Email Verified Override. This is only available for specific IdPs such as when selecting Azure AD in the configuration. The option is then available under the Advance settings.
Related Content