Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik Sense: Common error messages when using SAML
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik Sense: Common error messages when using SAML
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense: Common error messages when using SAML
Feb 1, 2022 4:18:56 AM
Oct 29, 2017 9:41:44 AM
This article gives an explanation of some of the common error messages.
Error 1:
Error 400 - Bad request
Contact your system administrator. The user cannot be authenticated by the SAML response through the following virtual proxy:
Error 2:
SAML mandatory attribute for user ID is missing
Error 3:
SAML assertion is expired
Error 4:
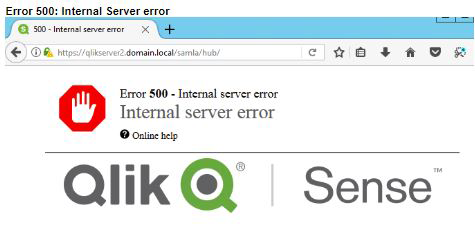
Error 500 - Internal server error
Internal server error
Error 5:
SAML assertion must be encrypted on an unsecured connection
Environment:
Qlik Sense Enterprise on Windows
Error 400: Bad request
This is the most common error message that is encountered when using SAML. It basically means that the SAML request is malformed, missing some mandatory information, or we are encountering a time sync issue.
Missing Attribute:
The first step to take when this error appears is to check the Servername_Audit_Proxy.txt (C:\Programdata\Qlik\Sense\log\Proxy\Trace)
WARN QlikServer2 Audit.Proxy.Proxy.SessionEstablishment.Authentication.SAML.SamlAuthenticationHandler 47 82c8cc12-5bf4-42a5-af04-b8e2c64d5c50 DOMAIN\Administrator SAML mandatory attribute for user ID is missing 0
The error is sometimes obvious as in the above example. An attribute is missing.
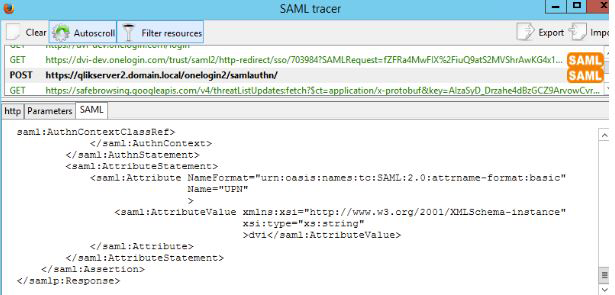
The second step would be to look into the SAML response and see if the SAML attribute you have set for your user ID is in there:
Check if you have an element <saml:Attribute ... Name="Nameofyourattribute" > inside the <saml:AttributeStatement> element.
In this example, the attribute we were trying to use for the User ID is Email. We see that it is not present in the <saml:AttributeStatement> element.
Time sync issue:
Verify that the SAML request is not rejected because it is "expired" or "SAML assertion is expired" and also result in "400: Bad request". This can happen if for example an AWS server with Sense installed on it was not configured to automatically update its date/time settings. The time difference between the identity provider and Sense can then lead to the message being rejected.
In this case, adjust time settings accordingly.
Error 500: Internal Server error:
This can have different reasons but the troubleshooting process is similar to the example above.
In SAML, error 500 usually indicates an error with the certificate used. Either the certificate used is incorrect or does not have the proper Cryptographic Provider.
In order to use SHA-256 in Qlik Sense with SAML, the cryptographic provider for the certificate applied on the Qlik Sense proxy must be "Microsoft Enhanced RSA and AES Cryptographic Provider".
This limitation does not apply to the certificate used by the Identity provider.
The Servername_Audit_Proxy.txt (C:\Programdata\Qlik\Sense\log\Proxy\Trace) will either indicate "could not decrypt data" or an error with ComponentSpace.SAML2.Exceptions.SAMLSignatureException.
SAML assertion must be encrypted on an unsecured connection:
All network traffic has to be encrypted, that means it's mandatory to use the port 443 in order to have a secure connection.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @fsiviero
Sorry for the confusion. I double-checked internally and the checkbox is only there for OIDC authentication.
For SAML authentication, attributes will be persisted if you fill something in the "additional attribute mapping" section. If you leave that section blank, then attributes won't be persisted, but you can synchronize some from a User Directory Connector instead if you want.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Damien_Villaret ,
Can SAML setup be done on RIM node (both load balancing and linked proxy ) or its mandatory to do it on central node.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Damien_Villaret ,
Can SAML setup be done on RIM node (both load balancing and linked proxy ) or its mandatory to do it on central node.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- « Previous
-
- 1
- 2
- Next »