Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Test Ability to Forge Requests in Qlik Sense Enter...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Test Ability to Forge Requests in Qlik Sense Enterprise on Windows
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Test Ability to Forge Requests in Qlik Sense Enterprise on Windows
Forging requests is a method that attackers use to circumvent the front-end GUI application to directly submit information for back-end processing. The goal of the attacker is to send HTTP POST/GET requests through an intercepting proxy with data values that is not supported, guarded against, or expected by the application's business logic. Some examples of forged requests include exploiting guessable or predictable parameters or exposing “hidden” features and functionality such as enabling debugging or presenting special screens or windows that are very useful during development but may leak information or bypass the business logic.
Vulnerabilities related to the ability to forge requests are unique to each application and different from business logic data validation in that its focus is on breaking the business logic workflow.
Applications should have logic checks in place to prevent the system from accepting forged requests that may allow attackers the opportunity to exploit the business logic, process, or flow of the application. Request forgery is nothing new; the attacker uses an intercepting proxy to send HTTP POST/GET requests to the application. Through request forgeries, attackers may be able to circumvent the business logic or process by finding, predicting, and manipulating parameters to make the application think a process or task has or has not taken place.
Applications must have logical controls in place to prevent the system from accepting forged requests that may allow attackers to exploit business logic or application flow.
In Qlik Sense Enterprise on Windows, attribute-based access control (ABAC) is defined as an access control method where user requests to perform actions on resources are granted based on assigned attributes of the user, assigned attributes of the resource, environment conditions, and a set of security rules that are specified in terms of those attributes and conditions.
Security rules control access to application streams in the hub, capabilities within applications (sheet, story, bookmark creation), and administrative capabilities in the QMC (publish apps, set stream access, create and run tasks).
Environment
- Qlik Sense Enterprise on Windows, All versions
Example
This example shows that HTTP responses can be manipulated to alter the web interface. The actual action and access related to the false UI options can not be executed, due to the back-end access control and missing user authorization.
- A user has limited access to Qlik Management Console.
- The HTTP response is captured and manipulated.
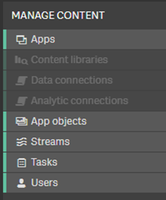
- The Users section is enabled in the web interface, without changing the deployment configuration
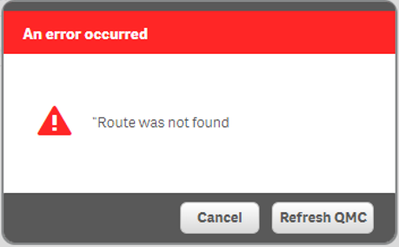
- Selecting the Users in the menu returns an error
Related Test Scenarios
- Test Ability to forge requests (OTG-BUSLOGIC-002)
References
- OWASP Testing Guide 4.0
https://owasp.org/www-project-web-security-testing-guide/assets/archive/OWASP_Testing_Guide_v4.pdf - Qlik Sense Enterprise Architecture, Scalability and Security
https://www.qlik.com/us/-/media/files/resource-library/global-us/register/whitepapers/wp-qlik-sense-... - Qlik Help: Qlik Sense Enterprise on Windows security
https://help.qlik.com/en-US/sense-admin/February2022/Subsystems/DeployAdministerQSE/Content/Sense_De...