Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- ROBOT vulnerability found with security scan on a ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
ROBOT vulnerability found with security scan on a Qlik Sense Enterprise on Windows system
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ROBOT vulnerability found with security scan on a Qlik Sense Enterprise on Windows system
Apr 12, 2021 9:56:48 AM
Apr 12, 2021 9:56:48 AM
When TLS 1.2 is enabled on the Windows operating system hosting the Qlik Sense Enterprise on Windows environment, the ROBOT vulnerability may be detected when performing a security scan.
Environment
Resolution
According to https://robotattack.org/ a way for you to get in a non-vulnerable state is to disable RSA encryption.
"ROBOT only affects TLS cipher modes that use RSA encryption. Most modern TLS connections use an Elliptic Curve Diffie Hellman key exchange and need RSA only for signatures. We believe RSA encryption modes are so risky that the only safe course of action is to disable them. Apart from being risky these modes also lack forward secrecy.
By disabling RSA encryption we mean all ciphers that start with TLS_RSA. It does not include the ciphers that use RSA signatures and include DHE or ECDHE in their name. These ciphers are not affected by our attack.
Based on some preliminary data we also believe the compatibility costs of disabling RSA encryption modes are relatively low. Cloudflare shared with us that around one percent of their connections use the RSA encryption modes. Disabling these modes on the HTTPS server operated by one of the authors caused no notable problems."
To achieve this, disable the following ciphers using IIS crypto, see Supported TLS and SSL Protocols and Ciphers
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256.CBC.SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC.SHA
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
After disabling TLS_RSA_WITH_AES_256_GCM_SHA384 and TLS_RSA_WITH_AES_128_GCM_SHA256 the services are not starting up. The log show that there was a problem communicating with the license service. Qlik Sense version - September 2019. Any ideas?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Sai_S
I recommend posting your query directly in our Deployment forum to make use of the wider reach of our community and our active support engineers. When posting, include the symptoms of your issue, any error messages that you have seen, and what troubleshooting steps you've already taken. Feel free to refer back to this article as an example of what you tried.
We also invite you to make use of our chat function if you require more direct assistance or a case to be logged.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
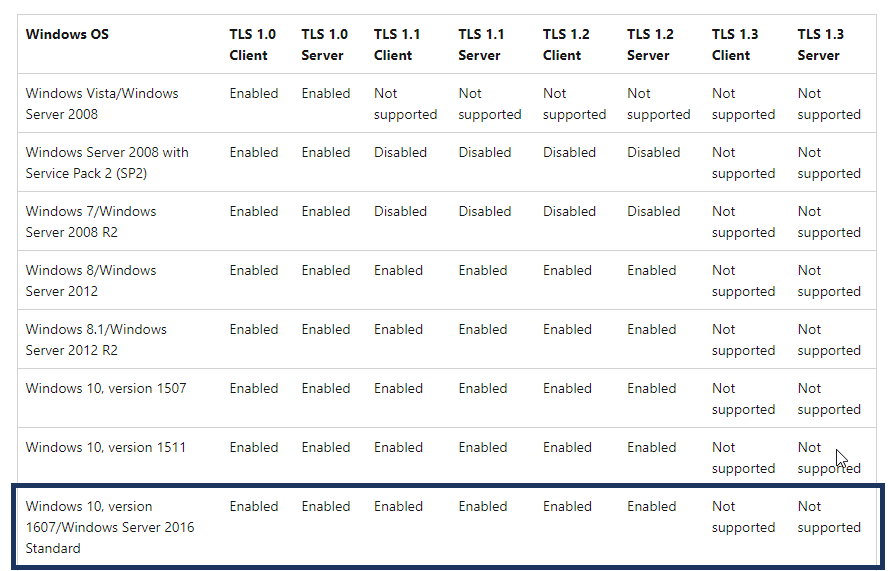
Hi I went to the link above https://docs.microsoft.com/en-us/windows/win32/secauthn/protocols-in-tls-ssl--schannel-ssp-#tls-prot...
But their latest server is 2008. Do you know if TLS 1.3/2.0 are fully supported for Server 2016?
Thanks
McCutchan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Mccutchan1
I am afraid I do not understand your question.
The site linked has Server 2016 standard listed. As per the list, 1.3 is not supported on Windows Server 2016.
Though if you have doubts I recommend reaching out to your IT administrator.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sorry Sonja, seems like I need some new glasses. 🙂