Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Discover
- :
- Blogs
- :
- Product
- :
- Design
- :
- Qlik Sense SAML – A standardized approach to authe...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Hello everyone, today I have the pleasure of introducing Jeff Goldberg as our guest blogger - (jog) - Jeff is a Senior Enterprise Architect on the Americas Pre-sales team who has worked in various technology positions for over 15 years. In between running half-marathons and crushing crossfit workouts ![]() , Jeff focuses on integration, deployment, automation, security, and api topics across a wide range of software. If you have a technical challenge, Jeff can put you on a path to figuring out the best way to overcome it. Jeff has the extreme pleasure of introducing you to SAML authentication with Qlik Sense, not only in text - but as well in supporting videos. Thanks for this valuable contribution Jeff!
, Jeff focuses on integration, deployment, automation, security, and api topics across a wide range of software. If you have a technical challenge, Jeff can put you on a path to figuring out the best way to overcome it. Jeff has the extreme pleasure of introducing you to SAML authentication with Qlik Sense, not only in text - but as well in supporting videos. Thanks for this valuable contribution Jeff!
Qlik Sense SAML
With the release of Qlik Sense 2.0, we introduced SAML as an authentication option between enterprise identity management systems (known as identity providers) and Qlik Sense. While SAML is a standard for authentication and authorization, it is open to interpretation and variability in its implementation. Consequently, implementing SAML can be a bit tricky. The goal of this blog post is to demystify SAML and provide some examples you can use to implement it with Qlik Sense.
SAML stands for Security Assertion Markup Language, an xml based authentication and authorization standard for web applications to exchange user credentials and attributes. SAML works between two parties, an identity provider (IdP) and a service provider (SP), to facilitate single sign-on access to secure content for a user.
Identity providers come in a variety of shapes and sizes. Salesforce.com, Active Directory Federation Services, and Ping Federate are just a few of the options available for handling the authentication components of the SAML handshake. The service provider is the system with the content we want to access. In this case, Qlik Sense is the service provider.
The figure below illustrates the SAML authentication process.
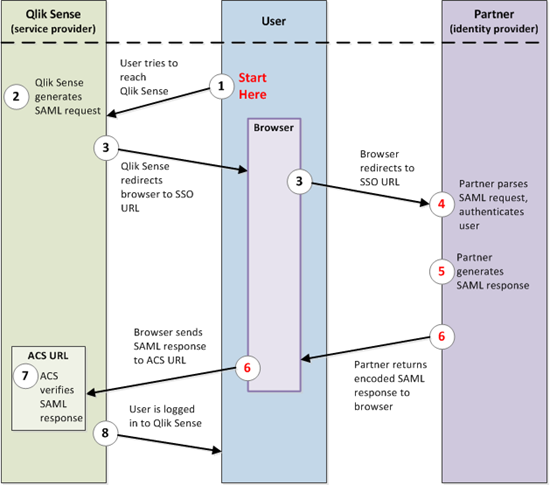
Keep in mind the SAML protocol is an open standard, therefore, implementing the solution between the SP and the IdP differs based on the requirements of the chosen provider.
For example:
- ADFS metadata contains a whole section of information that needs to be removed before it is imported into Qlik Sense.
- With Ping Federate, the IdP configuration needs to have the name ID format for the SAML response manually set to transient or the user authentication to Qlik Sense will fail.
- One login doesn’t care about the name ID format for the response.
Bottom line, expect some trial and error when configuring SAML, regardless if it’s with Qlik Sense or some other solution.
To ease the pain and hopefully reduce frustration, we have created some videos to help walk through configuring different SAML identity providers with Qlik Sense. As we encounter more flavors of IdP, we will create content to help with configuration.
For now, have a watch of the following videos, enjoy!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.