Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Vulnerability Concern: Username and password sent ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Vulnerability Concern: Username and password sent in plain text
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vulnerability Concern: Username and password sent in plain text
Feb 20, 2023 3:50:41 AM
Aug 11, 2020 5:10:46 PM
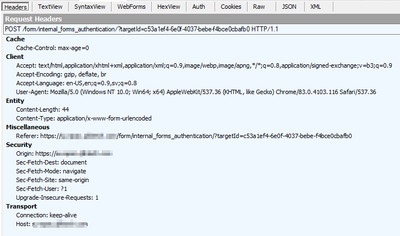
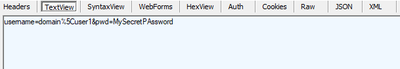
A penetration test shows traffic traces between a client device and a server that reveals the user's credentials. This might be flagged as a potential risk for man-in-the-middle (MITM) attacks in a security report.
Below images show an example of a login request through Qlik Sense form login, where the HTTP request body contains the user's credentials in plain text.
Diagnosis
In this scenario, the end-user typically enters credentials into a form on a login page. The login form usually hides the password from plain sight by masking it on the screen, but the entries are still plain text.
The communication between the client browser and server should be secured and encrypted with HTTPS so that the plain text credentials and any other content are encrypted at all times during transport between the client device and server.
An attacker does not have the required certificates, and can therefore not decrypt intercepted HTTPS traffic and the server reveal the content.
This test result is a false-positive since the penetration tool, in this case, acts as the connecting and trusted client, and thereby decrypts the traffic and consequently can also display and analyze the traffic content.
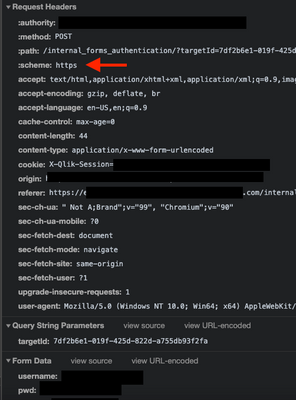
Qlik Sense on Windows defaults to HTTPS. All communication is under TLS. When a user is attempted to log in, the web browser establishes a TLS connection with the server and is able to view requests in plain text (in the browser). This does not mean the request has gone out into the world without encryption. From the provided screenshots, the target URL is omitted. I'm unable to verify if the scheme in the browser is HTTP or HTTPS (as seen in the below screenshot)
A change to your environment would require you to communicate with your support in order to reset the proxy to the default configuration.
Solution
Enforce HTTPS on all access to the server-side.
Based on the above this is not deemed to be a security vulnerability by the SSO team. This has gone through other auditors and has never reported as a security concern.
References
- Wikipedia: Man-in-the-middle attack
https://en.wikipedia.org/wiki/Man-in-the-middle_attack - Wikipedia: False positives and false negatives
https://en.wikipedia.org/wiki/False_positives_and_false_negatives
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @ToniKautto
Is there any approach where we can hide the plain text paaswords?
Currently it is breaching our security policies.
Regards,
Rohit Gharat
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @_rohitgharat
Let me get in touch with our engineers to verify the article.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @_rohitgharat
We have run this by our security office and the recommendation in the article remains the solution to this question.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Is this article also relevant for Qlik Alerting on Windows?
Regards,
Lucky
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Luck
This is not a Qlik-specific issue and generally applies to any unsecured connection (HTTP vs HTTPS) which is used to transport passwords. Though I believe Qlik Alerting does not submit passwords. Should you locate what you believe to be a security issue, please submit a ticket with Support so it can be correctly analyzed.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Sonja_Bauernfeind ,
I've submitted a ticket, but from the response we get by Support, it is deemed the same in Qlik Alerting (reported for QlikSense & Alerting).
Could we get a proof document from the solution mentioned above :
"Based on the above this is not deemed to be a security vulnerability by the SSO team. This has gone through other auditors and has never reported as a security concern."
From which auditors did the report on the above test come from?
Could share the report from the auditors on the above & does not deem this as a security concern?
Regards,
Lucky
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Luck
Please send me the ticket number you submitted in direct messages. As this will need to be handled by our security office and I cannot provide you with assistance on this article.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@ToniKautto @Luck @_rohitgharat @Sonja_Bauernfeind , can you confirm if this is applicable for Qlik Replicate as well ?
"Based on the above this is not deemed to be a security vulnerability by the SSO team. This has gone through other auditors and has never reported as a security concern."
We too have same issue, our security auditor mentioned the same, sensitive data is in plain text.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @rahulmagotra
Enforcing HTTPS on all access to the server-side will encrypt traffic.
This test result is a false-positive since the penetration tool, in this case, acts as the connecting and trusted client, and thereby decrypts the traffic and consequently can also display and analyze the traffic content.
All the best,
Sonja