Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- QlikView Administration
- :
- Configurable LDAP to Tivoli From QV Server 10
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Configurable LDAP to Tivoli From QV Server 10
We are currently using a Tivoli Web Proxy to validate users, then passing that validated username to Qlikview Server (v10) in the http header. Because we are going to have 50 initial users (and potentially many more going forward) I was trying to set up a configurable LDAP connection back to an LDAP directory on our Tivoli machine to look up group assignments. The goal would be to assign group names to Qlikview documents and opposed to 50 individual usernames, but I can't get the group name to pull back.
- Tags:
- qlikview_deployment
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jeff and Sylvia,
The solution is somewhat complex because of the differences between AD's group authentication and Tivoli's. Essentially, there are 2 problems: (1) there is no equivalent to a sAMAccountName in Tivoli that would exist as an attribute on both User and Group nodes; the QDS attempts to lookup an attribute that would exist at both levels, and is unable to find it; and (2) Distinguished Names are not actually stored in Tivoli; the Distinguished Name attribute exists, but is reserved by the system so that it can be auto-populated on-demand; the QDS attempts to reference a group's distinguished name but is not able to.
I'm not sure how to modify the Tivoli schema itself, so this solution makes use of 2 fields that I am assuming are currently not populated: (1) description and (2) mobile.
- For each user, Tivoli stores group memberships in hidden attributes called "ibm-allgroups" which are the equivalent to "memberof" in Active Directory. Unfortunately, the values of these attributes are stored in distinguished format (e.g. cn=mygroup,cn=SecurityGroups,secAuthority=Default). Create a new rule in Tivoli that will take just the "mygroup" part of the value and store it in attribute "mobile." You should create a mobile attribute for each instance of "ibm-allgroups" for each user.
- For both user and groups, we need to create an attribute that simulates a sAMAccountName. We will populate the attribute "description" with this. So if you have a group whose ID is "qlikview_group1" and a user whose UID is "qv_user1", create a Tivoli rule that sets the group's "description" attribute to "qlikview_group1" and the user's "description" attribute to "qv_user1." Propogate these changes for all users and groups.
- In QlikView, create a Configurable LDAP DSC in QEMC >> System >> Directory Service Connectors. Enter the proper credentials (although I'm assuming this is already working for you since you can authorize usernames). Enter the following settings:
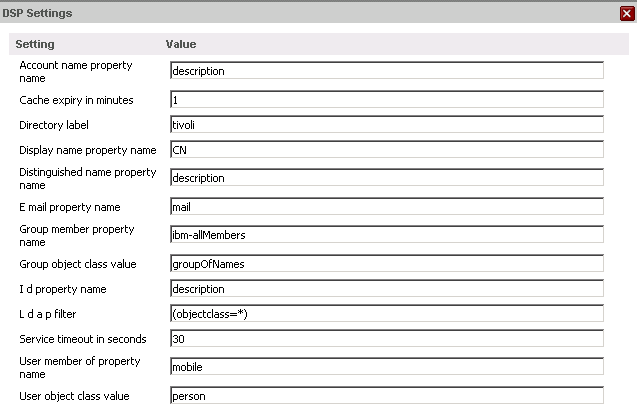
- That's it! You can now authorize groups on documents. In the Document Authorization tab, groups can either be browsed to in the usual way or simply entered in the format: tivoli\groupname
Cheers,
Vlad
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It almost appears as if I have a setting wrong and DSC isn't even being used. When we configure the connection, it polls the Tivoli machine without issue. However, when we log on as a user through the web I don't see anything that attempts to then get a group name based on the user id (we are using DMS authorization).
I've been reading through the server documentation and so far haven't found a location to 'turn on" our configured DSC - what am I missing? Does our web proxy need to pass the http string to the DSC url as opposed to the standard server url?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, was able to get the directory service connector working by specifying the 'Directory Label' in the settings as the name of the QlikView Directory Service. Now it loads the connector dll's, although are still having issues looking up group names that are associated with the actual users.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jeff,
Are you able to find any solution for reading the individual user name from the group user name in TDS?
We have similar problem here.
Thanks,
Silvia
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I haven't yet. We are in the process of setting up our development environment, and when complete (next two weeks) I'm planning on engaging a QlikView consultant to help take a look at it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jeff and Sylvia,
The solution is somewhat complex because of the differences between AD's group authentication and Tivoli's. Essentially, there are 2 problems: (1) there is no equivalent to a sAMAccountName in Tivoli that would exist as an attribute on both User and Group nodes; the QDS attempts to lookup an attribute that would exist at both levels, and is unable to find it; and (2) Distinguished Names are not actually stored in Tivoli; the Distinguished Name attribute exists, but is reserved by the system so that it can be auto-populated on-demand; the QDS attempts to reference a group's distinguished name but is not able to.
I'm not sure how to modify the Tivoli schema itself, so this solution makes use of 2 fields that I am assuming are currently not populated: (1) description and (2) mobile.
- For each user, Tivoli stores group memberships in hidden attributes called "ibm-allgroups" which are the equivalent to "memberof" in Active Directory. Unfortunately, the values of these attributes are stored in distinguished format (e.g. cn=mygroup,cn=SecurityGroups,secAuthority=Default). Create a new rule in Tivoli that will take just the "mygroup" part of the value and store it in attribute "mobile." You should create a mobile attribute for each instance of "ibm-allgroups" for each user.
- For both user and groups, we need to create an attribute that simulates a sAMAccountName. We will populate the attribute "description" with this. So if you have a group whose ID is "qlikview_group1" and a user whose UID is "qv_user1", create a Tivoli rule that sets the group's "description" attribute to "qlikview_group1" and the user's "description" attribute to "qv_user1." Propogate these changes for all users and groups.
- In QlikView, create a Configurable LDAP DSC in QEMC >> System >> Directory Service Connectors. Enter the proper credentials (although I'm assuming this is already working for you since you can authorize usernames). Enter the following settings:

- That's it! You can now authorize groups on documents. In the Document Authorization tab, groups can either be browsed to in the usual way or simply entered in the format: tivoli\groupname
Cheers,
Vlad