Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- SSL Security error using Microsoft OLE DB Provider...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SSL Security error using Microsoft OLE DB Provider for SQL Server
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSL Security error using Microsoft OLE DB Provider for SQL Server
May 22, 2023 7:14:16 AM
Feb 21, 2019 1:48:24 PM
Tasks using 'Microsoft OLE DB Provider for SQL Server' are failing with the following error:
Possible Error 1:
Error: Connector connect error: ErrorSource: Microsoft OLE DB Provider for SQL Server, ErrorMsg: [DBNETLIB][ConnectionOpen (SECCreateCredentials()).]SSL Security error.
Possible Error 2:
ErrorMsg: [DBNETLIB][ConnectionOpen (SECDoClientHandshake()).]SSL Security error.
Environment:
- All QlikView versions
- All Qlik Sense versions
Resolution:
The source and destination servers do not have aligned TLS versions enabled.
For example, if the data source only has TLS 1.0 enabled, while the Qlik product is installed on a Windows 2016 machine that disallows 1.0 and uses either TLS 1.1 or TLS 1.2, then the data source needs to be upgraded to support TLS 1.1 or TLS 1.2, or the security protocols need to be aligned.
In this example, the currently deployed Microsoft OLE DEB Providers for SQL do not support TLS 1.2 yet.
Please verify what version you have installed and confirm if you need to upgrade your data source: https://support.microsoft.com/en-us/kb/3135244
Recommended Fix:
Upgrade your data source so that the TLS versions between the data source and Qlik Sense or QlikView server match.
Alternative Fix:
Align the TLS versions used. Note that the example we use here configures TLS 1.0. We do not recommend the use of TLS 1.0, it is simply used for demonstration purposes.
If the registry keys are not present, the script under the following article should add them leaving only TLS 1.2 enabled TLS and SSL Support in Qlik Sense: How to configure Qlik Sense and TLS . Then TLS 1.0 may be enabled as mentioned below.
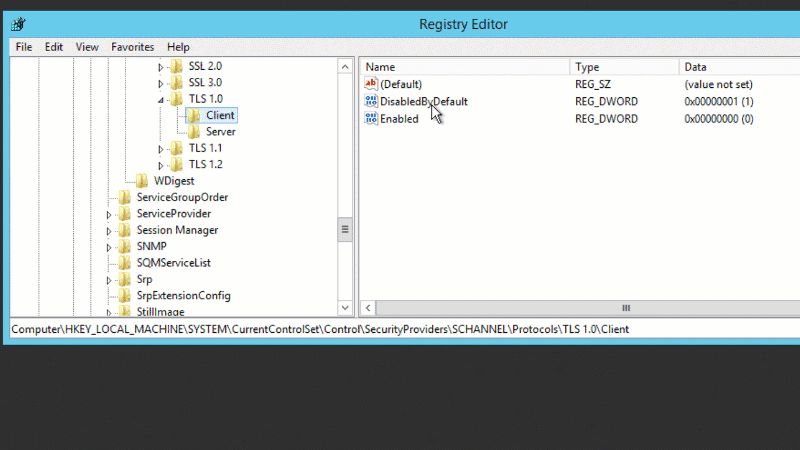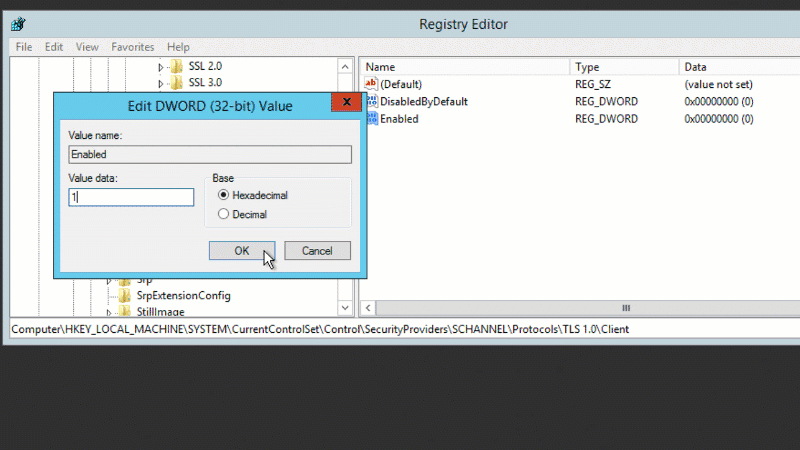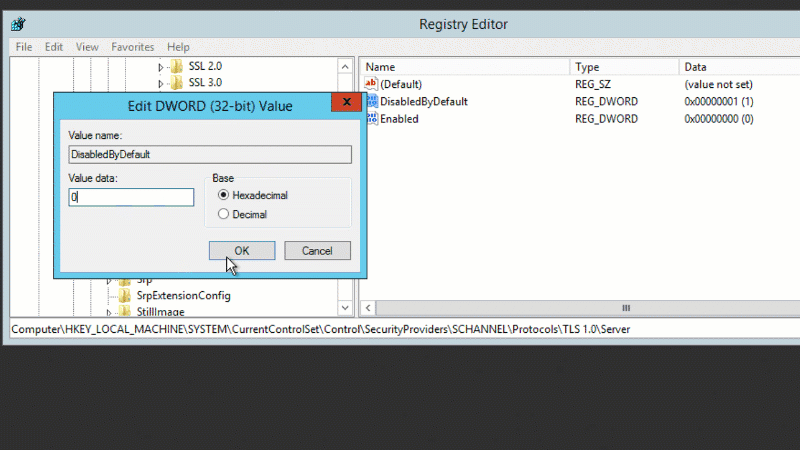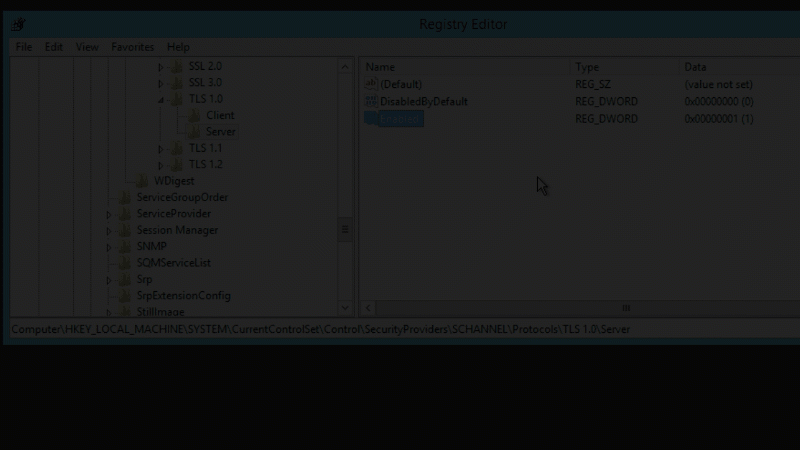
TLS 1.0 can be enabled with the following registry changes:
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] "Enabled"=dword:00000001
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server] "DisabledByDefault"=dword:00000000
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] "Enabled"=dword:00000001
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client] "DisabledByDefault"=dword:00000000
If the organization policy requires TLS 1.1 to be disabled, this can be done after the installation completes:
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] "Enabled"=dword:00000000
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Server] "DisabledByDefault"=dword:00000001
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] "Enabled"=dword:00000000
- [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] "DisabledByDefault"=dword:00000001