Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Discover
- :
- Blogs
- :
- Product
- :
- Support Updates
- :
- Qlik Sense Hub and QMC with a custom SSL certifica...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
If you’ve just installed Qlik Sense Enterprise, then this image probably looks familiar. Alternatively, Chrome might display The site's security certificate is not trusted, while Firefox may report This Connection is Untrusted.
By default, Qlik Sense uses a self-signed certificate to enable HTTPS access across both the Hub (https:// YourSenseServer/hub) and the Management Console (https://YourSenseServer/qmc). But self-signed certificates cannot be validated or trusted by web browsers and tend to prompt a warning message.
That's alright though. All we need is the following:
- An additional (signed) certificate.
- A brief (5 minute) downtime of the Qlik Sense Proxy.
- And, I suppose, this blog post for the instructions.
So, let’s get started.
What is the current certificate used for?
During the initial install, the Qlik Sense Repository Service creates a set of certificates. Their purpose is to:
- Secure Service Communication and Service Authentication.
Qlik Sense uses certificates to authenticate its service across all nodes. See the Qlik Sense Online Help for details. In addition, other products (such as Qlik NPrinting) require these certificates to be establish a connection.
- HTTPS enabled access for the Hub the QMC.
Note: We will not modify, replace, or remove the originally created certificates. Doing so will break service communication.
What we’ll do instead is to add an additional one.
Certificate options, or: What type of certificate is right for me?
There are three possible types of certificates for us to use.
- A certificate purchased from and signed by a trusted CA (Certificate Authority) such as VeriSign, Thawte, Geotrust, etc.
- A certificate provided and signed by your own Enterprise CA (Certificate Authority).
- And, of course, a self-signed one. Those can be created by any number of applications, such as Microsoft IIS, but is generally only recommended for test environments. More so, it has the potential side effect of teaching users to ignore browser warnings, which we do not want.
Requirements, or: What to look out for when getting your cert.
- The certificate itself must contain a private key
- Has an up to date valid from / valid to date range
- Is signed by a valid and OS or browser configured Certificate Authority
When support gets questions, they are most often related to a certificate missing the private key. Always verify the certificate comes bundled with one when you install it.
It’ll look like this:
As far as formats and algorithms are concerned, the following are confirmed to work with Qlik Sense:
- Certificates that are x509 version 3
- Use signature algorithm sha256RSA
- Use signature hash algorithm sha256
Where to get a certificate and how to do a CSR?
The Certificate Authority you chose will have instructions for this, and if you are looking to get a self-signed one or one from your corporation's CA, then a local administrator can provide the certificate to you.
Either way, you are going to need to generate a Certificate Signing Request (CSR) to pass on to your CA. There are tools out there to get that done with, such as certreq from Microsoft (found here), and SSLhopper has a great article on that, which I often send to customers when they ask us about CSRs and how to do them.
Once you obtain the certificate, we'll move on to installing it and activating it in Qlik Sense. This will be done in three quick steps:
- Import
- Get the Thumbprint
- Provide Thumbprint to the Proxy
Importing the Certificate
As mentioned before, we are not replacing certificates. The already existing ones will not be deleted. Doing so would break service authentication between the individual Qlik Sense services and render the system… broken.
Step 1:
On the Qlik Sense node running the Qlik Sense Proxy, log on with the user running the Sense services. This is important since the certificate needs to be accessible for this account.
Step 2:
If the certificate was saved in the .pfx format, then all you need to do is double click the file. Follow the prompt to import the certificate into the Personal store.
Longer Step 2:
If you want to import it manually or verify if it was correctly installed, then we'll need to do a little more work.
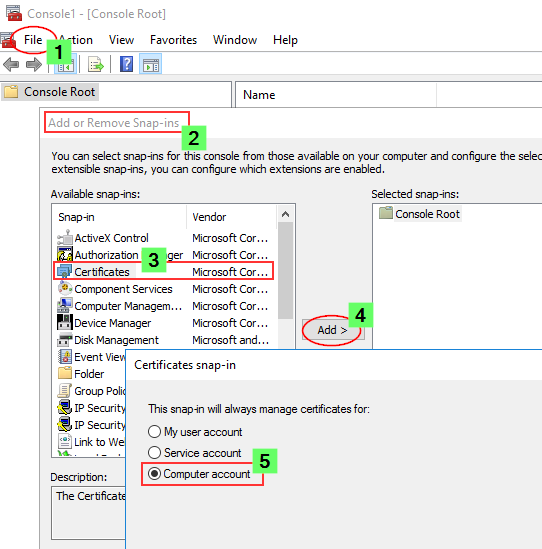
- Launch the Microsoft Management Console (mmc.exe) on the Proxy node
- In the MMC, go to File > Add / Remove Snap-in...
- Select Certificates and click Add
- Select Computer account, click Next, select Local computer and click Finish
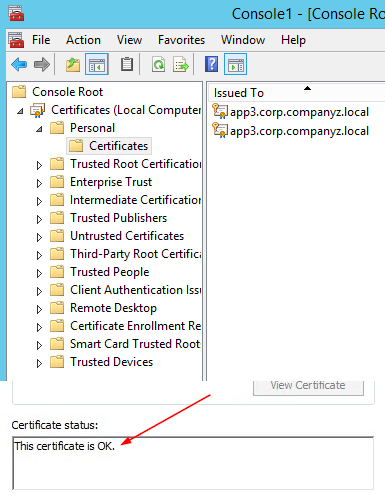
- In the MMC, go to Certificates (Local Computer)/Personal
- In the MMC, go to Actions > All Tasks > Import...
- Browse to the certificate file provided to you from your CA
- Follow the instructions on the screen to import the certificate, including the private key
- Verify the new certificate has been imported into Certificates (Local Computer) > Personal > Certificates and that it contains a private key
- Double-click the Certificate > Certification Path and confirm it shows "This certificate is OK"
Getting the Thumbprint
Well, since we are already in the MMC, let's open the freshly installed certificate again.
- Switch to the Details tab and scroll down until you find Thumbprint
- Mark the entire thing and copy it into, for example, Notepad.
Configuring the Qlik Sense Proxy
Almost done!
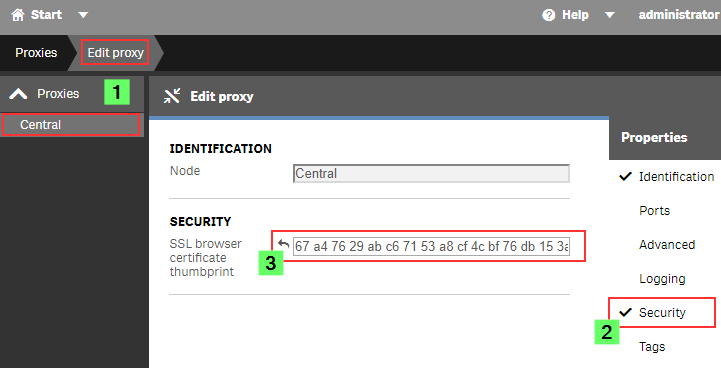
- Open the Qlik Sense Management Console (QMC)
- Go to Proxies
- Double click the Proxy you want to use (or select and choose Edit)
- Enable the Security options in the Properties panel on the right
- Paste the certificate Thumbprint into the SSL browser certificate thumbprint text box.
Click Apply.
The Sense Proxy will now restart. During the restart, it will be using Windows API calls to correctly bind the new certificate to its SSL ports.
Verification, or: How to prove the certificate was accepted.
In the web browser:
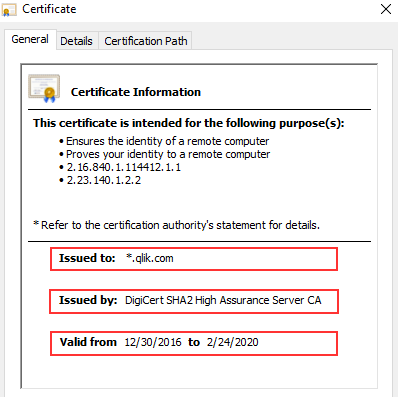
When opening the Qlik Sense Hub or QMC, the certificate will now be displayed in the browser. This may look different depending on the web browser, but in Google Chrome you can click the padlock to the left of the URL to verify what certificate is used.
The information displayed needs to match the properties of the certificate you installed.
In the log files:
If you’d rather see what the Qlik Sense Proxy service is doing, then you can directly check up on that, too.
On the Proxy node, go to C:\ProgramData\Qlik\Sense\Log\Proxy\Trace and open the Security log file from just after the last start.
It will now print a slightly different message than before:
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.LoggingDigester DOMAIN\_service Setting crypto key for log file secure signing: success
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.SecretsKey DOMAIN\_service retrieving symmetric key from cert: success
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.CryptoKey DOMAIN\_service setting crypto key: success
Security.Proxy.Qlik.Sense.Communication.Security.CertSetup 'CN=localhost' (08C871933A58E072FED7AD65E2DB6D5AD3EAF9FA) as SSL certificate presented to browser, which is a 3rd party SSL certificate
And that's it!
There isn't much more to it in a standard Qlik Sense Enterprise installation, but if you have more questions, then maybe a few of these articles can help:
I applied my certificate and it seems to be using it correctly, but browsers are still saying the Common Name is Invalid?
ERR_CERT_COMMON_NAME_INVALID when using 3rd party certificate
Qlik Sense keeps reverting to the default and complains it can't find a valid ssl certificate with the thumbprint.
The certificate may not have a Private key or the service account does not have access to it.
How to: Manage Certificate Private Key
The Qlik Sense Service account doesn't have admin privileges and the certificate is not accepted.
I hope that this was useful 😊 Stay tuned for an upcoming post where we’ll focus on QlikView and how to enable HTTPS for its AccessPoint, and don’t forget to subscribe to this blog for more content delivered by #QlikSupport. We’ll be watching for your comments and questions and we’ll to get back to you as soon as possible. Your feedback is always appreciated.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.