Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- Deployment & Management
- :
- Qlik Sense still using default certificate rather ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense still using default certificate rather than SSL certificate (Couldn't find a valid ssl certificate with thumbprint)
Hello, we recently deployed Qlik Sense on a Windows EC2 instance, and we are trying to replace the default AWS certificate with a self-signed cert. To do so we took the following steps:
- Generated an SSL cert (detailed steps below)
- Imported this cert to the MMC
- The fullchain cert is in the personal store, the intermediate cert is in the Intermediate Certification Authorities Store, and the root cert is in the Trust Root Certification Authorities Store.
- Gave the qlik service user read access to the private key
- Verified the certificate status of the fullchain cert reads "This certificate is OK."
- Added the thumbprint of the cert to the central proxy in the QMC
- Added the domain to the host allowlist in the virtual proxy configuration
- Restarted the qlik sense services
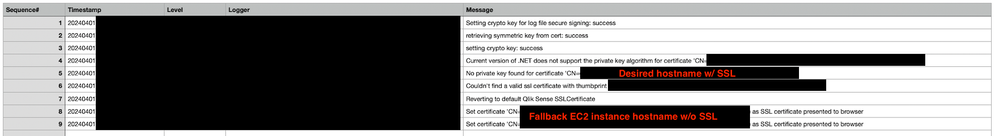
We are able to access the qlik sense hub from the domain we configured, but we get an invalid certificate error, and it shows that it is using the default AWS certificate rather than the one we configured. The security proxy logs contain the error "Couldn't find a valid ssl certificate with thumbprint <thumbprint>", where the thumbprint is that of our SSL certificate, followed by "Reverting to default Qlik Sense SSLCertificate".
Searching around led us to this article, but as mentioned above, we've verified that the certs are in their proper stores.
Any assistance would be appreciated, thanks!
Detailed steps about how the cert was generated:
- Followed these instructions to set up CertBot on Windows
- Certificate is saved at: C:\Certbot\live\my-domain\fullchain.pem
- Key is saved at: C:\Certbot\live\my-domain\privkey.pem
- Installed Git for Windows to get OpenSSL
- Converted the
fullchain1.pemcert chain to a .crt file- ```openssl x509 -in C:\Certbot\archive\my-domain\fullchain1.pem -out C:\Certbot\archive\my-domain\fullchain1.crt```
- Converted just the root CA cert to a .crt file
- ```openssl x509 -in C:\Certbot\archive\my-domain\cert1.pem -out C:\Certbot\archive\my-domain\cert1.crt```
- Generated a pcks12 file containing the full chain, private key, and root cert
- ```openssl pkcs12 -export -out fullchain1.pfx -inkey C:\Certbot\archive\my-domain\privkey1.pem -in C:\Certbot\archive\my-domain\fullchain1.crt -certfile C:\Certbot\archive\my-domain\cert1.crt```
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CNG certificate support is not fully implemented while CryptoAPI is fully supported. So the certificate needs to be converted before it will work.
See below article
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CNG certificate support is not fully implemented while CryptoAPI is fully supported. So the certificate needs to be converted before it will work.
See below article