Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
Recent Documents
-
Qlik Sense Enterprise on Windows and the PostgreSQL CVE-2025-1094 vulnerability
PostgreSQL has identified a vulnerability (CVE-2025-1094) that allows for SQL injection under certain scenarios. For more information, see CVE-2025-10... Show MorePostgreSQL has identified a vulnerability (CVE-2025-1094) that allows for SQL injection under certain scenarios. For more information, see CVE-2025-1094: PostgreSQL quoting APIs miss neutralizing quoting syntax in text that fails encoding validation.
Resolution
To allow for quick mitigation of PostgreSQL vulnerabilities, Qlik offers the ability to run and manage your own PostgreSQL instance independently of what Qlik Sense Enterprise on Windows is shipped with. This allows for direct control of your PostgreSQL instance and facilitates maintenance without a dependency on Qlik Sense. Further Database upgrades can then be performed independently and in accordance with your corporate security policy when needed, as long as you remain within the supported PostgreSQL versions.
Recommendations
Upgrade PostgreSQL
If you have already installed a standalone PostgreSQL database, or if you have used the Qlik PostgreSQL Installer (QPI) to upgrade and decouple your previously bundled database, then you can upgrade PostgreSQL at any time. This means you control maintenance and can immediately react to potential PostgreSQL security concerns by upgrading to a later service release or a later major version.
See Qlik Sense Enterprise on Windows: How To Upgrade Standalone PostgreSQL.
Verify your Qlik Sense Enterprise on Windows version's System Requirements before committing to a PostgreSQL version.
Unbundle and upgrade PostgreSQL using QPI
If you have not yet installed a standalone PostgreSQL instance, this is the preferred method to gain direct control to upgrade at your own pace. For instructions, see Upgrading and unbundling the Qlik Sense Repository Database using the Qlik PostgreSQL Installer.
Manually switch to a dedicated PostgreSQL database
An alternative method to migrate to a standalone PostgreSQL instance is available in How to configure Qlik Sense to use a dedicated PostgreSQL database.
Related Content
- System requirements for Qlik Sense Enterprise
- Qlik Sense Enterprise on Windows: How To Upgrade Standalone PostgreSQL
- Upgrading and unbundling the Qlik Sense Repository Database using the Qlik PostgreSQL Installer
- How to configure Qlik Sense to use a dedicated PostgreSQL database
Internal Investigation ID(s)
SUPPORT-896
Environment
- Qlik Sense Enterprise on Windows
-
Qlik Talend Cloud Hybrid Data StewardShip Rules and Semantic Type Pages give 404...
Talend Cloud Hybrid Data Stewardship Rules and Semantic type pages give 404 error, showing empty data. Resolution Temporary Solution Please update t... Show MoreTalend Cloud Hybrid Data Stewardship Rules and Semantic type pages give 404 error, showing empty data.
Resolution
Temporary Solution
Please update the setting in data-stewardship.properties file where <env> is the target environment: ap, eu, us
dataquality.rules.baseUri=https://tdc.<env>.cloud.talend.com/rulerepository
semanticservice.url=https://tdc.<env>.cloud.talend.com/api/v1/semanticExample
#vi data-stewardship.properties
dataquality.rules.baseUri=https://tdc.ap.cloud.talend.com/rulerepository
semanticservice.url=https://tdc.ap.cloud.talend.com/api/v1/semantic
#restart data-stewardshipThis temp solution will work for some time, please start to upgrade as soon as possible as changes/security fixes are there on the Cloud services side.
Final Resolution
Update Talend Data Stewardship to the latest version.
Cause
The root cause is due to Cloud Security update and old API deprecated. For security reasons, we updated the cloud services level with up-to-date libraries. This might have undetected side effects mainly on old on-prem/hybrid installs.
Environment
-
Qlik Talend Products: Upgrade Required for Spring Core Version in Talend Studio ...
The security team has identified that the Spring Core version is reaching its end of life. The current Talend Studio version (R2025-01) is using Sprin... Show MoreThe security team has identified that the Spring Core version is reaching its end of life. The current Talend Studio version (R2025-01) is using Spring Core 5.3.39, which needs to be updated to a higher version for compliance and security reasons.
Cause
The Spring Framework is reaching its End of Life (EOL).
Resolution
The Spring framework version update is scheduled for the February 2025 patch. Kindly apply the R2025-02 or later Studio and Runtime patches.
Environment
-
Qlik Sense Enterprise on Windows and PostgreSQL vulnerability CVE-2024-7348 (pg_...
Affected versions: Qlik Sense Enterprise on Windows all versions, including November 2024 CVE-2024-7348 is a Time-of-Check Time-of-Use (TOCTOU) ra... Show MoreAffected versions:
- Qlik Sense Enterprise on Windows all versions, including November 2024
CVE-2024-7348 is a Time-of-Check Time-of-Use (TOCTOU) race condition vulnerability in pg_dump, a utility used for backing up PostgreSQL databases. This vulnerability allows an attacker to replace a relation type (such as a table or sequence) with a view or foreign table right when pg_dump is running. Because pg_dump often runs with superuser privileges, this attack could execute arbitrary SQL code, leading to unauthorized actions or data corruption. Source: https://www.postgresql.org/support/security/CVE-2024-7348/
How does this vulnerability impact Qlik Sense Enterprise on Windows?
Qlik can confirm that pg_dump is not actively used in the Qlik Sense Enterprise on Windows code.
How to mitigate the vulnerability
Both steps are required to fully mitigate the issue.
- Upgrade PostgreSQL. This requires a standalone instance of PostgreSQL. See Upgrading and unbundling the Qlik Sense Repository Database using the Qlik PostgreSQL Installer on how to unbundle PostgreSQL if necessary.
Always verify compatibility between your Qlik Sense version and PostgreSQL before planning an upgrade.
- Delete the pg_dump.exe located in the default Qlik Sense Enterprise on Windows Postgresql install folder: C:\Program Files\Qlik\Sense\Repository\Postgresql\14\
The file will be recreated after an upgrade. This step will need to be repeated after each Qlik Sense upgrade. Qlik is actively investigating the removal of pg_dump from future installers (SHEND-2041).
The updated pg_dump.exe in, for example, C:\program files\postgresql\14 does not need to be removed.
Does the Qlik PostgreSQL Installer (QPI) use the pgdump.exe?
QPI does not utilise pgdump.exe.
Internal Investigation ID(s)
- QB-28706
- SHEND-2041
-
Qlik Talend CICD pipeline build failure : transfer jar filed per dependency reso...
Talend CICD pipeline build encounters an error: dependency resolving issue: could not transfer jar from talend-update.talend.com Cause Due to secu... Show MoreTalend CICD pipeline build encounters an error:dependency resolving issue: could not transfer jar from talend-update.talend.comCause
Due to security considerations, the proxy setting has not yet been adapted to the CICD server.
Resolution
To resolve this issue, two options can be adopted: adding proxy settings at the Operating System or Maven level, as follows.
Operating System level:
vi /etc/profile
export http_proxy=http://USERNAME:PASSOWRD@proxy-server.mycorp.com:3128/ export https_proxy=http://USERNAME:PASSOWRD@proxy-server.mycorp.com:3128/ export no_proxy=localhost,127.0.0.1,*.xxx.com
Maven level:
vi maven-setting.xml<settings> .... <proxies> <proxy> <id>example-proxy</id> <active>true</active> <protocol>http</protocol> <host>proxy.example.com</host> <port>8080</port> <username>proxyuser</username> <password>somepassword</password> <nonProxyHosts>localhost|127.0.01|*.example.com</nonProxyHosts> </proxy> </proxies> .... </settings>Related Content
Qlik Talend CICD build fails with an error: Could not resolve dependencies for project
Environment
-
A call to SSPI failed (Qlik Sense Proxy)
You may get the errors, "A call to SSPI failed, see inner exception" and "The certificate chain was issued by an authority that is not trusted". While... Show MoreYou may get the errors, "A call to SSPI failed, see inner exception" and "The certificate chain was issued by an authority that is not trusted". While they should have no impact on your end-users, you'd still like to clean them up from the logs.
Qlik Sense otherwise functions without issues.
Example error:
System.Proxy.Qlik.Sense.Communication.Communication.Tcp.StreamFactory 16 c2972806-6ae3-4559-8ebf-c7c2201335f3 xx\xxx Failed to authenticate stream as Server The client and server cannot communicate, because they do not possess a common algorithm↵↓A call to SSPI failed, see inner exception. NO-STACKTRACE↵↓ at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
These, unfortunately, are not Qlik Sense errors, but rather errors from Windows that Qlik Sense reports. You should also be able to see them in your Windows Application logs. For more information, please search out Windows Support.
See Security Support Provider Interface Architecture for additional details.
Possible root causes:- A possible root cause for Windows reporting these errors is a missing or wrong certificate thumbprint.
If a third party certificate is being used in the environment, verify that the correct thumbprint is added to the Qlik Sense Proxy. - It may also be related to the load balancer.
A common behaviour for a load balancer is a quite constant interval between two SSPI failures on Sense, generally because the basic load balances HTTPS health check doesn't complete the HTTPS handshake. The error "because they do not possess a common algorithm" is for this reason. The fast check can be done by changing the frequency of HTTP health check on the load balancer and seeing the corresponding interval change on the Qlik Sense side pay attention if multiple LB nodes are present.
- A possible root cause for Windows reporting these errors is a missing or wrong certificate thumbprint.
-
TLS and SSL Support in Qlik Sense: How to configure Qlik Sense and TLS
There are environments where the cryptographic protocols available to the Windows Operating System need to be restricted for security or compliance re... Show MoreThere are environments where the cryptographic protocols available to the Windows Operating System need to be restricted for security or compliance reasons. This article will outline where various TLS versions are supported. This article will not have full coverage of the impact of TLS changes to other software installed on the Qlik Sense server. For examples of potential impacts:
Resolution
- Full compatibility with TLS 1.2 in all current and supported versions of Qlik Sense Enterprise on Windows
- TLS 1.3 is not yet fully compatible [Internal Reference ID: SHEND-1269]
Implementation
To enable strong TLS implementation make sure to have all your servers updated to a version of both the operating system and the Qlik software, which explicitly details they support the required version of TLS.
If you have a clustered environment with multiple nodes spread across different machines, please make sure to enable the same subset of protocols on all Sense machines, otherwise the services will not be able to successfully communicate.
Using a third-party toolset
Third-party tools such as IIS Crypto can be used to enable and disable SSL or TLS. Consult your Windows administrator or network security team for what tools are usually used in your organization.
Manual
The correct protocols and ciphers can then be applied using the PowerShell (PS) scripts and making changes to the Windows Registry. Consult Microsoft or your Windows administrator for details.
Related Content
IIS Crypto is an example 3rd party tool that can be used to achieve this. IIS Crypto is not supported by Qlik, but by its respective vendor, NARTAC Software. To obtain IIS Crypto, visit https://www.nartac.com/Products/IISCrypto.
-
High Security fixes for Qlik Sense Enterprise for Windows (CVE-2024-55579 and CV...
Edited December 12th, Noon CET: updated patch versions, internal Qlik tracking reference, and added information on QB-30633; previous patches were rem... Show MoreEdited December 12th, Noon CET: updated patch versions, internal Qlik tracking reference, and added information on QB-30633; previous patches were removed from the download site
New patches have been made available and have replaced the original six releases. They include the original security fixes (CVE-2024-55579 and CVE-2024-55580) as well as QB-30633 to resolve the extension and visualization defect.
If you continue to experience issues with extensions or visualizations, see QB-30633: Visualizations and Extensions not loading after applying patch.
Executive Summary
Security issues in Qlik Sense Enterprise for Windows have been identified, and patches have been made available. If the vulnerabilities are successfully exploited, these issues could lead to a compromise of the server running the Qlik Sense software, including remote code execution (RCE).
This issue was discovered by Qlik during internal security testing and no reports of it being maliciously exploited have been received.
Affected Software
All versions of Qlik Sense Enterprise for Windows prior to and including these releases are impacted:
- May 2024 Patch 9
- February 2024 Patch 13
- November 2023 Patch 15
- August 2023 Patch 15
- May 2023 Patch 17
- February 2023 Patch 14
Severity Rating
Using the CVSS V3.1 scoring system (https://nvd.nist.gov/vuln-metrics/cvss), these issues are rated HIGH.
Vulnerability Details
(CVE-2024-55579) QB-29918, QB-29750 Remote Code Execution (RCE) via Connectors
Severity: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 8.8 (High)
Unprivileged users with network access may be able to create connection objects that trigger the execution of arbitrary EXE files on Qlik Sense Enterprise for Windows.
(CVE-2024-55580) QB-29586, QB-29864, QB-30007, QB-29802 - Broken Access Control (BAC)
Severity: CVSS:3.1/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H 7.5 (High)
Unprivileged users with network access to Qlik Sense for Windows installation may be able to execute remote commands that could cause high availability damages, including high integrity and confidentiality risks.
Resolution
Recommendation
Customers should upgrade Qlik Sense Enterprise for Windows to a version containing fixes for these issues. Fixes are available for the following versions:
- November 2024 Initial Release
- May 2024 Patch 10 or 11 (both valid)
- February 2024 Patch 14 or 15 (both valid)
- November 2023 Patch 16 or 17 (both valid)
- August 2023 Patch 16 or 17 (both valid)
- May 2023 Patch 18 or 19 (both valid)
- February 2023 Patch 15 or 16 (both valid)
All Qlik software can be downloaded from our official Qlik Download page (customer login required).
-
Qlik NPrinting Server and SharePoint as a Qlik NPrinting report destination
Question Does NPrinting have the ability to send NPrinting reports to a Microsoft Sharepoint or other worldwide web url address destination? Environme... Show MoreQuestion
Does NPrinting have the ability to send NPrinting reports to a Microsoft Sharepoint or other worldwide web url address destination?
Environment
- Qlik NPrinting: All Versions
Resolution
- It is not possible to automatically distribute Qlik NPrinting reports from an Qlik NPrinting publish task to any type of HTTP, FTP or any other worldwide web url addresspath.
- Therefore, it is not possible to send NPrinting Reports to an MS SharePoint worldwide web address.
- To workaround, it is possible to use a local or network path as defined in Distributing reports to folders
- Create a network share on the Sharepoint server and use that network folder as a destination for the distribution of your Qlik NPrinting reports.
Local and Network path examples:- Local: c:\nprinting\output
- network: \\myfileserver\files\nprinting
output
NOTE: Keep in mind that the NPrinting Scheduler service user account must have NTFS file and folder security permission to access local or network share folder destinations. It must also be in the same domain as the share point or destination server host address path or the NP service account will fail to open the network path.
*This feature is not planned nor on the NPrinting road map at this time. You can check our 'ideas' page to determine if this has been requested. You can add your request at the link below if it has not: Ideation
Related Content
- NPrinting Engine System Requirements
- Storage: Only Windows, local or shared, storage is supported.
-
Qlik Sense Enterprise on Windows: Compatibility information for third-party SSL ...
A third-party certificate was configured in the Qlik Sense Proxy, but is not being used. The connection is not private" NET::ERR_CERT_COMMON_NAME_INVA... Show MoreA third-party certificate was configured in the Qlik Sense Proxy, but is not being used.
The connection is not private" NET::ERR_CERT_COMMON_NAME_INVALID may be displayed on HUB access.
Qlik Sense Enterprise on Windows uses self-signed and self-generated certificates to protect communication between services, as well as user web traffic to the hub and management console. It is possible to use a third-party-issued SSL certificate to protect client web traffic. Using the self-signed certificate will cause a certificate warning to be displayed in the web browser (such as Google Chrome or Internet Explorer).
If the third-party certificate for the Qlik Sense Proxy Service is not fully compatible with Qlik Sense or it does not have the correct attributes and cyphers, the Qlik Sense Repository Service will revert to using the default certificates. The following error may occur in the Proxy Security logs:
Example: C:\ProgramData\Qlik\Sense\Log\Proxy\Trace\HOSTNAME_Security_Proxy.txtNo private key found for certificate 'CN=qliksense.domain.com' ([CERTIFICATE THUMBPRINT HERE]) Couldn't find a valid ssl certificate with thumbprint [CERTIFICATE THUMBPRINT HERE] Reverting to default Qlik Sense SSLCertificate Set certificate 'CN=qliksenseserver1.domain.com' ([CERTIFICATE THUMBPRINT HERE]) as SSL certificate presented to browser
Resolution:
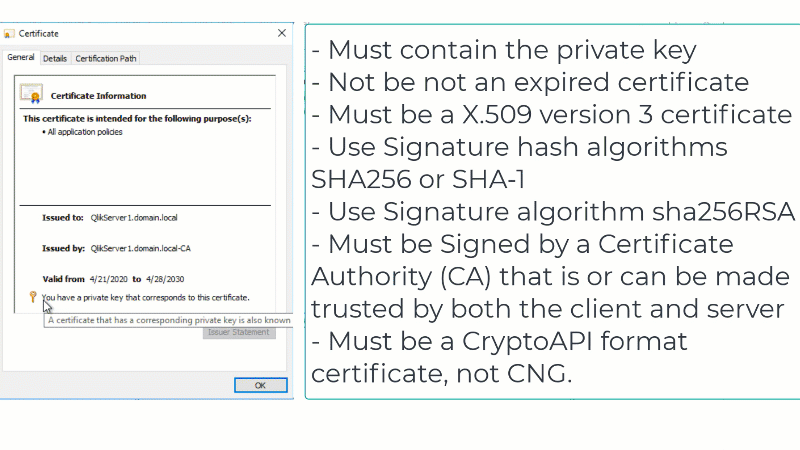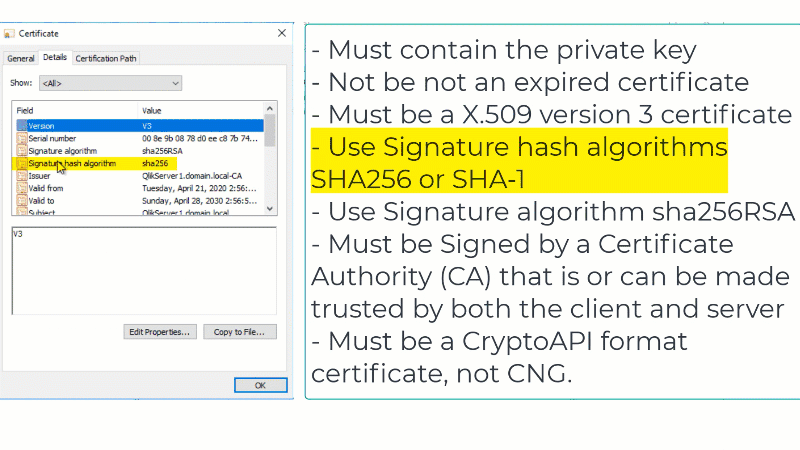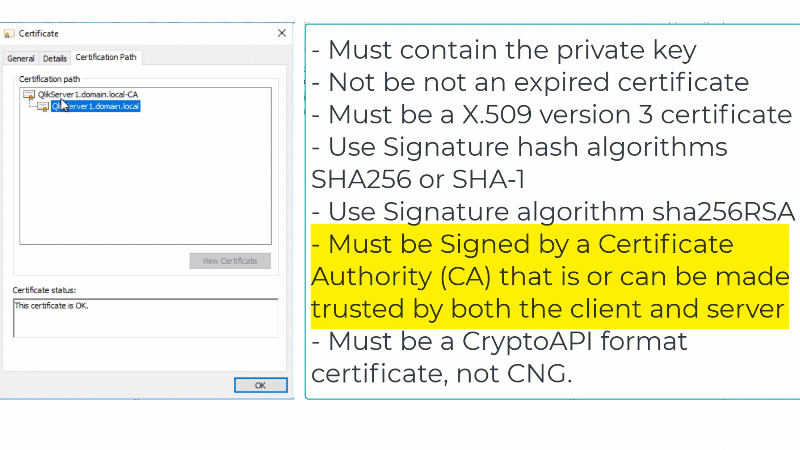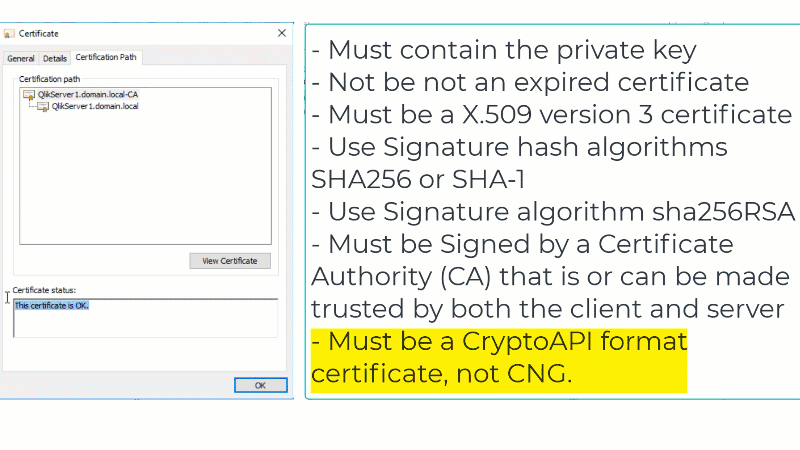
In order for Qlik Sense Enterprise to correctly recognize the third-party certificate as valid, the certificate will have to meet the following requirements:
Note: Root and Intermediate CA certificates need to be correctly installed. Should any be missing, Qlik Sense proxy will not use the server certificate and will revert back to using the self-signed certificate instead.
Certificates that are known to work well with Qlik Sense have the following attributes:- Certificates that are x509 version 3. More information including filename extensions under https://en.wikipedia.org/wiki/X.509
- Use signature algorithm sha256RSA
- Use signature hash algorithm sha256
- Signed by a valid, and OS/browser configured , CA
- Are valid according to date restrictions (valid from/valid to)
- Key in format CryptoAPI (not in CNG)
- The certificate itself has to contain private key no matter what Qlik Sense version.
Related Content:
How to: Change the certificate used by the Qlik Sense Proxy to a custom third party certificate
-
Qlik Sense on Windows: Setup Database Traffic Encryption
Disclaimer: Encrypted communication between PostgreSQL database and Qlik Sense services is a supported setup. This article provides general guidance o... Show MoreDisclaimer: Encrypted communication between PostgreSQL database and Qlik Sense services is a supported setup. This article provides general guidance on how to enable encryption on PostgreSQL database server, but local adjustment must be applied to comply with local IT requirements. Please be aware that Qlik Support can not help setting up Database Traffic Encryption, while Qlik Consulting Services may be utilized for deployment implementation.
Qlik Sense supports database traffic encryption using SSL/TLS, but it is not enabled by default. The Qlik Sense installer cannot use SSL encryption for establishing a connection to PostgreSQL. When SSL encryption is enabled, the installer does not recognize any already installed PostgreSQL databases, and as a consequence, installation cannot be completed. Password security and local IT policy around certificate need to be considered before enabling database encryption, as the implementation includes manual configuration of the Qlik Sense deployment.
Qlik recommends that the configuration in this section is performed by someone with sufficient skills in PostgreSQL database configuration.
This article covers two scenarios for enabling Database Traffic Encryption;- PostgreSQL database installed locally with the Qlik Sense installer
- Qlik Sense referred to the existing database during the installation
Upgrades: Prior to Qlik Sense Enterprise August 2022 release, the Qlik Sense installer cannot use SSL encryption for establishing a connection to PostgreSQL. So any upgrades will fail unless you are upgrading to August 2022 and later. Prior to upgrading, disable the encryption. You can enable it again after the upgrade is complete.
See Unable to upgrade Qlik Sense with missing 'SenseServices', 'QSMQ', and 'Licenses' database for respective capabilities.
Always take a complete backup of Qlik Sense deployment before altering system configuration, to allow restoring a working state in case of disaster.
These scenarios apply the default Qlik Sense signed certificate to encrypt traffic for a PostgreSQL database. Qlik Sense signed certificate is commonly only fully trusted by Qlik Sense nodes, which means other usage may not comply with local IT policies. It is recommended that a fully trusted certificate is used when applying encrypted database traffic for production environments. Consult the local IT department for details on retrieving a fully trusted certificate.Scenario 1: PostgreSQL database installed locally with the Qlik Sense installer
This scenario assumes a standard Qlik Sense installation, where the Qlik Sense Repository Database is installed on the Qlik Sense central node as part of the Qlik Sense installation.
- Complete installation of Qlik Sense Enterprise on Windows as described in Qlik Sense Help for Administrators: Installing Qlik Sense Enterprise on Windows.
- Enable encryption as described in Qlik Sense Help for Administrators: Database traffic encryption
Scenario 2: Qlik Sense referred to the existing database during the installation
This scenario assumes a custom Qlik Sense installation, where Qlik Sense is configured to use a dedicated PostgreSQL database as its Repository Database.
- Install and configure a standalone PostgreSQL database server as described in Qlik Sense Help for Administrators: Installing and configuring PostgreSQL
- Install Qlik Sense central node connected to an existing repository database as described in Qlik Sense Help for Administrators: Installing Qlik Sense on a single node
- Install Qlik Sense rim nodes if required as described in Qlik Sense Help for Administrators: Installing Qlik Sense in a multi-node site
- Enable encryption PostgreSQL database and all Qlik Sense nodes as described in Qlik Sense Help for Administrators: Database traffic encryption
-
Security scan reports the use of self signed certificates in Qlik Sense Enterpri...
This is working as designed. Qlik Sense Enterprise on Windows uses self signed certificates for service communication (Certificates | Qlik Sense for a... Show MoreThis is working as designed. Qlik Sense Enterprise on Windows uses self signed certificates for service communication (Certificates | Qlik Sense for administrators Help) and as the out-of-the-box proxy certificate.
This is not considered a security vulnerability.
If you have run a security scan and receive reports of vulnerabilities which are of concern to you, see Qlik Security Vulnerability Policy on how to report them to Qlik.
Resolution
To improve the security of your system, consider the following actions:
- How to change the certificate used by the Qlik Sense Proxy to a custom third party certificate
- How to: Redirect HTTP to HTTPS in Qlik Sense
- HTTP Strict Transport Security (HSTS) in Qlik Sense
- Configuring preferred cipher suites for Qlik License Service in Qlik Sense Enterprise on Windows
Environment
- Qlik Sense Enterprise on Windows
-
Qlik Talend Data Integration: Implementing password vaults
Problem Description Currently, Talend does not have a built-in feature allowing the integration of password vaults. Root Cause Password vaults is a ... Show More -
Qlik Replicate: JVM security configuration directory is missing
Sometimes a specific version JVM is needed rather than the shipped JVM, for example due to a known vulnerability in the JVM, the existing JVM need to ... Show MoreSometimes a specific version JVM is needed rather than the shipped JVM, for example due to a known vulnerability in the JVM, the existing JVM need to upgrade to a higher verion. However, the new jvm folder may not contain two required security configuration files, causing Replicate to generate the following warning message:
JVM security configuration directory is missing or not a directory; unable to set the Java security policy
Resolution
This warning message is reported by Replicate due to the missing of the following two security configuration files:
- java.security.default
- java.security.FIPS
To resolve this issue, you can simply copy these two files from your backup or another Replicate server into the <Replicate folder>\jvm\conf\security folder.
Internal Investigation ID(s):
#00163870
Environment
- Qlik Replicate All versions
- All supported JVM versions
-
Qlik Sense Enterprise on Windows: Securing and Hardening Server
Security of Qlik Sense Enterprise on Windows can be approached in the below discrete areas. All these areas provide different options for increasing s... Show MoreSecurity of Qlik Sense Enterprise on Windows can be approached in the below discrete areas. All these areas provide different options for increasing security in a deployment, and thereby mitigating vulnerabilities and protecting against attackers.
Content:
- 1. Authentication
- 2. Authorization
- Security Rules
- Section Access
- 3. Operating System Hardening
- Step 1: Disabling protocols and ciphers
- Step 2: Firewalls
- Step 3: Service Account Permission
- Step 4: Anti-Virus
- Step 5 (Optional): FIPS
- 4. PostgreSQL Hardening
- 5. Generalized Web Server best practices
- Apply a trusted certificate
- Optional: Additional HTTP Response Headers
Be aware that a high level of server hardening can lead to failure in your deployment. Be mindful of always having a backup to restore to in case your configuration leads to irreversible failure.
1. Authentication
Qlik Sense Enterprise on Windows supports multiple different Authentication Solutions;
- Windows (NTLM)
- Kerberos
- Ticketing
- SAML
- JWT
- Header
- Anonymous
Qlik can not specify which authentication method is appropriate for each deployment. It is advisable to review currently supported alternatives within your organization and/or Identity Provider (IdP) to implement the most suitable solution for your use case.
2. Authorization
Qlik Sense Enterprise on Windows provides two levels of native authorization in the product.
Security Rules
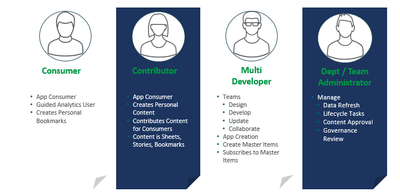
Attribute based access control (ABAC), which is configured through Qlik Sense security rules. This article will not go in depth on how to best implement security rules for your requirements, but it is highly recommended to think of your users based on the capabilities that you intend to provide them. For example different roles and capabilities as shown in image below, allows for a security rule framework to be designed and implemented. This can be done either by yourself by referencing Qlik Sense Help for Administrators and available assets or by engaging with a Qlik Consultant or Qlik Partner.
Section Access
Row level data reduction, which is configured through Section Access at Qlik Sense app level. This article will not go in depth on Section Access implementation, but with this reduction a single file can be used to hold the data for a number of users or user groups. Qlik Sense uses the information in the section access for authentication and authorization, and dynamically reduces the data, so that users only see their own data.
3. Operating System Hardening
Qlik Sense Enterprise on Windows inherits the available protocols, cipher suites, key exchanges and other security hardening which are enabled on the Windows Server operating Qlik Sense.
Step 1: Disabling protocols and ciphers
Windows Server has a lot of protocols enabled by default; however protocols, ciphers, hashes and key exchanges that are considered deprecated or not secure enough should be disabled. There are many ways of doing this, and the Windows administrator and security experts should be consulted so that local policies are accurately applied. For simplicity, understanding and a good overview IIS Crypto 3.0 can be a good tool for evaluating current Windows configuration and applying changes.
Keep in mind that "Best Practice" today might not be recommended in the near future, what was considered "safe" a while ago is not necessarily considered so today. For this reason, it is also important to regularly scan servers for potential vulnerabilities and revisit configurations as required.The Windows Server needs to be restarted for these settings changes to take effect. It is also important to ensure that all components running on the server still operate as expected after hardening is applied, for example, older non-Qlik software might not be compliant with the latest options and standards.
Step 2: Firewalls
Firewalls typically should be closed, with required ports only opened for intended purposes.
See Qlik Sense Enterprise on Windows ports overview for details on required port based on the deployed architecture.Step 3: Service Account Permission
For most organizations, local administrator rights allow for an easier deployment, but Qlik Sense Enterprise on Windows does not require local administrator rights in order to function. This can be an attractive option inside some organizations. This will require additional configuration of boot strap mode as described in Qlik Sense Enterprise on Windows Services.
For a brief overview of the rights needed by a Qlik Sense Enterprise service account:- Full control over the share used by Qlik Sense Enterprise
- Full control over the installation directory (default: C:\Program Files\Qlik)
- Full control over %ProgramData%\Qlik
- Full control over any folders used as data connections
Qlik Sense Enterprise for Windows does not officially support Group Managed Service Accounts (gMSA), but it can operate using one. The initial barrier is that the installer requires a service account and password to be entered during installation. A domain or local account could be substituted for the install stages only to be swapped out in the Windows Services applet (services.msc) after installation. Some functionality may require workarounds (e.g. A User Directory Connection to Active Directory).
Step 4: Anti-Virus
Qlik Sense Enterprise on Windows does require exceptions from anti-virus scan to avoid potential disk I/O conflicts. Refer to Qlik Sense Folder And Files To Exclude From AntiVirus Scanning for more details.
Step 5 (Optional): FIPS
Qlik Sense Enterprise on Windows can run with Federal Information Processing Standards (FIPS) enabled on the Windows Server. This does require a few adjustments of configuration files due to Qlik using non-FIPS compliant algorithms for minor tasks like hash checks. See Running Qlik Sense on Windows systems with FIPS compliance enabled for more details on Qlik Sense and FIPS.
4. PostgreSQL Hardening
Qlik Sense Enterprise on Windows uses PostgreSQL to store meta-data relating to a Qlik Sense site. In multi-node sites or sites where PostgreSQL is isolated from Qlik Sense Enterprise for Windows additional security can be applied;
- Database Traffic Encryption
- Hardening what endpoints are allowed to connect to PostgreSQL as described in PostgreSQL: postgresql.conf and pg_hba.conf explained
5. Generalized Web Server best practices
Qlik Sense Proxy service bundled with Qlik Sense Enterprise on Windows is simply a web-service. This means applying general practice guidance but in the context of Qlik Sense as described below.
Apply a trusted certificate
Qlik Sense Enterprise on Windows acts as a Certificate Authority (CA) during initial installation and signs a certificate that is applied on all encrypted traffic between Qlik Sense services. The same Qlik Sense signed certificate is applied as default certificate also for incoming connections from users accessing Qlik Sense Hub and QMC. This default certificate is not intended for production use, unless user access to Qlik Sense comes through a network load balancer or reverse proxy that trusts the Qlik Sense certificate. For direct user access to Qlik Sense Proxy, a fully trusted certificate can typically be acquired from your local IT and then applied on the Qlik Sense Proxy service.
As of July 2019, Qlik Sense Enterprise on Windows support SHA1 and SHA2 certificates. If SHA384 or SHA512 certificates are needed, then a network load balancer or reverse proxy can be configured in front of Qlik Sense which offloads to Qlik Sense.
Optional: Additional HTTP Response Headers
There are numerous HTTP response headers that can be used in attempting to secure a server. Below are a couple of the most common ones, but as always it is recommended to consult local IT and web security expert on what the recommendations are.
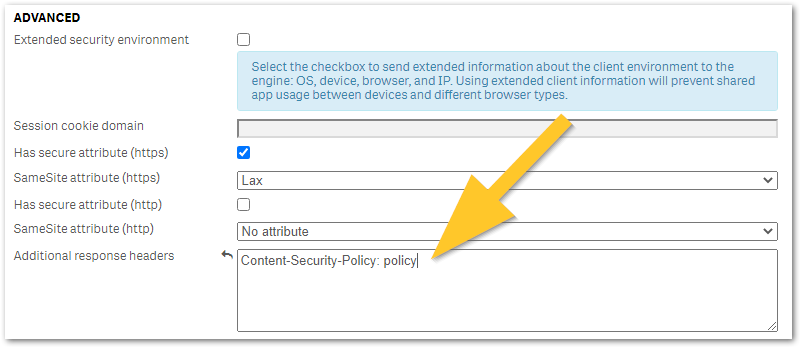
Any additional HTTP response header values can be configured in Qlik Sense Virtual Proxy settings under Additional response headers as shown in the below image and described in Qlik Sense for Administrators: Virtual Proxies. It is recommended to trial any header changes in a new virtual proxy, as poor configuration may accidentally lock you out from Qlik Sense access.
- HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security (HSTS) is an opt-in security enhancement which any web application can support through the use of a special response header. When a supported browser receives this header that browser will prevent any communication sent over HTTP in the future and will redirect all traffic over HTTPS instead. Caution is advised when implementing HSTS, as it might block HTTP access to certain pages that actually requires it or needs to be excluded from HSTS. See MDN Web Docs: Strict-Transport-Security for more details on configuration options.
- Optional: X-Content-Type-Options X-Content-Type-Options response HTTP header is a marker used by the server to indicate that the MIME types advertised in the Content-Type headers should not be changed and be followed. This allows to opt-out of MIME type sniffing.
- X-Frame-Options will prevent the site to be embedded in an iFrame, which can effective mitigate against ClickJacking attacks
- Content-Security-Policy: policy (old: X-XSS-Protection) improves security against some types of XSS (cross-site scripting) attacks.
Policy is a placeholder for your policy of choice and cannot be used as a value. See Writing a Policy (Mozilla) for examples.
-
Qlik Sense Management Console fails to open when Virtual Proxy set to Always Ano...
A virtual proxy which was configured to use Always Anonymous is not intended to be used for administration. While Qlik Sense will prompt for login whe... Show MoreA virtual proxy which was configured to use Always Anonymous is not intended to be used for administration. While Qlik Sense will prompt for login when accessing the Qlik Sense Management Console (QMC), the Management Console cannot be navigated successfully.
Beginning with November 2023, access will fail with:
An error occurred
The operation failed due to insufficient privilegesAs well as:
400
Bad RequestPrevious version of Qlik Sense may succeed with the login but not allow navigation.
Resolution
Do not use a Virtual Proxy configured to use Always Anonymous as authentication method. Always have a Virtual Proxy ready which requires authentication. For information on how to create a new Virtual Proxy, see Qlik Sense: How to create a new Virtual Proxy.
If you have locked yourself out of the Qlik Sense Management Console by modifying the only available Virtual Proxy, change the enabled authentication method directly in the Qlik Sense QSR database.
Manual steps to change the authentication method:
- Connect to the QSR using PGAdmin (see How to connect to the Qlik Sense Enterprise on Windows or Qlik NPrinting PostgreSQL database)
- Open the VirtualProxyConfig table
- In the row for your active Virtual Proxy, change the column AnonymousAccessMode value from 3 (Always Anonymous) to 0 (Requires Authentication)
- Save the changes
- Restart the database service
Cause
A secure Qlik Sense Enterprise Management Console when anonymous access is required.
Internal Investigation ID(s)
SHEND-1902
Environment
Qlik Sense November 2023 & Newer
-
Tabular Reporting events in the management console do not appear for all the use...
Issue reported Tabular Reporting events in the management console not showing for all the users in the tabular reporting recipient list Environment ... Show MoreIssue reported
Tabular Reporting events in the management console not showing for all the users in the tabular reporting recipient list
Environment
Resolution
When section access is used in a Qlik App, ensure to add all required recipients/users to the section access load script
For example, users in the Recipient import file should ideally match the users entered to the Section Access load script of the app.
This generally permits users to view management console details such as 'Events' assuming those user also have the necessary 'view' permissions in the tenant in which the app exists
Cause
If some of the recipients in the tabular reporting recipient list do not have access to the Space/App - they won't be considered in the task execution because they fail the governance.
ie: Recipients/users that are not added to the load script will not have access to the app nor associated management console events.
This is expected behavior.
Related Content
- Tabular reporting and section access
- URL to Events in your management console: https://yourtenant.us.qlikcloud.com/console/events
- Reviewing system events
-
High Severity Security fixes for Qlik Sense Enterprise for Windows (CVE-2024-360...
Executive Summary A security issue in Qlik Sense Enterprise for Windows has been identified, and patches have been made available. If successfully ex... Show MoreExecutive Summary
A security issue in Qlik Sense Enterprise for Windows has been identified, and patches have been made available. If successfully exploited, this vulnerability could lead to a compromise of the server running the Qlik Sense software, including remote code execution (RCE).
This issue was responsibly disclosed to Qlik and no reports of it being maliciously exploited have been received.
Affected Software
All versions of Qlik Sense Enterprise for Windows prior to and including these releases are impacted:
- February 2024 Patch 3
- November 2023 Patch 8
- August 2023 Patch 13
- May 2023 Patch 15
- February 2023 Patch 13
- November 2022 Patch 13
- August 2022 Patch 16
- May 2022 Patch 17
Severity Rating
Using the CVSS V3.1 scoring system (https://nvd.nist.gov/vuln-metrics/cvss), Qlik rates this severity as high.
Vulnerability Details
CVE-2024-36077(QB-26216) Privilege escalation for authenticated/anonymous user
Severity: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H 8.8 (High)
Due to improper input validation, a remote attacker with existing privileges is able to elevate them to the internal system role, which in turns allows them to execute commands on the server.
Resolution
Recommendation
Customers should upgrade Qlik Sense Enterprise for Windows to a version containing fixes for these issues. Fixes are available for the following versions:
- May 2024 Initial Release
- February 2024 Patch 4
- November 2023 Patch 9
- August 2023 Patch 14
- May 2023 Patch 16
- February 2023 Patch 14
- November 2022 Patch 14
- August 2022 Patch 17
- May 2022 Patch 18
All Qlik software can be downloaded from our official Qlik Download page (customer login required).
Credit
This issue was identified and responsibly reported to Qlik by Daniel Zajork.
Edited 20th of May 2024: Added recently assigned CVE number.
-
Qlik Talend Studio: "Clean up Libraries" check box greyed out when patching fro...
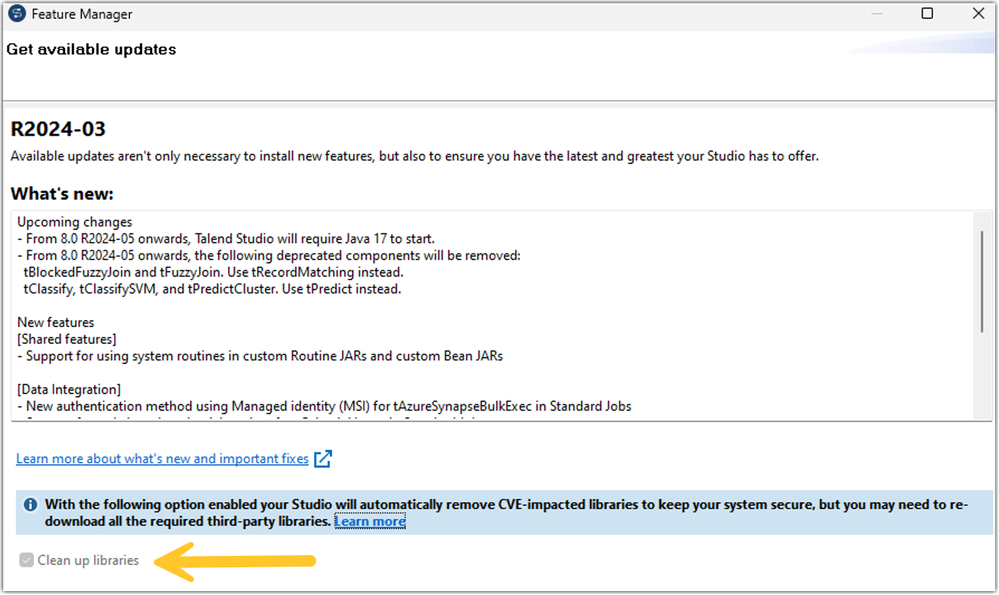
When patching Studio from the Feature manager, the Clean up libraries option is greyed out: Resolution Navigate to <Talend Studio Home>\studio\ Ba... Show MoreWhen patching Studio from the Feature manager, the Clean up libraries option is greyed out:
Resolution
- Navigate to <Talend Studio Home>\studio\
- Backup and edit Talend-Studio-win-x86_64.ini (Win OS) or Talend-Studio-macosx-cocoa.ini (Mac OS)
- Remove the following parameter -Dtalend.studio.m2.clean=true
- Save and restart Studio
Cause
The -Dtalend.studio.m2.clean=true property ensures Studio removes obsolete jars during patching.
Related Content
For more information, please review the Studio installation guide.
Environment
Talend Studio 8.0.1
-
QlikView HSTS (HTTP Strict-Transport-Security response header)
HSTS (HTTP Strict-Transport-Security response header) security check failed. HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to... Show MoreHSTS (HTTP Strict-Transport-Security response header) security check failed.
HTTP Strict Transport Security (HSTS) is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone.
Resolution
Before adding HSTS to either the QlikView AccessPoint or the QlikView Management Console (QMC), set both up to use HTTPS. See for QlikView AccessPoint and QMC with HTTPS and a custom SSL certificate instructions.
HSTS for the QlikView AccessPoint
Custom response headers can be set in both the QlikView WebServer (beginning with 12.30) and Microsoft IIS (all QlikView versions).
The custom header needed for HSTS is: Strict-Transport-Security
- Run text editor (e.g. Notepad) as Administrator
- Edit QlikView WebServer configurations file. The default path is C:\ProgramData\QlikTech\WebServer\config.xml
- Locate CustomHeaders element within the config file. For more information, see QlikView WebServer: Custom HTTP Header.
- Add custom response header as <Header> element(s) with sub-elements defining Strict-Transport-Security as the name and your desired max-age= as value.
Example:<Config> ... <Web> ... <CustomHeaders> <Header> <Name>Strict-Transport-Security</Name> <Value>max-age=31536000</Value> </Header> </CustomHeaders> </Web> </Config> - Restart QlikView WebServer service
For information on how to configure custom headers with Microsoft IIS, see Setting Custom HTTP Headers in IIS for QlikView. The site https://https.cio.gov/hsts/ gives information on how to setup the webserver to enable HSTS.
Testing can be achieved using any number of third party sites, such as:HSTS for the QlikView Management Console (QMC)
This setting was introduced with QlikView 12.70 (May 2022) SR1.
QVManagementService.exe.Config Changes:
- Stop the QlikView Management Services
- Go to ProgramFiles => qliktech => management service => open QVManagementService.exe.config using an administrator notepad
- Update this value to true =>
<add key="UseHSTS" value="true" /> - To enable HSTS to header this value has to be set to true
<add key="UseHTTPS" value="true" />
Environment:
- Run text editor (e.g. Notepad) as Administrator