Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Forums
- :
- Data Integration
- :
- Qlik
- :
- Qlik Replicate
- :
- Re: Exposure to CVE-2022-42889
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exposure to CVE-2022-42889
Hi Team,
Could you please confirm the impact of https://nvd.nist.gov/vuln/detail/CVE-2022-42889 on Qlik replicate
We are currently on version May 2021 (2021.5.0.1133)
Regards,
Vipul
- « Previous Replies
-
- 1
- 2
- Next Replies »
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @vipulmisra
The only place in QDI where apache.commons.text is used is in the Replicate Salesforce incremental-load JREP endpoint (salesforce-source-endpoint.jar). Neither Compose nor QEM use this library.
The library version currently used there is 1.9 and it is vulnerable. It should be changed to 1.10 in a future service release.
Still, even though the vulnerable JAR exists, there is no use at all of the vulnerable class StringSubstitutor which is a prerequisite to exploiting the vulnerability. Hence, from Qlik perspective, the risk of this CVE for the QDI products is zero. As usual, Qlik will update this library in a service release.
Customers who are not using that endpoint can delete the salesforce-source-endpoint.jar so it does not come up in later scans.
Thanks,
Dana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @vipulmisra
The only place in QDI where apache.commons.text is used is in the Replicate Salesforce incremental-load JREP endpoint (salesforce-source-endpoint.jar). Neither Compose nor QEM use this library.
The library version currently used there is 1.9 and it is vulnerable. It should be changed to 1.10 in a future service release.
Still, even though the vulnerable JAR exists, there is no use at all of the vulnerable class StringSubstitutor which is a prerequisite to exploiting the vulnerability. Hence, from Qlik perspective, the risk of this CVE for the QDI products is zero. As usual, Qlik will update this library in a service release.
Customers who are not using that endpoint can delete the salesforce-source-endpoint.jar so it does not come up in later scans.
Thanks,
Dana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Dana_Baldwin ,
We are using Replicate version 2021.5.0.1272 and QEM version May 2021 (2021.5.0.543). Could you please check and confirm is this version replicate and QEM affected with this security vulnerability CVE-2022-42889.
The end-points were are using are ;
source - Oracle and DB2 iSeries
target - Oracle.
Thanks,
Adersh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @adershb
As noted above, the only place in QDI where apache.commons.text is used is in the Replicate Salesforce incremental-load JREP endpoint (salesforce-source-endpoint.jar). Neither Compose nor QEM use this library.
Version 2021.5 uses the vulnerable version and it will be changed to 1.10 in a future service release of 2022.5 or later.
Still, even though the vulnerable JAR exists, there is no use at all of the vulnerable class StringSubstitutor which is a prerequisite to exploiting the vulnerability. Hence, from Qlik perspective, the risk of this CVE for the QDI products is zero. As usual, Qlik will update this library in a service release.
If you are not using Salesforce incremental load endpoint, you can delete the salesforce-source-endpoint.jar so it does not come up in later scans.
Thanks,
Dana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @Dana_Baldwin
Where is the location of salesforce-source-endpoint.jar file. You mean on Replicate server or on QEM server?
Thanks,
Adersh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @adershb
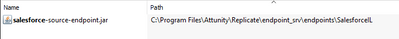
It is on the Replicate server, as noted QEM does not use this library. It is here:
Thanks,
Dana
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dana_Baldwin ,
I could see file arep-salesforce.jar in below location. Our Replicate server is Linux.
replicate-2021.5.0-1272/endpoint_srv/endpoints/Salesforce $
Thanks,
Adersh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dana_Baldwin ,
Can you please confirm is it the same vulnerable file (mentioned above on Linux) and If so, for removing it, do we need to restart the replicate service on Linux (stop, remove .jar file and start).
Thanks,
Adersh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Dana_Baldwin , we also see the same file arep-salesforce.jar in the Attunity/Replicate/endpoint_srv/endpoints/Salesforce folder
No other files.
Could you please confirm if this is the affected file?
Regards,
Vipul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- « Previous Replies
-
- 1
- 2
- Next Replies »