Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik coverage for June 2021 CVE-2021-1675 and CVE-...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik coverage for June 2021 CVE-2021-1675 and CVE-2021-34527 PrintNightmare vulnerabilities
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik coverage for June 2021 CVE-2021-1675 and CVE-2021-34527 PrintNightmare vulnerabilities
Jul 20, 2021 7:13:02 AM
Jul 20, 2021 7:04:43 AM
IMPORTANT: As of July 6, 2021, Microsoft has released KB5005010, an out-of-band update to address CVE-2021-34257 Remote Code Execution. This update allows organizations to restrict Print Driver installation to Administrator groups exclusively. Qlik recommends customers apply this update as soon as possible.
This is Windows related Security hardening and vulnerability, we recommend you to once check with your Antivirus vendor to provide you a Signature file or their recommendations.
For more information, see the Microsoft update release article at: KB5005010 - Restricting installation of new printer drivers after applying the July 6, 2021 updates.
Qlik is aware of CVE-2021-1675, CVE-2021-34527, and related publicized "proof of concept" code, collectively known as "PrintNightmare." In response to the identified vulnerability, Qlik has generated an Antivirus Rule that can prevent exploitation and allow monitoring of this vulnerability. This rule detects when files are written from the spool service into the directory that known exploits are using to drop files on victim systems.
In addition to the Antivirus Rule, you can disable the print spooler as a mitigation effort. Qlik recommends disabling the print spooler as a standard security practice when not in use on infrastructure systems to reduce risk in your environment.
Environment:
Qlik Sense Enterprise on Windows
QlikView
Qlik NPrinting
Workaround:
Product: Antivirus Access Protection rule (Any version and any antivirus product use the below syntax)
The following Access Protection rules can be implemented to mitigate exploit behavior by preventing write access to the directories used be the technique by the Print Spooler.
NOTE: When creating a user-defined Access Protection rule in Antivirus, an asterisk (*) is pre-populated in Processes to include and must be removed and replaced with spoolsv.exe. It is recommended that the rule be thoroughly tested to ensure integrity and ensure there are no application conflicts.
|
New rule type |
File/Folder Blocking Rule |
|
Rule Name: |
Block new files from being created or written to by Spoolsv.exe in OLD drivers directory |
|
Processes to include: |
Spoolsv.exe |
|
Processes to exclude |
<blank> |
|
File or folder name to block: |
%systemroot%\System32\spool\drivers\**\Old\* |
|
File actions to prevent: |
Write access to files New files from being created |
|
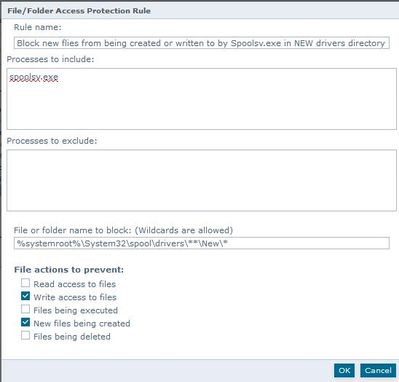
New rule type |
File/Folder Blocking Rule |
|
Rule Name: |
Block new files from being created or written to by Spoolsv.exe in NEW drivers directory |
|
Processes to include: |
Spoolsv.exe |
|
Processes to exclude |
<blank> |
|
File or folder name to block: |
%systemroot%\System32\spool\drivers\**\New\* |
|
File actions to prevent: |
Write access to files New files from being created |
Product: Host Intrusion Prevention (HIPs)
The following rule can be used to block spoolsv.exe from creating files in the paths used by the technique:
NOTE: It is recommended that the rule be thoroughly tested to ensure integrity and ensure there are no application conflicts.
Rule {
tag PrintNightmare_Custom_Rule
Class Files
Id 4001
level 4
attributes -v
files { Include "*\\System32\\spool\\drivers\\*\\New\\&.dll" "*\\System32\\spool\\drivers\\*\\Old\\&\\&.dll" }
Executable { Include { -path "*\\spoolsv.exe" } }
user_name { Include "*" }
directives files:create
}
Additional Recommendations:
To disable PrintSpooler through Group Policy Objects (Recommended for servers, except dedicated print servers):
NOTE: Disabling the print spooler service disables the ability to print both locally and remotely.
- To manage this setting, modify your Global Policy Object (GPO) or create a GPO.
- When you edit the GPO, go to Computer Configuration, Policies, Windows Settings, System Services, Print Spooler.
- Right-click the Print Spooler System Service option and select Properties.
- Set the System Service to Disabled.
To block only the remote attack vector, administrators can disable inbound remote printing through Group Policy Objects (Recommended for workstations):
- To manage this setting, modify your Global Policy Object (GPO) or create a GPO.
- When you edit the GPO, go to Computer Configuration, Administrative Templates, Printers.
- Right-click the Allow Print Spooler to accept client connections policy option and select Edit.
- Set the policy to Disabled.
Related Information: