Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How to enable Data Encryption In Qlik Sense Enterp...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to enable Data Encryption In Qlik Sense Enterprise On Windows
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to enable Data Encryption In Qlik Sense Enterprise On Windows
Aug 28, 2024 3:48:58 AM
Nov 7, 2019 10:11:54 PM
Qlik Sense allows for Data Encryption for Qlik Sense Apps (QVF) and Data (QVD) Files.
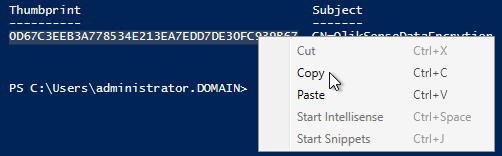
Qlik Sense Engine can encrypt data by using a data encryption key (DEK), which is generated from a certificate-based key encryption key (KEK). The DEK is unique to each encrypted file and is stored alongside the encrypted data (inside the QVF and QVD files) in an encrypted format using RSA. The industry standard AES-256 GCM is used as the data encryption algorithm. Decryption requires access to the same certificate as used during encryption, which mean that the KEK certificate thumbprint in the certificate store must match the thumbprint used for the DEK generation.
Instructions
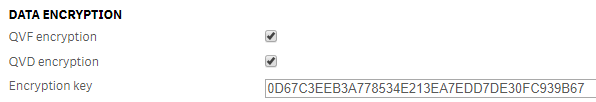
Data encryption can be enabled in the Service Cluster configuration of the Qlik Sense Management Console. See the Online Help at Qlik Sense Enterprise on Windows > Administer Qlik Sense Enterprise on Windows > Managing a Qlik Sense Enterprise on Windows site > QMC resources overview > Service cluster > Data encryption
Detailed Instructions with Example
This is a simple example of how to explore data encryption in Qlik Sense Enterprise on Windows.
- Create a new sample app, like the attached ascii-table.qvf
- Add a simple script to generate an ASCII table
ASCII: Load if(RecNo()>=65 and RecNo()<=90,RecNo()-64) as Num, Chr(RecNo()) as AsciiAlpha, RecNo() as AsciiNum autogenerate 255 Where (RecNo()>=32 and RecNo()<=126) or RecNo()>=160 ;
- Create a folder connection to a folder where the QVD can be written
- Generate QVD of a data table. Note, change the lib:// reference to match a valid data connection
STORE ASCII INTO [lib://MyData (domain_administrator)/ascii.qvd] (QVD);
- Add a simple script to generate an ASCII table
- Reload the app
- Copy the app and qvd files to allow comparison after enabling encryption
- Default app location: C:\ProgramData\Qlik\Sense\Apps
- The QVD location is per the app's folder data connection path
- Create a certificate to test, following Encryption Certificates.
- Run Powershell as the Qlik Sense service account or log in to Windows as the Qlik Sense service account.
Doing this with the correct account is crucial to make the generated certificate available to the service account.
- Generate a self-signed certificate to use as an encryption key
Windows Server 2016
New-SelfSignedCertificate -Subject "QlikSenseDataEncrytion" ` -KeyAlgorithm RSA ` -KeyLength 4096 ` -Provider "Microsoft Software Key Storage Provider" ` -KeyExportPolicy ExportableEncrypted ` -CertStoreLocation "cert:\CurrentUser\My"
Windows Server 2012 R2
New-SelfSignedCertificate -DnsName "QlikSenseDataEncrytion" ` -CertStoreLocation "cert:\CurrentUser\My" - Validate that cert is available
- Run Powershell as the Qlik Sense service account or log in to Windows as the Qlik Sense service account.
- Get the cert thumbprint from generation result. This thumbprint can be used as key-encryption key (KEK) by Qlik Sense.
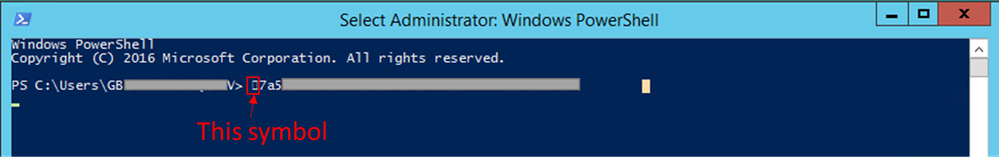
Note: When copying the certificate thumbprint, an invisible character may be added at the beginning of the certificate thumbprint. Verify the thumbprint before executing the command in PowerShell: - Enable encryption in Service Cluster settings per Data Encryption
- Restart Qlik Sense Engine service
- Reload the app to generate data encryption keys (DEK) for encrypted QVF and QVD files.
Disable Encryption
Files remain encrypted after disabling encryption until the next following app reload or QVD generation.
- Disable encryption in QMC > Service Cluster
- Uncheck both encryption options
- Remove encryption key
- Restart Qlik Sense Engine Service on all nodes
- Complete a full successful app reload cycle, including QVD generators
- All QVF files have been decrypted
- All QVD files have been decrypted
File Comparison
Compare the unencrypted and encrypted files to validate successful encryption
Qlik Sense app (.qvf) file is a binary file, which makes it harder to visually confirm the encryption effect.
Encrypted app files have multiple references to ciphertext, which in turn refers to secrets used for the encryption.
App file without encryption has no such references. The cypher text portion of QVF represents the data encryption key (DEK) used to encrypt the app data and bookmarks.
Encrypted data (.qvd) files has "Encryption Info" defined, which includes the data encryption (DEK) references.
Data part is also significantly different, even though both version have exactly the same static data content.
Encryption Scope
- Encryption only applies at rest, meaning when stored on disk.
- Data in memory is not encrypted
- Exported app (QVF) file is not encrypted
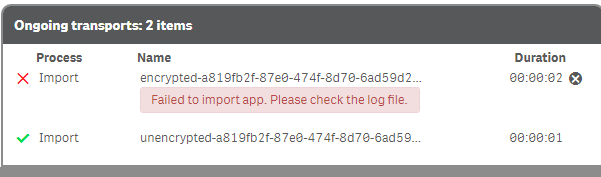
- Encrypted file (from apps storage folder) can not be imported in an other Qlik Sense instance.
The import fails as the importing server is unable to parse the encrypted file.
Related Content:
Qlik Sense on Windows: Data Encryption Key Rotation
Using Server Certificates for Data Encryption
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@ToniKautto what do you mean by "a user needs access to the cert used for encrypting the file" to decrypt it?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@ToniKautto so as long as the app is on the server where it was encrypted any developer is able to open it and work on it normally
but if this app is copied from where it is saved (folder location) and a user tries to import it to another server the import will fail
so I assume that encryption is not intended to prevent a group of user from working on the app on the server where it was encrypted
another question if this encrypted app was duplicated, will the duplicate copy be encrypted too?
if I publish the duplicated app and replace the encrypted one, what will happen?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@ali_hijazi encryption in this case protects a file at rest. As you can see in the post and related help pages, the encryption is certificate-based, so if someone copies a file, they can not decrypt it without access to the same certificate.
Encryption of a file is unrelated to authorization or user access to the product; these are two different concepts.
As you can see in the documentation, encryption is enabled at the service cluster level; it affects all QVF and QVD files that are written in the deployment. A duplicate app is a new QVF; hence, it will be encrypted at creation.
My suggestion is that you validate some of your use cases and concerns by following the post and the documentation. Enable encryption, and verify that files are encrypted in storage. Duplicate and publish apps, while verifying that encryption remains on he created, updates files.
- « Previous
-
- 1
- 2
- Next »