Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Missing SameSite attribute blocks requests in Chro...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Missing SameSite attribute blocks requests in Chrome 80 and later - Too many sessions in parallel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Missing SameSite attribute blocks requests in Chrome 80 and later - Too many sessions in parallel
Nov 6, 2020 8:19:45 AM
Jan 10, 2020 4:15:57 AM
Working with Qlik Sense in mashups or other integrations such as Sharepoint can lead to issues with a SameSite attribute.
Qlik Sense will show the error:
You cannot access Qlik Sense because you have too many sessions active in parallel
The error seen in Chrome is:
"A cookie associated with a cross-site resource at ....[URL]... was set without the `SameSite` attribute. It has been blocked, as Chrome now only delivers cookies with cross-site requests if they are set with `SameSite=None` and `Secure`. You can review cookies in developer tools under Application>Storage>Cookies and see more details at https://www.chromestatus.com/feature/5088147346030592 and https://www.chromestatus.com/feature/5633521622188032."
Even though this comes from the Chrome console, other browsers as Mozilla and Edge are also displaying similar warnings. Is there a way around this error?
Also see Community post Cross-Site requests with cookies without the SameSite attribute are being blocked by Google Chrome
NOTE: This issue does not impact NPrinting and no NPrinting patches are required
Environment:
- Qlik Sense Enterprise
- QlikView Server
- Browsers enforcing the new CORS security standard.
Cause:
This is a new CORS security standard/feature that browsers are now enforcing, or beginning to enforce as developers begin to opt in. More information is available here https://www.chromestatus.com/feature/5088147346030592 and here https://www.chromestatus.com/feature/5633521622188032 as the above error mentions.
Product Defect ID(s):
- QB-682
- QV-19466
Resolution
The issue has been fixed by setting the attribute SameSite=None. It is possible to change the SameSiteAttribute values if needed as described below.
Note! Please review the list of Patches from which Qlik has made the changes possible.
Qlik Sense April 2020 and later
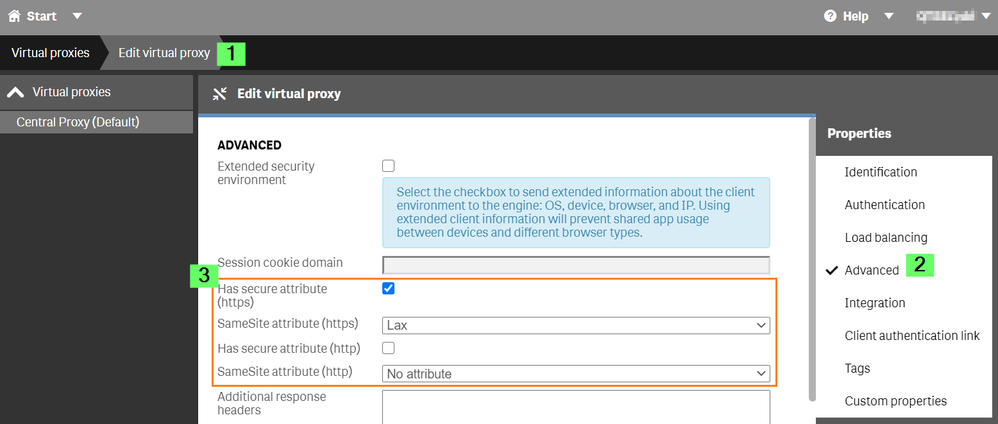
The SameSite attribute is set directly in the GUI of the Virtual Proxy settings.
- Open the Qlik Sense Management Console
- In the leftmost menu locate Virtual Proxies
- Open the available list and select the Virtual Proxy you wish to edit
- Click Edit (or double click)
- In the rightmost menu, select Advanced
- Scroll down to locate the SameSite attributes.
Pictured in Image 1 are the default values for Qlik Sense September 2020. - Depending on your implementation, set the SameSite attribute to None.
See SameSite attribute values on Help.qlik.com for details on the available values.
Note: If you are changing the SameSite Attribute to None, ensure that Has Secure Attribute (https) remains checked - Press Apply
Previous versions of Qlik Sense
Available from the following Patches:
Qlik Sense February 2020
Qlik Sense November 2018 Patch 8 Update 1
Qlik Sense February 2019 Patch 7
Qlik Sense April 2019 Patch 7
Qlik Sense June 2019 Patch 10
Qlik Sense September 2019 Patch 6
Qlik Sense November 2019 Patch 5
The default behavior for https is to set SameSite=None. The default behavior for http is not to set SameSite attribute, neither the Secure attribute, just like it was before this change. Other behaviors can be configured. This change is available in all patches listed above. By default above applies. If you wish to configure other values, do the following:
1. Open the Proxy.exe.config file, which by default is located in "C:\Program Files\Qlik\Sense\Proxy".
2. Add following strings in the section <appSettings> with the desired values, in example:
<add key="SessionCookieSettings.Https.HasSecureAttribute" value="true"/>
<add key="SessionCookieSettings.Https.SameSiteAttribute" value="None"/> <!-- Valid values are NoAttribute, None, Lax and Strict -->
<add key="SessionCookieSettings.Http.HasSecureAttribute" value="false"/>
<add key="SessionCookieSettings.Http.SameSiteAttribute" value="None"/> <!-- Valid values are NoAttribute, None, Lax and Strict -->
3. Restart Qlik Sense Proxy Service.
4. Repeat above actions on each node of the cluster running the Qlik Sense Proxy Service.
Workaround(s):
- If you are using Chrome versions 79 and below, the default setting for SameSite is "default", which is equivalent to "disabled". You can check it here chrome://flags/#same-site-by-default-cookies. In Chrome versions 80 and newer, "default" will be equivalent to "enabled", which enforces this security setting and will require an update to Qlik Sense to prevent requests from being blocked. The update is provided on the versions documented here under the "Fixed Version" sections. Otherwise as a workaround the SameSite setting can be set to "disabled".
- Edit the domain policy for where a list of specific domains are allowed for the legacy SameSite behavior to be used. See Cookie Legacy SameSite Policies.
NOTE:
- Qlik will have official patches available on the patch Wednesdays delivery – Feb 12th 2020.
- Licensee patches will be available on demand as of Feb 3rd 2020, please contact support@qlik.com.
The fix does have some limitations, bugs in older browsers can cause the following:
| Browser | Bug | Effect |
| Chrome 51-66 Android releases before 12.13.2 |
SameSite=None cookies are rejected | External mashups will not work |
| Safari on MacOS 10.14 All browsers on iOS 12 |
SameSite=None is treated as SameSite=Strict |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Sonja and thank you very much for this article.
When you mentioned fixed version, what do you mean exactly ? does it mean that it is mandatory to upgrade in order to change thoses properties or doest it concern only the possibility to change properties directly in the qmc ?
For example, in a June 2018 Patch 1 version, is it possible to change Proxy.exe.config file ?
Best regards.
Johann
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Prior to upgrading our platform to the latest version of Qlik, we are looking for a quick fix for our April 2017 version of the software for the SameSite cookie attribute.
Can you confirm what requirement would be required if possible to address this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Sonja_Bauernfeind
Thanks for your response.
I understand the workarounds for Chrome, however, we have a couple thousands of users, across an array of different organisations around the world, on our Qlik instance where asking the users to individually update their browser settings for Chrome and other browsers, that are also effected, and negate any company wide user directory settings their IT departments might force is highly unachievable.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@unknownb An upgrade will be required in that case if you wish to make use of the settings introduced in the fixed versions.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Team,
After setting SameSite=None in chrome browser, I am getting the result from Qlik to my application. But I am not able to get the output for my Qlik extension.
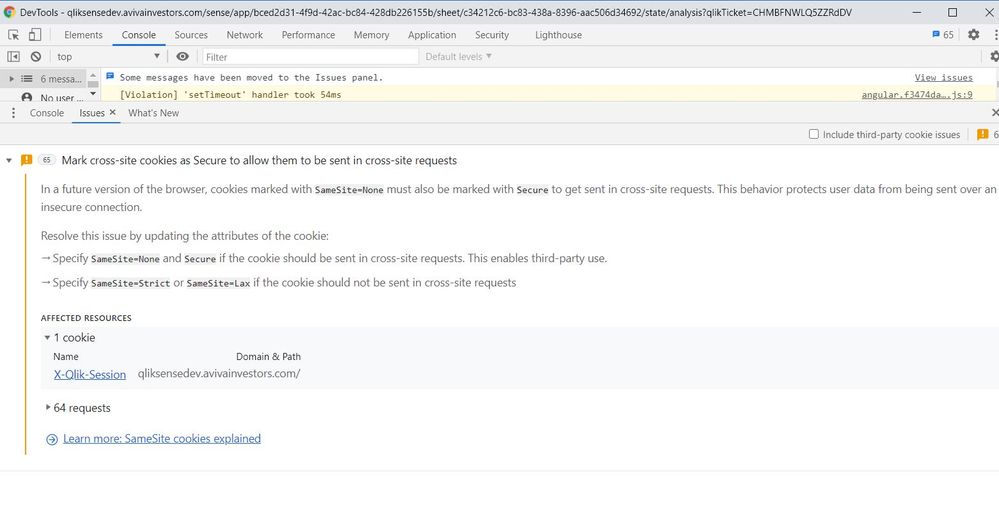
I am getting the following warning message "mark cross-site cookies as secure to allow them to be sent in cross-site request" (Please find the attachment).
Please guide me to fix this issue
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi @hshahul04 have you solved this issue yet?
I believe you have to check the attributes "Has Secure Attribute (https)" in order for it to work.
Now I do wonder, since this requires the web app to be hosted on https, how does one allow using it on http for development purposes?
Or we should only use SameSite = None and host the web app on https?