Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Forums
- :
- Analytics
- :
- New to Qlik Analytics
- :
- SSL Labs: Grade F for Qlik Sense Server
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSL Labs: Grade F for Qlik Sense Server
Hi,
I check our new Qlik Sense Server with SSL Labs and got the Grade F.
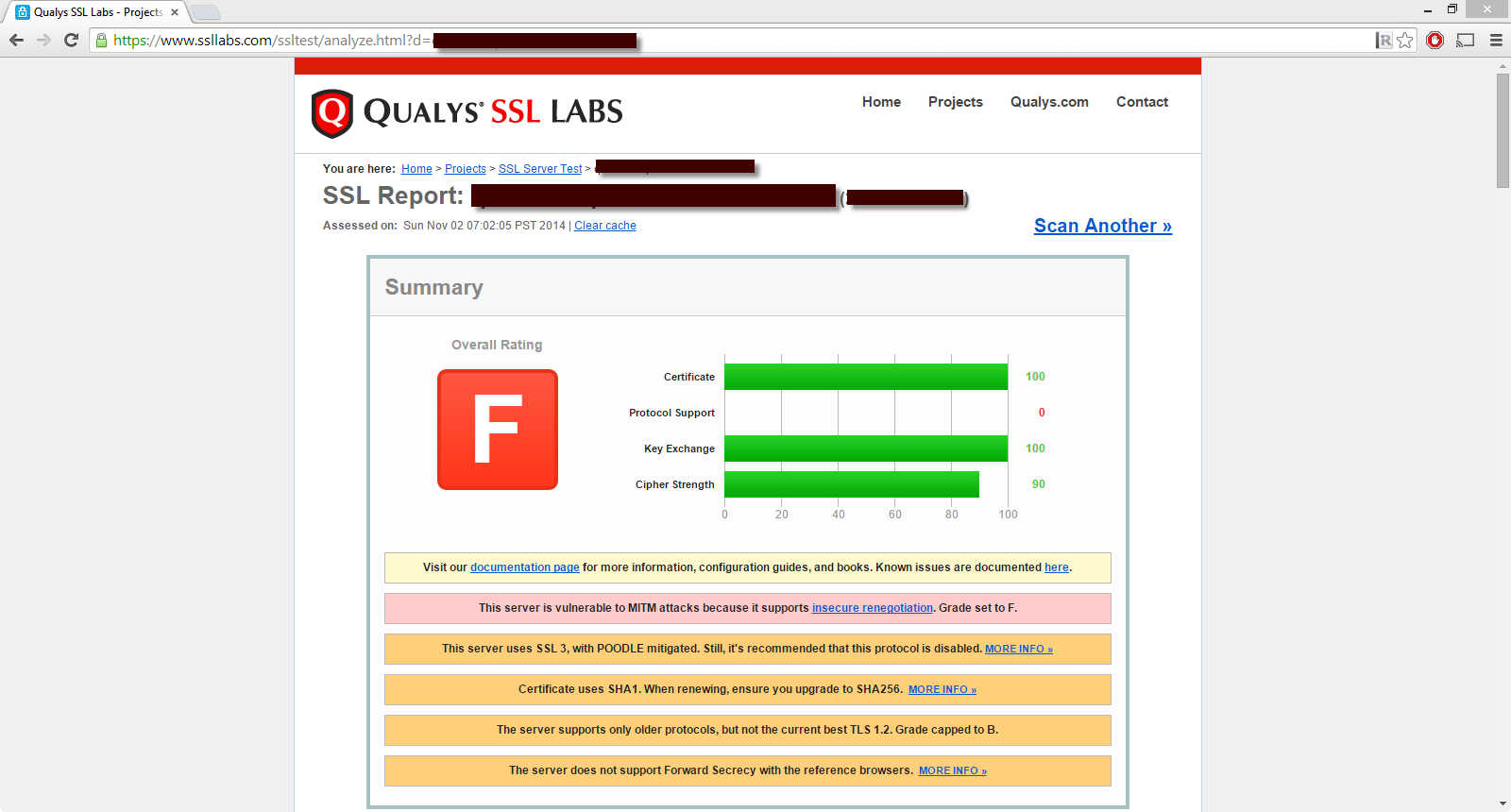
I order to be secure again the POODLE attack, I need to disable SSL 3. It's also recommanded to enable TLS 1.2, which is disabled and Forward secrecy. How to do that? There are no options regarding that in the QMC, only the SSL Cert Thumbprint.
- « Previous Replies
- Next Replies »
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
As Fredrik pointed out, future updates will support TLS 1.2.
As a side-note, one mitigation option stated on the page you're referring to, is to disable renegotiation. This can be done as well, on OS level by adding the following registry key:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
"DisableRenegoOnServer"=dword:00000001
You need to test this thoroughly in your environment for any side effects as it may affect functionality in other software.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
Disabling SSL 3.0 needs to be done on OS level.
See Microsoft Security Advisory 3009008 for more instructions on how to do this.
Best,
Bjorn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Björn,
I applied the Security Advisory to our server. SSLv3 is off and Perfect Forward Secrecy is on, but still got an Grade F. There was an Authentication Gap Vulnerability discovered (https://community.qualys.com/blogs/securitylabs/2009/11/05/ssl-and-tls-authentication-gap-vulnerabil...) and TLS 1.2 is off, although the Server OS WIndows Server 2012 R2 supports that. What can I do to fix that?
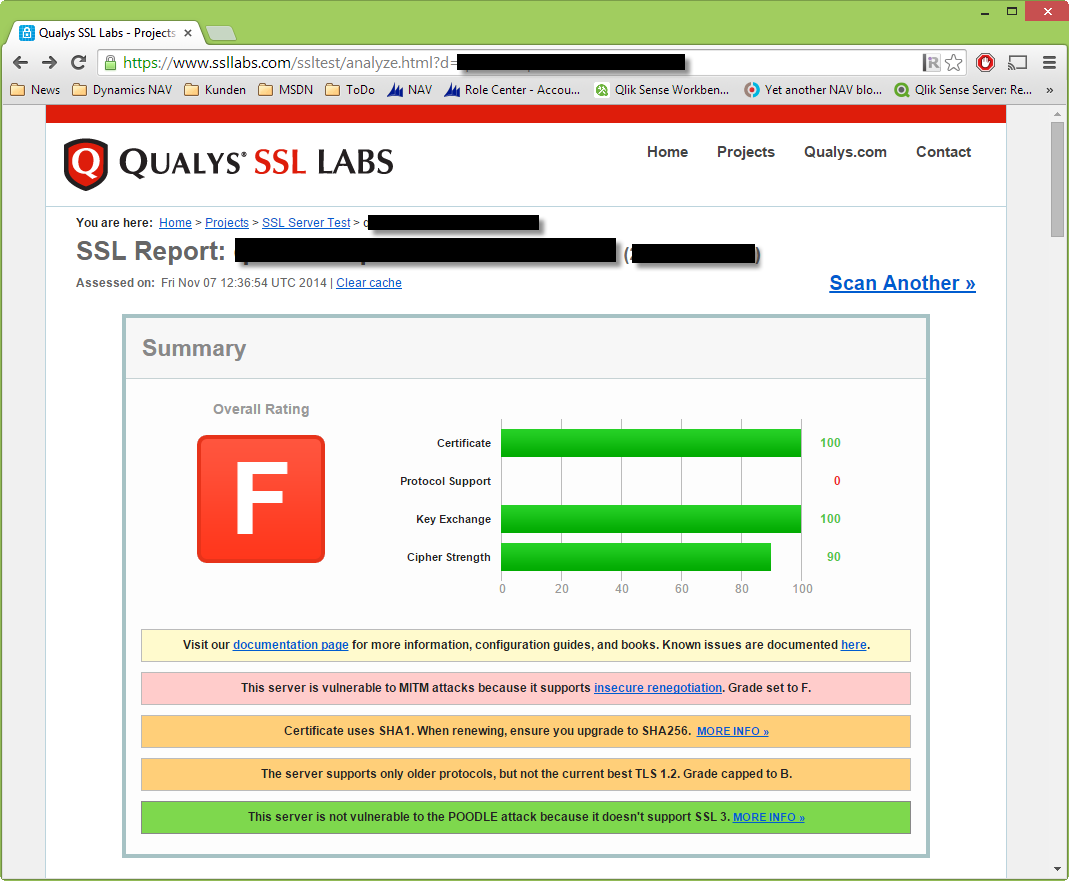
Best regards,
Daniel Göhler
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Daniel,
Current versions of Qlik Sense uses version 4 of the dot net framework that only support up to TLS 1.0. Futures updates of Sense will be upgraded to version 4.5 which supports TLS 1.2
The description you forwarded state that this vulnerability is only critical in combination with CSRF weaknesses.
Qlik Sense has proven protection against CSRF that has been validated by external security tests several times during the development of Qlik Sense.
At Qlik we take security extremely seriously and value feedback from our customers.
Fredrik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
As Fredrik pointed out, future updates will support TLS 1.2.
As a side-note, one mitigation option stated on the page you're referring to, is to disable renegotiation. This can be done as well, on OS level by adding the following registry key:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
"DisableRenegoOnServer"=dword:00000001
You need to test this thoroughly in your environment for any side effects as it may affect functionality in other software.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Björn,
you suggestion didn't change a thing.
Best regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Has this been addressed by Qlik? My Qlik Server still seems to be using TLS1.0, amongst a whole list of other obsolete cryptographic technologies.
When you say
Futures updates of Sense will be upgraded to version 4.5 which supports TLS 1.2
can you be more specific please? Your post was made over 1 year ago, and the situation still seems to be the same.
Furthermore, I cannot find a single official acknowledgement or support path by Qliktech that addresses the use of completely unsuitable security measures.
What gives?!!
dgoehler, what have you done since about you SSLLabs "F Grade"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Darren,
please notice that this web test gives you an indication of potential problems. My assumption here is that the result and analysis is based on what the webserver finds in the communication and handshake done with your client. This tool would not actually execute a attack to confirm if it can be done or not, so if you mitigate the risk of an attack the tool would still consider that you are in the risk zone.
The MITM attack related to insecure renegotiation is the F grade indicator, which can be mitigated by disabling renegotiation as mentioned previously in this thread. This is something that needs to be done the OS level by adding the below Windows registry key.
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
"DisableRenegoOnServer"=dword:00000001
IMPORTANT: Any changes at the OS level must be thoroughly tested as they may cause other software to no longer function as expected, or clients may be unable to communicate with the server. If any side effects are experienced, the changes should be reverted back to the original settings.
TLS 1.2 support is targeted for the next service (2.0.7) and feature (2.2) release.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm next feature release (2.2) does in fact support TLS 1.2.
Tested on hardened Windows 2012 R2 and I got confirmed a Grade A on SSL Labs test page.
For more information about when (soon) Qlik Sense 2.2 will be available, keep an eye on Qlik Support Updates
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
Did you figure out a way to work around the insecure renegotiation? We are running into the same issue, and some of our customers are not able to access the Qlik charts and graphs in our mashup because of it. We are wondering if you found a way to successfully disable insecure renegotiation on the Windows/OS level.
Thanks,
Grace
- « Previous Replies
- Next Replies »