- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
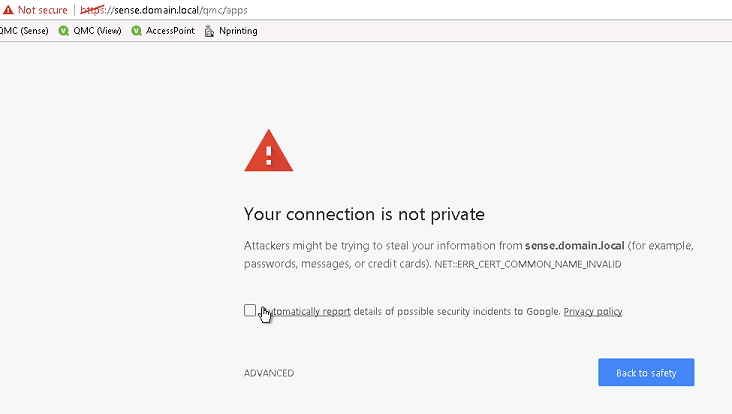
Chrome 58+ and SSL Certificates - Your connection is not private
May 7, 2021 10:27:34 AM
Apr 20, 2017 8:40:46 AM
Google Chrome 58 and higher displays a “Your connection is not private” warning when accessing Qlik Sense Hub or QMC. Accessing the same Qlik Sens site through another browser or older version of Google Chrome work without any problem.
The same issue might be seen also for other non Qlik related HTTPS URLs.
Environment:
Qlik Sense Enterprise on Windows
Resolution
The issue can be resolved differently depending on the Qlik Sense version and certificate authority in use. A temporary solution can be to ignore the browser warning, or to use another browser. Permanent solutions depend on current version of Qlik Sense.
3rd party certificates
Qlik Sense sites that use 3rd party certificates, have to be updated by acquiring an updated certificate from the certificate provider. Please consult local IT team for more guidance on how to apply a certificate update.
Qlik Sense Standard self signed certificates
Certificates self-signed by Qlik Sense do not contain the “Subject Alternative Name” attribute. A possible solution is to configure Google Chrome to allow certificates issued by local trust anchors that are missing the subjectAlternativeName, which can be done by setting HKEY_CURRENT_USER\Software\Policies\Google\Chrome\ EnableCommonNameFallbackForLocalAnchors= dword :1 in Windows Registry.
CAUTION: Changes to Windows registry can lead to severe system problems if not applied accurately.
See attached .reg file as reference to applying EnableCommonNameFallbackForLocalAnchors in Windows registry.
Cause
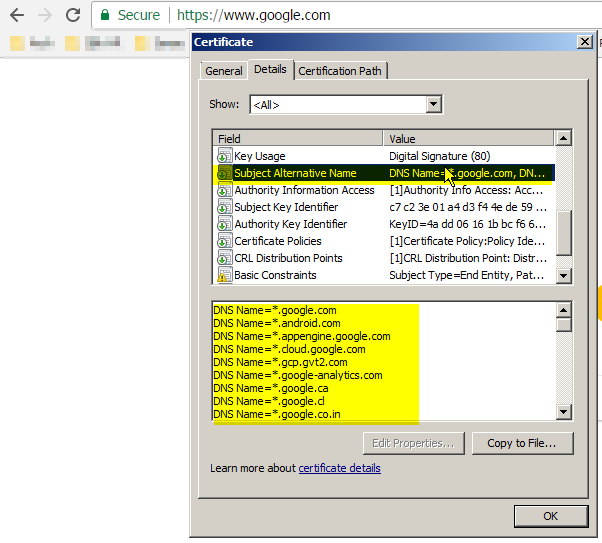
This issue is caused by Google Chrome 58 (and later) requiring “Subject Alternative Name” attribute including “DNS Name” value. See Google Chrome issues 308330 as reference;
https://bugs.chromium.org/p/chromium/issues/detail?id=308330
RFC6125 (https://tools.ietf.org/html/rfc6125) definition of “Subject Alternative Name”;
If a subjectAltName extension of type dNSName is present, that MUST
be used as the identity. Otherwise, the (most specific) Common Name
field in the Subject field of the certificate MUST be used. Although
the use of the Common Name is existing practice, it is deprecated and
Certification Authorities are encouraged to use the dNSName instead.
This is an example of a certificate that will work without issue in Chrome 58 or higher, note the highlighted portions: