Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Enabling App Distribution after an Upgrade of a Mu...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Enabling App Distribution after an Upgrade of a Multi-cloud Setup (September 2020)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Enabling App Distribution after an Upgrade of a Multi-cloud Setup (September 2020)
Sep 2, 2022 9:20:46 AM
Dec 8, 2020 3:51:11 AM
IMPORTANT NOTE: The following steps are applicable for Qlik Sense multi-node and Multi-cloud deployments using app distribution that have been upgraded to September 2020 release (or later) from versions prior to the September 2020 release.
This does not apply to:
- Qlik Sense Single Node deployments
- Qlik Sense Single Node deployments using app distribution to Qlik Sense SaaS
- Qlik Sense Multi-node deployment not using app distribution to Qlik Sense SaaS
For those three, follow the standard Upgrade Instructions (Source: Qlik Help).
Note that if you have a single node deployment that uses app distribution, you have one additional step to perform after following standard upgrade instructions. You will be required to recreate the identity provider in QCS tenant for QSEfW setup. This is required because the local bearer token for cloud deployment is recreated using a new certificate after QSEfW has been upgraded to September 2020 release or later.
Related Articles
Steps to perform after an upgrade to configure app distribution in a multi-node site
- Stop all services on NON-CENTRAL NODES in the Qlik Sense cluster.
- Back up all current Qlik Sense certificates from the NON-CENTRAL NODE by following the steps mentioned in Backing up certificates help section.
- Remove all current Qlik Sense certificates from NON-CENTRAL NODES by executing the following PowerShell found in the Appendix at the bottom of the document.
- On the NON-CENTRAL NODES, depending on the setup, perform either step a) or b) below:
- Account running the Qlik Sense services has administrator privileges:
- [Applicable ONLY for April 2019 track]: Delete host.cfg file from C:\ProgramData\Qlik\Sense\
- Start Qlik Sense Repository Service.
- Open the Qlik Management Console (QMC) and redistribute the certificates according to Redistributing a certificate.
- Restart Qlik Sense Repository Service and start all remaining services on the node to make sure they are using the newly distributed certificates.
- Account running the Qlik Sense service does not have administrator privileges:
- [Applicable ONLY for April 2019 track]: Delete host.cfg file from C:\ProgramData\Qlik\Sense\
- In the command prompt, navigate to C:\Program Files\Qlik\Sense\Repository (or corresponding nondefault location), and run:
repository.exe -bootstrap - When the "Waiting for certificates to be installed..." message is displayed, redistribute the certificates according to Redistributing a certificate.
- Once the bootstrap mode has terminated, start the Qlik Sense Service Dispatcher, then start the Qlik Sense Repository Service, and finally the remaining Qlik Sense services.
- Account running the Qlik Sense services has administrator privileges:
- For distributing apps to Qlik Cloud Services, follow the steps mentioned in Distributing apps from Qlik Sense Enterprise on Windows to Qlik Sense Enterprise SaaS.
- For distributing apps to Qlik Sense Enterprise on Kubernetes, follow the steps mentioned in Distributing apps to Qlik Sense Enterprise on Kubernetes.
Steps to perform after an upgrade to re-configure app distribution in a multi-node site
- Perform the steps 1 to 4 mentioned above.
- For re-configuring app distribution in Qlik Cloud Services, perform the following steps:
- Open the Multi-Cloud Setup Console by adding /api/msc to your existing Qlik Sense Enterprise on Windows server name: https://<server name>/api/msc.
- Click the Deployments tile.
- Select your deployment.
- Click “Copy to clipboard” button to copy the updated local bearer token for multi-cloud configuration.
- Now, open your Qlik Sense Enterprise SaaS tenant and select Identity provider in the menu to the left.
- Delete the identity provider configuration that was added previously for this setup.
- Click Create new.
- The Create identity provider configuration window is opened.
- Under Type, select Multi-cloud.
- Optionally, enter a description.
- In the Local bearer token box, paste the token you copied in the deployment setup.
- For re-configuring app distribution in Qlik Sense Enterprise on Kubernetes, perform the following steps:
- Open the Multi-Cloud Setup Console by adding /api/msc to your existing Qlik Sense Enterprise on Windows server name: https://<server name>/api/msc.
- Click the Deployments tile.
- Select your deployment.
- Under Local bearer token for multi-cloud configuration, uncheck the “Qlik Cloud Services format” flag and then click “Copy to clipboard” button to copy the updated local bearer token.
- Now, go to your Qlik Sense Enterprise for Kubernetes environment.
- In efevalues.yaml configuration file, replace the old local bearer token with the new local bearer token by pasting the copied token.
- Make the server read the new efevalues.yaml configuration file.
- Remove the edge-auth pod and restart the services to recreate it.
- The setup should be ready for app distribution after successful restart of services.
Appendix: PowerShell Code
Executing the PowerShell code:
- Copy the code and save it in a ps1 file, for example, certificates_backup.ps1
- Open an elevated command line and navigate to the location where the script was saved.
- Start PowerShell by executing following command: Powershell
- Run the script by executing following command: .\<name_of_the_script>.ps1 in example: .\certificates_backup.ps1
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
function RemoveCertificatesFromStore(
[string] $name,
[string] $location)
{
$success = 1
$oid = "1.3.6.1.5.5.7.13.3"
$localStore = new-object System.Security.Cryptography.X509Certificates.X509Store $name, $location
$localStore.Open("MaxAllowed")
try
{
$certs = $localStore.Certificates
foreach ($cert in $certs)
{
$extensions = $cert.Extensions
foreach($extension in $extensions)
{
if ($extension.Oid.Value.Equals($oid))
{
write-host "Deleting certificate from" $localStore.Name $localStore.Location
write-host " Subject:"$cert.Subject
write-host " Issuer:"$cert.Issuer
write-host " Serial:"$cert.SerialNumber
$localStore.Remove($cert)
break;
}
}
}
}
catch
{
write-host "An error occurred while removing certificates" -ForegroundColor Red
write-host $_.Exception.GetType().FullName -ForegroundColor Red
write-host $_.Exception.Message -ForegroundColor Red
$success = 0
}
finally
{
$localStore.Close()
}
if ($success -ne 1)
{
exit 20
}
}
function CleanCertificates()
{
RemoveCertificatesFromStore "Root" "LocalMachine"
RemoveCertificatesFromStore "My" "LocalMachine"
RemoveCertificatesFromStore "My" "CurrentUser"
}
CleanCertificates
write-host "Done."
exit 0
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Sonja_Bauernfeind is this a notice about the coming 2020 Sep release?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@AdamBSnotused Correct!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sooo ... all you need to do in single node + SaaS environment is delete and recreate the identity provider?
Article does not (yet) clearly mention this ...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @john_oll I'm looking at getting you an answer for this. Will get back to you ASAP and then update the article accordingly.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
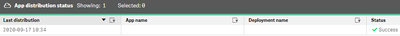
In my single node I see my one historical success
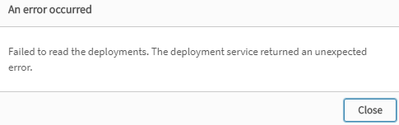
But in multi-cloud setup, the deployments page issues the error:
All I can see in support portal is that the user must have rootadmin or deployadmin, but I have attempted with the administrative account and the installing rootadmin user. Looking forward to anything you dig up Sonja. Must apologise, I have not registered my problem with support.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @AdamBSnotused - I think your issue might require more investigation than I can assist with here. I'd recommend taking this to the appropriate forum on here to engage with our userbase: Qlik Senes SaaS & Multi-Cloud.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @john_oll
As per our Subject Matter Experts:
This does not apply to:
- Qlik Sense Single Node deployments
- Qlik Sense Single Node deployments using app distribution to Qlik Sense SaaS
- Qlik Sense Multi-node deployment not using app distribution to Qlik Sense SaaS
For those three, follow the standard Upgrade Instructions (Source: Qlik Help).
So, for a Single Node you will not have to follow any of the steps listed in this article - as they only apply to Multi-Node installations.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Sonja_Bauernfeind ,
I have to disagree,
I made an upgrade for "Qlik Sense Single Node deployments using app distribution to Qlik Sense SaaS" , and this broke the app distribution to SaaS.
And applying the fix (deleting, recreating Identity provider) fixed it!
Notice that this probably happened since the Server had no SSL certificate, so the installation automatically removed and restored the certificate during the update.
But this problem and this solution does affect "Qlik Sense Single Node deployments using app distribution to Qlik Sense SaaS"!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Let me get back in touch with our SMEs, @john_oll! Thanks for bringing this here though, really appreciate it.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We've updated the article based on feedback from our developer, @john_oll .
What was added:
Note that if you have a single node deployment that uses app distribution, you have one additional step to perform after following standard upgrade instructions. You will be required to recreate the identity provider in QCS tenant for QSEfW setup. This is required because the local bearer token for cloud deployment is recreated using a new certificate after QSEfW has been upgraded to September 2020 release or later.