- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense Enterprise on Windows: Securing and Hardening Server
Nov 7, 2024 8:29:47 AM
Nov 21, 2019 5:28:59 AM
Security of Qlik Sense Enterprise on Windows can be approached in the below discrete areas. All these areas provide different options for increasing security in a deployment, and thereby mitigating vulnerabilities and protecting against attackers.
Content:
- 1. Authentication
- 2. Authorization
- Security Rules
- Section Access
- 3. Operating System Hardening
- Step 1: Disabling protocols and ciphers
- Step 2: Firewalls
- Step 3: Service Account Permission
- Step 4: Anti-Virus
- Step 5 (Optional): FIPS
- 4. PostgreSQL Hardening
- 5. Generalized Web Server best practices
- Apply a trusted certificate
- Optional: Additional HTTP Response Headers
Be aware that a high level of server hardening can lead to failure in your deployment. Be mindful of always having a backup to restore to in case your configuration leads to irreversible failure.
1. Authentication
Qlik Sense Enterprise on Windows supports multiple different Authentication Solutions;
- Windows (NTLM)
- Kerberos
- Ticketing
- SAML
- JWT
- Header
- Anonymous
Qlik can not specify which authentication method is appropriate for each deployment. It is advisable to review currently supported alternatives within your organization and/or Identity Provider (IdP) to implement the most suitable solution for your use case.
2. Authorization
Qlik Sense Enterprise on Windows provides two levels of native authorization in the product.
Security Rules
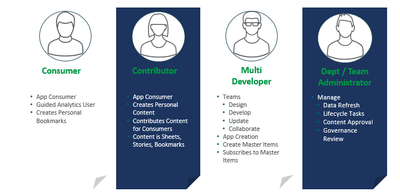
Attribute based access control (ABAC), which is configured through Qlik Sense security rules. This article will not go in depth on how to best implement security rules for your requirements, but it is highly recommended to think of your users based on the capabilities that you intend to provide them. For example different roles and capabilities as shown in image below, allows for a security rule framework to be designed and implemented. This can be done either by yourself by referencing Qlik Sense Help for Administrators and available assets or by engaging with a Qlik Consultant or Qlik Partner.
Section Access
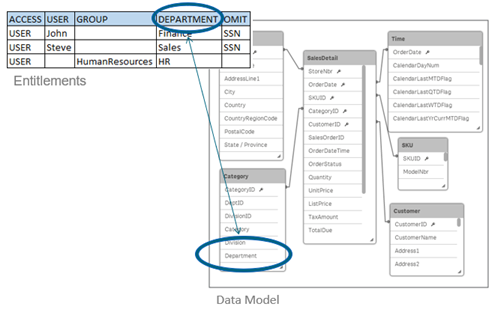
Row level data reduction, which is configured through Section Access at Qlik Sense app level. This article will not go in depth on Section Access implementation, but with this reduction a single file can be used to hold the data for a number of users or user groups. Qlik Sense uses the information in the section access for authentication and authorization, and dynamically reduces the data, so that users only see their own data.
3. Operating System Hardening
Qlik Sense Enterprise on Windows inherits the available protocols, cipher suites, key exchanges and other security hardening which are enabled on the Windows Server operating Qlik Sense.
Step 1: Disabling protocols and ciphers
Windows Server has a lot of protocols enabled by default; however protocols, ciphers, hashes and key exchanges that are considered deprecated or not secure enough should be disabled. There are many ways of doing this, and the Windows administrator and security experts should be consulted so that local policies are accurately applied. For simplicity, understanding and a good overview IIS Crypto 3.0 can be a good tool for evaluating current Windows configuration and applying changes.
Keep in mind that "Best Practice" today might not be recommended in the near future, what was considered "safe" a while ago is not necessarily considered so today. For this reason, it is also important to regularly scan servers for potential vulnerabilities and revisit configurations as required.
The Windows Server needs to be restarted for these settings changes to take effect. It is also important to ensure that all components running on the server still operate as expected after hardening is applied, for example, older non-Qlik software might not be compliant with the latest options and standards.
Step 2: Firewalls
Firewalls typically should be closed, with required ports only opened for intended purposes.
See Qlik Sense Enterprise on Windows ports overview for details on required port based on the deployed architecture.
Step 3: Service Account Permission
For most organizations, local administrator rights allow for an easier deployment, but Qlik Sense Enterprise on Windows does not require local administrator rights in order to function. This can be an attractive option inside some organizations. This will require additional configuration of boot strap mode as described in Qlik Sense Enterprise on Windows Services.
For a brief overview of the rights needed by a Qlik Sense Enterprise service account:
- Full control over the share used by Qlik Sense Enterprise
- Full control over the installation directory (default: C:\Program Files\Qlik)
- Full control over %ProgramData%\Qlik
- Full control over any folders used as data connections
Qlik Sense Enterprise for Windows does not officially support Group Managed Service Accounts (gMSA), but it can operate using one. The initial barrier is that the installer requires a service account and password to be entered during installation. A domain or local account could be substituted for the install stages only to be swapped out in the Windows Services applet (services.msc) after installation. Some functionality may require workarounds (e.g. A User Directory Connection to Active Directory).
Step 4: Anti-Virus
Qlik Sense Enterprise on Windows does require exceptions from anti-virus scan to avoid potential disk I/O conflicts. Refer to Qlik Sense Folder And Files To Exclude From AntiVirus Scanning for more details.
Step 5 (Optional): FIPS
Qlik Sense Enterprise on Windows can run with Federal Information Processing Standards (FIPS) enabled on the Windows Server. This does require a few adjustments of configuration files due to Qlik using non-FIPS compliant algorithms for minor tasks like hash checks. See Running Qlik Sense on Windows systems with FIPS compliance enabled for more details on Qlik Sense and FIPS.
4. PostgreSQL Hardening
Qlik Sense Enterprise on Windows uses PostgreSQL to store meta-data relating to a Qlik Sense site. In multi-node sites or sites where PostgreSQL is isolated from Qlik Sense Enterprise for Windows additional security can be applied;
- Database Traffic Encryption
- Hardening what endpoints are allowed to connect to PostgreSQL as described in PostgreSQL: postgresql.conf and pg_hba.conf explained
5. Generalized Web Server best practices
Qlik Sense Proxy service bundled with Qlik Sense Enterprise on Windows is simply a web-service. This means applying general practice guidance but in the context of Qlik Sense as described below.
Apply a trusted certificate
Qlik Sense Enterprise on Windows acts as a Certificate Authority (CA) during initial installation and signs a certificate that is applied on all encrypted traffic between Qlik Sense services. The same Qlik Sense signed certificate is applied as default certificate also for incoming connections from users accessing Qlik Sense Hub and QMC. This default certificate is not intended for production use, unless user access to Qlik Sense comes through a network load balancer or reverse proxy that trusts the Qlik Sense certificate. For direct user access to Qlik Sense Proxy, a fully trusted certificate can typically be acquired from your local IT and then applied on the Qlik Sense Proxy service.
As of July 2019, Qlik Sense Enterprise on Windows support SHA1 and SHA2 certificates. If SHA384 or SHA512 certificates are needed, then a network load balancer or reverse proxy can be configured in front of Qlik Sense which offloads to Qlik Sense.
Optional: Additional HTTP Response Headers
There are numerous HTTP response headers that can be used in attempting to secure a server. Below are a couple of the most common ones, but as always it is recommended to consult local IT and web security expert on what the recommendations are.
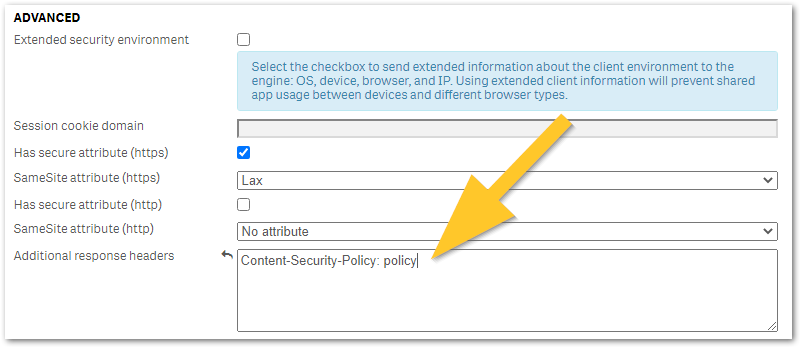
Any additional HTTP response header values can be configured in Qlik Sense Virtual Proxy settings under Additional response headers as shown in the below image and described in Qlik Sense for Administrators: Virtual Proxies. It is recommended to trial any header changes in a new virtual proxy, as poor configuration may accidentally lock you out from Qlik Sense access.
- HTTP Strict Transport Security (HSTS) HTTP Strict Transport Security (HSTS) is an opt-in security enhancement which any web application can support through the use of a special response header. When a supported browser receives this header that browser will prevent any communication sent over HTTP in the future and will redirect all traffic over HTTPS instead. Caution is advised when implementing HSTS, as it might block HTTP access to certain pages that actually requires it or needs to be excluded from HSTS. See MDN Web Docs: Strict-Transport-Security for more details on configuration options.
- Optional: X-Content-Type-Options X-Content-Type-Options response HTTP header is a marker used by the server to indicate that the MIME types advertised in the Content-Type headers should not be changed and be followed. This allows to opt-out of MIME type sniffing.
- X-Frame-Options will prevent the site to be embedded in an iFrame, which can effective mitigate against ClickJacking attacks
- Content-Security-Policy: policy (old: X-XSS-Protection) improves security against some types of XSS (cross-site scripting) attacks.
Policy is a placeholder for your policy of choice and cannot be used as a value. See Writing a Policy (Mozilla) for examples.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
As of July 2019, Qlik Sense Enterprise on Windows support SHA1 and SHA2 certificates. If SHA384 or SHA512 certificates are needed, then a network load balancer or reverse proxy can be configured in front of Qlik Sense which offloads to Qlik Sense.
Any plans to make SHA512 available as an option in the near future for any virtual proxies? And/or do you have an example of the load balancer or reverse proxy that we might use if SHA512 is a hard requirement?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
On running a security scan on the server where QlikSense is running, we get the following warning: "TLS Protocol Session Renegotiation Security Vulnerability port 443/tcp over SSL
QID: 38596
Category: General remote services
Associated CVEs: CVE-2009-3555
Vendor Reference: -
Bugtraq ID: 36935
Service Modified: 02/29/2024
User Modified: -
Edited: No
PCI Vuln: No"
We are running QSEOW August 2023 on a Windows Server 2022 VM.
We need to know if this is a real vulnerability and, if this is so, what the solution for this is. I have seen this issue mentioned a couple of times in the Qlik Community, but without there being a definitive answer.
Regards,
Paul