Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Forums
- :
- Analytics & AI
- :
- Products & Topics
- :
- Integration, Extension & APIs
- :
- Re: Extension not available with virtual proxy (he...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Extension not available with virtual proxy (header auth)
I am having troubles with accessing extensions when I am accessing Qlik Sense via a virtual proxy which is using header authentication.
I first noticed this when using a mashup which is trying to embed qlik extensions into the page. In the console log I can see the following error (403 Forbidden):
From the error message I can see that the xrfkey of the GET request differs from the one which is used in the initial header authentication.
Here are the settings from QMC (virtual proxy):
I would assume that xrfkey is causing XSFR check failure, but I am not sure how to fix it.
In the actual authentication we are defining the X-Qlik-Xrfkey and other headers as supposed. The authentication is working properly. For some reason our mashup is using different xrfkey when trying to access extensions via qrs API.
Any ideas how to fix the issue?
Update:
here is the screenshot of the object from the hub (when using the same virtual proxy and header authentication):
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pasi_lehtinen You should just need to inject the hdr-usr header.
Do not modify the other headers as it may cause some functionality to fail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The call /qrs/extension/schema is the one used to list available extensions. Does the call include your virtual proxy?? If not check that you include the virtual proxy in your require config.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your reply.
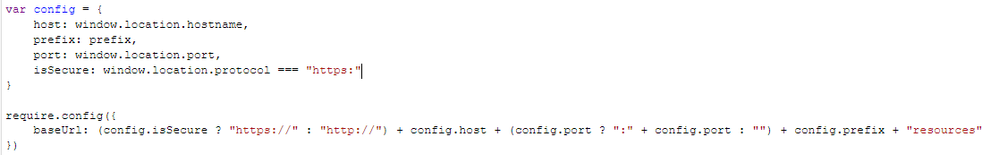
Yes, the call includes the virtual proxy. I also checked the mashup require config. Here is a screenshot of the configurations ( require.config is generated with a dynamic references )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
By the way, the same mashup works perfectly in our other environment which is using SAML authentication instead of header authentication.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
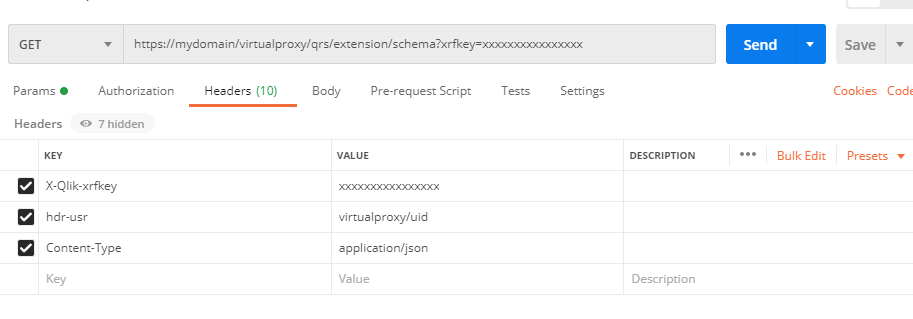
I tested the call to .../qrs/extension/schema with postman simultaneously while having a session open (in my browser). The strange this is that my request works as long as I pass the same xrfkey as query parameter as I have in my open session (in browser). As soon as I change the xrfkey, I get error: XSRF prevention check failed. Possible XSRF discovered.
Here is also the screenshot from the postman:
Seems like I need to some how handle the xrfkey when my mashup is trying to access the extensions, but unfortunately the xrfkey is outside of my control?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pasi_lehtinen , @Damien_V may can assist here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello @pasi_lehtinen
Am I understanding correctly here that you are overwritten the x-qlik-xrfkey header with your own value ?
"In the actual authentication we are defining the X-Qlik-Xrfkey and other headers as supposed."
The xrfkey / x-qlik-xrfkey are generated automatically by Qlik Sense and shouldn't be overwritten.
The only time you need to set the xrfkey / x-qlik-xrfkey is when you are calling the Qlik APIs from your code, which is not the case here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you @Damien_V for your response. Okey, I understand.
Are you able to explain further how the header authentication should be configured? We have set up the environment with virtual proxy which is utilizing header authentication.
- Should I just leave the xrfkey away when redirecting users into the mashup? So the URL would not include any query parameter and also I would leave the X-Qlik-xrfkey way?
- Should I still apply other headers (hdr-usr & Content-Type)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@pasi_lehtinen You should just need to inject the hdr-usr header.
Do not modify the other headers as it may cause some functionality to fail.