Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How to change the certificate used by the Qlik Sen...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to change the certificate used by the Qlik Sense Proxy to a custom third party certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to change the certificate used by the Qlik Sense Proxy to a custom third party certificate
Oct 23, 2025 4:21:35 AM
Oct 29, 2014 7:39:47 AM
Content:
- About
- What is the current certificate used for?
- Certificate options, or: What type of certificate is right for me?
- Requirements, or: What to look out for when getting your cert.
- Where to get a certificate and how to do a CSR?
- Importing the Certificate
- The 5 Install Steps
- Step 1: Getting Started
- Step 2: Import the certificate
- Longer Step 2 (manual import):
- Step 3: Getting the Thumbprint
- Step 4: Configuring the Qlik Sense Proxy
- Step 5:Verification, or: How to prove the certificate was accepted.
- Related Content:
If you’ve just installed Qlik Sense Enterprise, then this image probably looks familiar. Alternatively, Chrome might display The site's security certificate is not trusted, while Firefox may report This Connection is Untrusted.
By default, Qlik Sense uses a self-signed certificate to enable HTTPS access across both the Hub (https:// YourSenseServer/hub) and the Management Console (https://YourSenseServer/qmc). But self-signed certificates cannot be validated or trusted by web browsers and tend to prompt a warning message.
To establish a secure HTTPS connection, the browser must trust the SSL/TLS certificate installed on the server. In the case of self-signed certificates, the signing Certificate Authority is not trusted, hence no certificates generated by the CA are trusted.
To install a trusted certificate for use with the Qlik Sense Enterprise on Windows Hub and Management Console, we need:
- An additional (signed) certificate.
- A brief (5 minute) downtime of the Qlik Sense Proxy.
These instructions are for replacing the certificate used for accessing the Qlik Sense Hub and Management Console. The certificate used for service communication cannot be replaced.
For video Transcript click here
About
What is the current certificate used for?
During the initial install, the Qlik Sense Repository Service creates a set of certificates. Their purpose is to secure Service Communication and Service Authentication.
Qlik Sense uses certificates to authenticate its service across all nodes. See the Qlik Sense Online Help for details. In addition, other products (such as Qlik NPrinting) require these certificates to be establish a connection.
This self-signed certificate is then also used to secure hub and Management Console access through HTTPS.
We will not modify, replace, or remove the originally created certificates. Doing so will break service communication.
What we’ll do instead is to add an additional one.
Certificate options, or: What type of certificate is right for me?
There are three possible types of certificates for us to use.
- A certificate purchased from and signed by a trusted CA (Certificate Authority) such as VeriSign, Thawte, Geotrust, etc.
- A certificate provided and signed by your own Enterprise CA (Certificate Authority).
- And, of course, a self-signed one. Those can be created by any number of applications, such as Microsoft IIS, but is generally only recommended for test environments. More so, it has the potential side effect of teaching users to ignore browser warnings, which we do not want.
Requirements, or: What to look out for when getting your cert.
- The certificate must follow these requirements: Qlik Sense Enterprise on Windows: Compatibility information for third-party SSL certificates to use ...
- The certificate itself must contain a private key
- Has an up to date valid from / valid to date range
- Is signed by a valid and OS or browser configured Certificate Authority
When support gets questions, they are most often related to a certificate missing the private key. Always verify the certificate comes bundled with one when you install it.
It’ll look like this:
Where to get a certificate and how to do a CSR?
The Certificate Authority you chose will have instructions for this, and if you are looking to get a self-signed one or one from your corporation's CA, then a local administrator can provide the certificate to you.
Either way, you are going to need to generate a Certificate Signing Request (CSR) to pass on to your CA. There are tools out there to get that done with, such as certreq from Microsoft (found here), and SSLhopper has a great article on that, which I often send to customers when they ask us about CSRs and how to do them.
Once you obtain the certificate, we'll move on to installing it and activating it in Qlik Sense. This will be done in three quick steps:
- Import
- Get the Thumbprint
- Provide Thumbprint to the Proxy
Importing the Certificate
As mentioned before, we are not replacing certificates. The already existing ones will not be deleted. Doing so would break service authentication between the individual Qlik Sense services and render the system… broken.
The 5 Install Steps
Step 1: Getting Started
On the Qlik Sense node running the Qlik Sense Proxy, log on with the user running the Sense services. This is important since the certificate needs to be accessible for this account.
Step 2: Import the certificate
If the certificate was saved in the .pfx format, then all you need to do is double click the file. Follow the prompt to import the certificate into the Personal store.
Longer Step 2 (manual import):
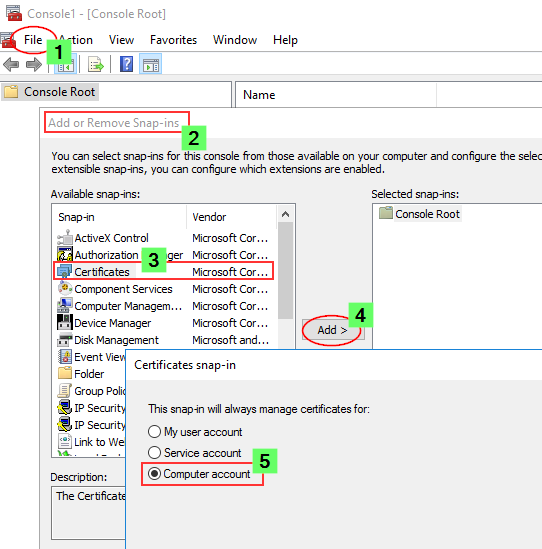
If you want to import it manually or verify if it was correctly installed:
- Launch the Microsoft Management Console (mmc.exe) on the Proxy node
- In the MMC, go to File > Add / Remove Snap-in...
- Select Certificates and click Add
- Select Computer account, click Next, select Local computer and click Finish
- In the MMC, go to Certificates (Local Computer)/Personal
- In the MMC, go to Actions > All Tasks > Import...
- Browse to the certificate file provided to you from your CA
- Follow the instructions on the screen to import the certificate, including the private key
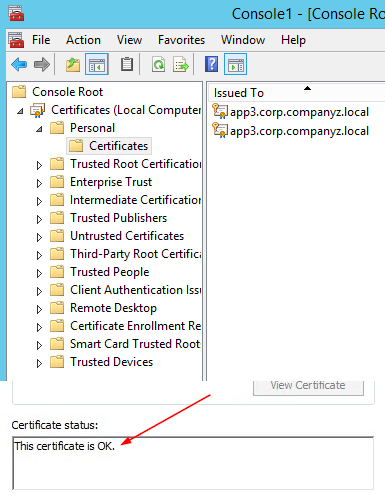
- Verify the new certificate has been imported into Certificates (Local Computer) > Personal > Certificates and that it contains a private key
- Double-click the Certificate > Certification Path and confirm it shows "This certificate is OK"
Step 3: Getting the Thumbprint
Well, since we are already in the MMC, let's open the freshly installed certificate again.
- Switch to the Details tab and scroll down until you find Thumbprint
- Mark the entire thing and copy it into, for example, Notepad.
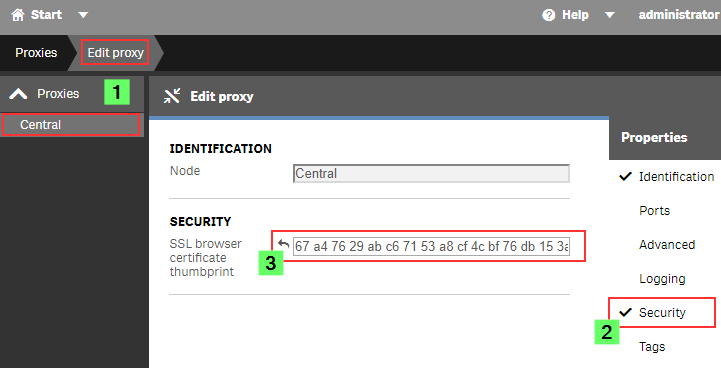
Step 4: Configuring the Qlik Sense Proxy
Almost done!
- Open the Qlik Sense Management Console (QMC)
- Go to Proxies
- Double click the Proxy you want to use (or select and choose Edit)
- Enable the Security options in the Properties panel on the right
- Paste the certificate Thumbprint into the SSL browser certificate thumbprint text box.
Click Apply.
The Sense Proxy will now restart. During the restart, it will be using Windows API calls to correctly bind the new certificate to its SSL ports.
Step 5: Verification, or: How to prove the certificate was accepted.
In the web browser:
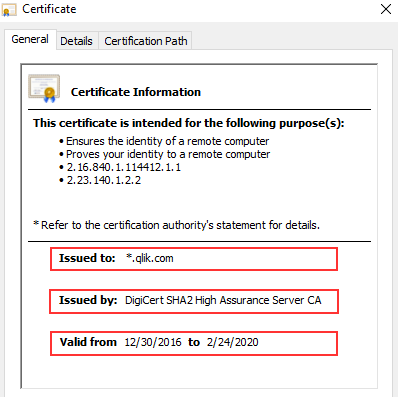
When opening the Qlik Sense Hub or QMC, the certificate will now be displayed in the browser. This may look different depending on the web browser, but in Google Chrome you can click the padlock to the left of the URL to verify what certificate is used.
The information displayed needs to match the properties of the certificate you installed.
In the log files:
If you’d rather see what the Qlik Sense Proxy service is doing, then you can directly check up on that, too.
On the Proxy node, go to C:\ProgramData\Qlik\Sense\Log\Proxy\Trace and open the Security log file from just after the last start.
It will now print a slightly different message than before:
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.LoggingDigester DOMAIN\_service Setting crypto key for log file secure signing: success
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.SecretsKey DOMAIN\_service retrieving symmetric key from cert: success
Security.Proxy.Qlik.Sense.Common.Security.Cryptography.CryptoKey DOMAIN\_service setting crypto key: success
Security.Proxy.Qlik.Sense.Communication.Security.CertSetup 'CN=localhost' (08C871933A58E072FED7AD65E2DB6D5AD3EAF9FA) as SSL certificate presented to browser, which is a 3rd party SSL certificate
And that's it!
There isn't much more to it in a standard Qlik Sense Enterprise installation, but if you have more questions, then maybe a few of these articles can help:
Receiving Bad Request 400?
Make sure the URL/FQDN you are using to access the Hub and QMC is correctly added to the WebSocket Allow List: How to configure the WebSocket origin allow list and best practices
I applied my certificate and it seems to be using it correctly, but browsers are still saying the Common Name is Invalid?
ERR_CERT_COMMON_NAME_INVALID when using 3rd party certificate
Qlik Sense keeps reverting to the default and complains it can't find a valid ssl certificate with the thumbprint.
The certificate may not have a Private key or the service account does not have access to it.
How to: Manage Certificate Private Key
The Qlik Sense Service account doesn't have admin privileges and the certificate is not accepted.
Related Content:
- Qlik Sense Hub and QMC with custom SSL certificate
- A certificate error or warning is displayed in the browser when accessing the Qlik Sense Hub or Mana...
- Qlik Sense - Changing to a signed server proxy certificate
- Qlik Sense - Changing a proxy certificate
- ERR_CERT_COMMON_NAME_INVALID when using 3rd party certificate
- Qlik Sense: Compatibility information for third-party SSL certificates to use with HUB/QMC
- Requirements for configuring Qlik Sense with SSL
- Couldn't find a valid ssl certificate with thumbprint and the incorrect certificate used on hub
- How to: Change the Qlik Sense Proxy certificate if the service account does not have local administr...
- NET::ERR_CERT_AUTHORITY_INVALID
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, Please help. I have installed the certificates but still getting the not secure icon on the browser which is disabling the mobile app from working as well.
If the environment where Qliksense is installed is showing the secured icon and certificate valid, okay, but when connecting over the internet to the hub I still get the certificate invalid error.
Kindly assist on what steps to troubleshoot and resolve this.
Ayo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Ayo,
Just closing the loop here that you've investigated this based on Qlik Sense Hub and QMC with a custom SSL certificate and are looking into ensuring the certificate you are using has a private key.
/Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Sonja,
Thanks, I have requested the server administrator provide SSL certificates with a private key.
Regards,
Ayo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
To whom it may concern: you can automate this with ahaydon/Qlik-Cli-Windows.
In my case I use Win-Acme to get certs from Let's Encrypt, and as a post-renewal step I added powershell.exe as script, and as parameters: `Update-QlikProxy -id [my-proxy-id] -SslBrowserCertificateThumbprint {Cert.Thumbprint}`
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Sonja and everyone who has helped with the issues I mentioned above.
I have finally installed the SSL and applied the thumbprint on the Qlik sense server.
Now when accessing the hub or qmc from over the internet the secure icon is available but now when accessing the hub or qmc with the server environment name (i.e default localhost address when installing the Qlik sense earlier) it gives the insecure error now.
Can this be rectified or I am still missing something.
I have read and watched all videos concerning SSL and Qliksense but all to no avail.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@delmak2000 , you cannot reference internal server names in certificates that are issued by publicly trusted Certificate Authorities for security reasons. If you need to not have the certificate error internally and externally, one way you may be able to accomplish this is with a reverse proxy, which offers the internet client it's own certificate, and acts as the man-in-the-middle for the encrypted communication with the QS server from a public location. The most practical way however may be for internal users to use the public name and to have the DNS server resolve that name to the internal IP address.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, Andre for the prompt response. I did resolve to call the public name on the Qlik sense server environment but I noticed when I tried logging in with the domain user that serves as the root admin and was used for the installation it doesn't re-direct to the hub or the QMC either. But using the server name/localhost will successfully logon to the hub or QMC but with an invalid certificate.
Any pointers on if the reverse proxy is worth it?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, I've successfully installed the SSL on my VM hosting QS. I configured the QMC. And now my connection over Intranet is secure. But I've used before Azure Reverse Proxy for one of the Virtual Proxies so users can access from eternal network.
It had it's own certificate which was secure already. After implementing new SSL my Azure Virtual Proxy for Qlik stopped working. I get connection timeout error straight away when I log into the hub. What can be cause of this, how to fix? It worked before implementing custom SSL to Proxy.
@Sonja_Bauernfeind , @Andre_Sostizzo any idea what can I do?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @matKa - Thank you for getting in touch! To get more eyes on this issue, I'd recommend posting it to our forums: Deployment and Management.
When posting, please include additional details on the setup, for example, if your Reverse Proxy and the Qlik Sense Virtual Proxy have different certificates and more detail on how the environment is constructed. A review of the Proxy logs (Log locations) will also give you an idea of what the issue may be.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Sonja_Bauernfeind @Andre_Sostizzo ,
I'm in this process and went to buy a custom SSL certificate, unfortunately I have been asked to *validate* CSR data and it looks the only way is a "file" authentication, hence they asked me to upload a specific file that should be reachable at "45.XX.YYY.Z/.well-known/pki-
Could you help me sorting this out? Thanks a lot, Brunello