Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Attacker can upload a malicious file in the applic...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Attacker can upload a malicious file in the application with a double extension in Qlik Sense
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attacker can upload a malicious file in the application with a double extension in Qlik Sense
Nov 30, 2022 10:13:21 AM
Nov 30, 2022 10:12:05 AM
How to mitigate if an attacker uploads a malicious file in the application with a double extension in Qlik Sense?
The XML files can be used for data ingestion. By default XML is disabled, but we do provide the ability to allow list XML as a data type.
Uploading an XML with Javascript (XSS) will allow a malicious user to run code in the context of the targeted user's session.
Environment
Qlik Sense Enterprise on Windows February 2022 and previous versions.
Resolution
Add the following flag in the "C:\Program Files\Qlik\Sense\Repository\Repository.exe.conf" file,
<!-- Flag will enable to scan for script tags in the uploaded XML files through the ContentLibrary or AppContent--> <add key="ScanXmlFileForScripts" value="true" />
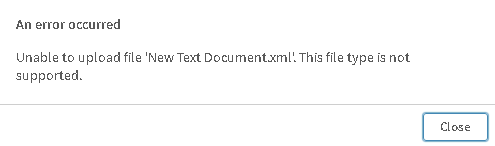
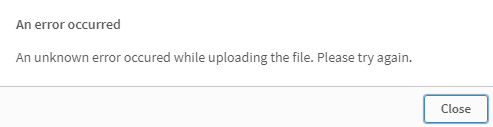
Upon detecting the script within the XML file, the User will be warned that the file can not be uploaded.
Or the below error based on the Qlik Sense version,
Fix Version:
Qlik Sense Enterprise on Windows May 2022.
Cause
- QB-1693
- QB-8378
- QB-11820
To allowlist XML files in Qlik Sense May 2022 and later versions, please contact the Qlik Support Team via Live chat or Submit a case!