Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- Deployment & Management
- :
- Re: Integrating AD Users with Okta SSO
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Integrating AD Users with Okta SSO
Environment: Qlik Sense Enterprise 3.0.0
We use Okta for single sign-on, and all Okta accounts for internal users are sourced from Active Directory (domain = CORP). The user ID used by most of our SSO-enabled applications is Email Address.
I have created a User Directory Connector for our CORP AD domain with a filter to only synchronize users in the group 'Okta-Qlik-Users'. This is working fine and the accounts created in Qlik have a User ID equal to the Windows logon name (SAMAccountName).
We now want to use Okta SSO with Qlik Sense. I have followed the instructions for creating a virtual proxy to integrate with Okta and have tested it successfully. The problem is that when a user logs into Qlik using Okta SAML it creates another user account using their email address as the User ID and 'OKTA' as the User Directory.
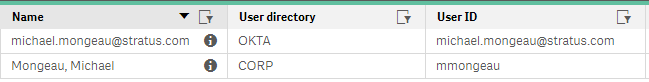
Instead of creating a new account we would like to simply map the Okta SAML login to the user's existing AD account. Is there a way to do that?
Thanks,
Michael Mongeau
IT Applications Manager
Stratus Technologies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Michael,
You can achieve the following requirement.
Basic Two Things you need here:
The user ID and user Directory values should be same.
same means:
When you login or pulled users from UDC
and
When you login from OKTA using
If both cases matches then same user is refereed in Qlik Sense Database.
1.SAML attribute for user ID
By asking the SSO admin (Here OKTA Guys) to send the required user attribute Value as an attribute in SAML Response.
Same attribute you can configure it in Virtual Proxy as SAML attribute for user ID.
here:
May be SAM-Account-Name is used not sure.(Your proxy configuration and AD attributes will provide the mapping here)
2.SAML attribute for user directory:
By asking the SSO admin (Here OKTA Guys) to send the required User Directory Value as an attribute in SAML Response.
Same attribute you can configure it in Virtual Proxy as SAML attribute for user directory.
here:
domain = CORP
This is only based on login of the user.
But if you have some some security rules written utilizing the groups info received from UDC pulling data directly from AD.
Then we need to send those groups info also in SAML Response matching the groups info received from UDC.
Thanks,
Suraj
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks so much for the suggestion. Here is how I got it working.
In the Okta Qlik SAML application:
- on the Sign On tab set the username format to 'AD SAM Account Name'
- on the General tab added a custom attribute called 'username' and set it to 'appuser.userName'
In the Qlik Virtual Proxy for Okta, in the Authentication section:
- set SAML attribute for User ID = username
- set SAML attribute for user directory = [CORP]
I decided to just use a static attribute for the user directory name since I do not expect it to change.
Michael
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We are having similar problem but with reverse item.
QMC and Virtual Proxies are set to use email address. But whenever User logins through okta authentication, account with SAMAccountName (short user ID) are being created. It use to work and only email address use to create, but after upgrading to Qliksense 2019 we started noticing that duplicate account with Short User ID are being created. I checked the configuration and it seems to be fine. Could you tell me if there is anything else I need to check.
- QMC--> Pulls email address and CORP through ODBC SQL tables.
- Virtual Proxy--> OKTA SAML
- User ID: email
- User directory : [CORP]
But accounts are created as followings
- useremail@company.com
- UserID
Anyway to getrid of 2nd duplicate account i.e UserID account.
More info on another thread I have created below.
Regards,
Chandru
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this. Solved my issue with duplicate accounts.