Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- Deployment & Management
- :
- Re: User Directory Connector with Azure AD
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
User Directory Connector with Azure AD
Hello, I had a User Directory Connector (UDC) configured with our on premises AD (filtering some users and cost centers) and using the default Virtual Proxy (VP).
Now, we configured a new VP to Azure AD (AAD) to single sign-on (SSO) sucessfully. But have no idea how to filter the same cost centers to get the users from AAD. We tried to create a new UDC with a generic LDAP but no success (same URL from first UDC - I know, strage, but we gave it a shot).
I saw this post but I think the guys are stuck in the same point.
Is the only way to ask the users access at least one time to then allocate a license to them? Or is there a way to get them from AAD via UDC?
I'd really appreciate any help.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If someone need the info, we solved this issue:
- Using the same Path and LDAP filter of the old UDC;
- In Directory Entry Attributes, the Account Name as the same attribute used in claim with AAD (in our case, "mail");
- And the User Identification attribute as "user" instead the default "inetOrgPerson";
QS June 2017, BTW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If someone need the info, we solved this issue:
- Using the same Path and LDAP filter of the old UDC;
- In Directory Entry Attributes, the Account Name as the same attribute used in claim with AAD (in our case, "mail");
- And the User Identification attribute as "user" instead the default "inetOrgPerson";
QS June 2017, BTW.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ennio,
great information thank you very much.
- In Directory Entry Attributes, the Account Name as the same attribute used in claim with AAD (in our case, "mail");
In this sentence, what is "the same attribute used in claim with AAD" ? Are you talking about a property of the Qlik Sense Virtual Proxy or a property of your Azure AD ?
Best Regards.
Johann
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry for delay, jchoucq. I don't know if still helps but is the property of AAD.
The Ldap-Display-Name from MSDN (or from this friendly version).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ennio,
How did you manage to import users in Qlik Sense, did you successfully create an UDC to Azure AD ?
I cannot make it work (QS Feb.2018, Azure AD over SSL port 636).
Thanks for this information !
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, Thomas.
Actually, we created a UDC to our on-premise AD (using Generic LDAP connection).
Then we just authenticate in AAD. The title of the thread was unfortunate, after all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if anyone wants to create an Azure AD UDC : here attached is the "Generic LDAP UDC configuration".
So, you just have to change the User-Directory-Attribute "User identification" to "Person" and that's it
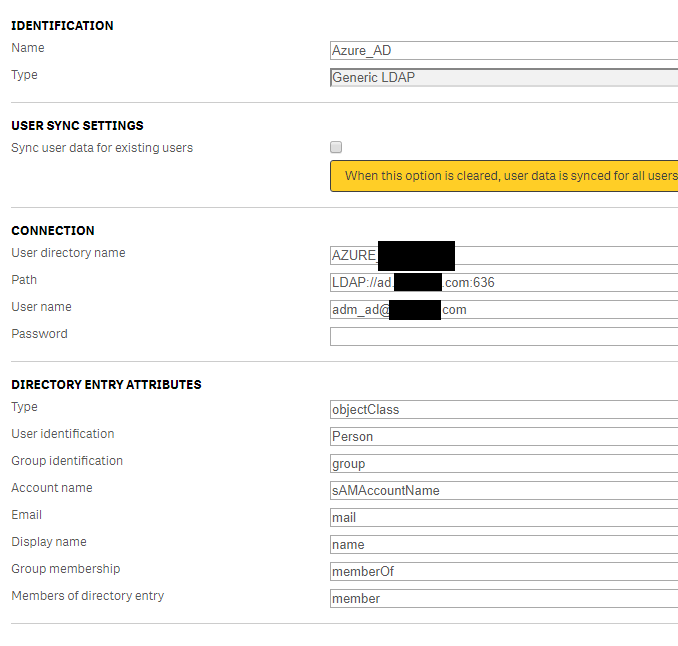
Regards,
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To expand on the answer of @thomaslg_wq , we have a case where we had to use LDAPS protocol, which requires a SSL certificate installed on the qlik server (we had a *-certificate, which works for ldaps.domain.com). The base setup for the LDAP connector worked as demonstrated, but it also required some configuration in Azure network security groups for the UDC to become operational.
Unfortunately I don't have detailed information on this step, as it was done by our clients IT supplier, but after this the connection between the UDC and azure ad was effectively opened up, and we successfully managed to bring all users from azure AD to the qlik repository.
Before this, running LDAP Admin tool on the qlik server returned a "Server down!" error, so I assume Azure NSG works as something like a firewall between the domain server and azure ad.
I cannot say for sure if all the steps would have been required, or just whatever was done in the Azure NSG, but with this configuration it works for our case.