Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How to determine string policy for Content Securit...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to determine string policy for Content Security Policy Header
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to determine string policy for Content Security Policy Header
Sep 20, 2021 9:14:01 AM
Nov 26, 2018 2:12:55 PM
Customer policy adopted injection via the reverse proxy of the Content Security Policy header for security reasons.
The policy adopted is basic: default-src 'self'
Opening the QlikView AccessPoint or Qlik Sense Hub may fail or the AccessPoint may only render partially.
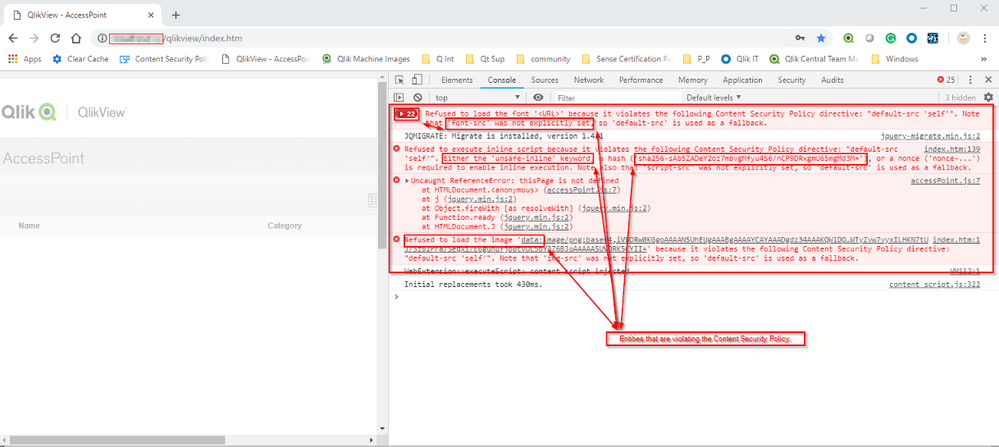
The Browser Debug tools will provide more insight:
Environment:
QlikView
Qlik Sense Enterprise on Windows
The Header Content Security Option contains a string of rules that informs the browser which resource/code is trusted to be loaded, executed rendered.
More details on the argument could be found here:
https://www.w3.org/TR/CSP3/ ,
Resolution:
For QlikView Accesspoint a first example is to use Content-Security-Policy: "default-src 'self' 'unsafe-inline' data: ;" ; (note that using 'unsafe-inline' option could be unsafe in a the proxy injection scenario when the client will brose a different site , you could/evaluate to use instead the sha256-hashcode version )
Further option could be necessary if for example you have QlikView Extension Object ( Server and Document Extensions) that are using external resources downloaded from CDN locations;
In this case the troubleshoot is the same use F12/Development Tools to check the resource that violates the policy and ad an exclusion.
Related Content:
QlikView Access Point Shows "Loading Content" Indefinitely,
What is CSP (Content-Security-Policy) and How does it Relate to Qlik?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Filippo_Nicolussi_P ,
How can we implement Content Security Policy in Qliksense Enterprise version?
Regards,
Rohit Gharat
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @rohitgharat
I believe I already provided you with an answer to this in a different post. Copying it in here for reference:
If you are looking to add custom response headers in Qlik Sense (Enterprise on Windows), see How to add additional response headers in Qlik Sense.
Please note that we cannot advise on what headers to add.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello all,
How can I create a SHA256 hashcode version as written in the solution in Qlik Sense Enterprise?
Any other solution that makes the use of 'unsafe-inline' / 'unsafe-eval' in CSP unnecessary is also welcome.
I am posting the question here because Qlik Support closed my ticket with the note:
Regarding your question about "How you can do to consider using the SHA256 hashcode version instead”, please go to this article (see below link) and post this question there. The author (owner) of this article or the content manager will provide answers/feedback
Thank you very much for your help.
Thorsten
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @thorsten_wolff
I have reached out to the support agent who has assisted you and am looking into what information we can provide you with.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, @thorsten_wolff @Sonja_Bauernfeind
Regarding the sha-256 method/string to use it is proposed directly in the solution in case of the article screen-shot it correspond to the third shape highlighted:

here above in green.
The article was published 3 years ago; do the development tools still provide the sha-256 as above? Content Security Policy header is an integrations not provided natively by Qlik; as per introduction "Customer via reverse proxy was injecting that header".
For updates and details possible suggestion is to give a look here https://developer.mozilla.org/en-US/docs/Web/HTTP/CSP involving your IT Security Team.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
OK, I think I was thinking too complicatedly.
I used the F12/Development Tools and have set script-src 'self' 'sha256-AXWwKykxPuYO3+hAZ/9h0sc7xvhRQSSdNtWjehy0kcU='
It still gives me the below error
Refused to execute inline event handler because it violates the following Content Security Policy directive: "script-src 'self' 'sha256-AXWwKykxPuYO3+hAZ/9h0sc7xvhRQSSdNtWjehy0kcU='". Either the 'unsafe-inline' keyword, a hash ('sha256-...'), or a nonce ('nonce-...') is required to enable inline execution. Note that hashes do not apply to event handlers, style attributes and javascript: navigations unless the 'unsafe-hashes' keyword is present.
Thank you for help.
Thorsten
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Did you checked the guide https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/script-src for the updated version and how to?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Community,
In Qlik sense enterprise, according to VAPT report there are some missing security headers which needs to be implemented. We are facing issue while adding the below security header in the virtual proxy.
--> Content-Security-Policy: default-src 'self'
After implementing it we are unable to access qlik getting black/grey screen.
Articles followed:
How to determine string policy for Content Securit... - Qlik Community - 1715491