Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How to match users between Qlik Sense Client Manag...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to match users between Qlik Sense Client Managed and Qlik Cloud to avoid duplicate license use
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to match users between Qlik Sense Client Managed and Qlik Cloud to avoid duplicate license use
Jan 25, 2023 3:40:30 AM
Jan 25, 2023 1:05:00 AM
When using a Qlik Sense Unified License, it is possible to use the same license in Qlik Sense Client Managed and Qlik Cloud and use one license assignment for the same user, no matter which product the user is using.
However, for users to be able to use the same license, the user name and domain must match. This article explains how Qlik Sense differentiates users.
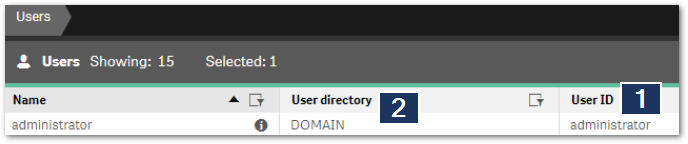
In Qlik Sense Client Managed, the user is recognized based on his User Id (1) and User Directory (2),
In Qlik Cloud, the user will be recognized based on their IdP subject:
User Directory is compulsory in Qlik Sense Client Managed but not in Qlik Cloud.
As the default QlikID authentication in Qlik Cloud does not include a User Directory in the IdP Subject, it is not possible to match users from Qlik Sense Client Managed to users in Qlik Cloud when using Qlik ID as the authentication method. You need to bring your own Identity Provider (IdP) to do so.
Below are a few explanations of what is used as the User Directory and User Id based on which type of authentication you are using.
Qlik Sense Client Managed
| Authentication Method | User Directory | User Id |
| Windows | Windows domain name (not customizable) | SamAccountName (not customizable) |
| SAML | SAML Attribute for User Directory | SAML Attribute for User Id |
| OIDC | realm (if set, the string will be used as a static string value) | sub (If "sub" already includes a domain name in the form of Domain\UserId then "realm" is optional) |
| JWT | JWT Attribute for User Directory | JWT Attribute for User Id |
* Except for Windows authentication, the above fields can be customized in the virtual proxy settings
Qlik Cloud
OIDC authentication:
User Directory: Realm
If set, the string will be used as a static string value.
User Id: sub
If sub already includes a domain name in the form of Domain\UserId, then realm is optional.
JWT authentication:
User Directory and User Id: sub
The value must contain both a domain name and a user Id in the form of Domain\UserId. See https://qlik.dev/tutorials/create-signed-tokens-for-jwt-authorization for details.
Environments
Qlik Sense Enterprise on Windows May 2021 and later
Qlik Cloud
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Damien_V - Can we identify in anyway with which identity provider configuration the "IdP subject" is created in Qlik Cloud tenant ? We switched from Ping IdP to Google IdP recently where email being common denominator between both IdPs. Does "IdP subject" changes if we switch from one IdP to other ?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The IdP subject is created/updated based on what you have filled in in the "sub" field when you have set up the Identity Provider in the Qlik Cloud console, and then that would depend on what the IdP is exposing inside the claim you have filled in. You can check manually by doing this:
As of now, Qlik Cloud will behave different ways depending on how the claims have been set. If the user logged in with the new IdP has the same email and the "email_verified" claim is set to true on the IdP side, then Qlik Cloud will keep it as the same user and update the IdP subject to the new IdP subject provided by the new IdP.
If email is different or "email_verified" is not sent to Qlik Cloud by the IdP or is set to false, then Qlik Cloud will create a totally new user as a separate entry, this new user will be considered different and not inherit any previously created content.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Damien_V
We set OIDC authentication with azure, as default we authenticate as "sub" it's exposing inside the claim sub "UserId", which cause for duplicate license use, since we authenticate with ONPREM environment as "name" claim, we aimed to have both authenticate as "name".
we tried to create alternate claim for the mapped sub with no success, it seems that "sub" claim of OIDC can't have filled with other claim such as "name".
any change with "sub" in the Qlik Cloud console brake the authentication.
hope you can advise
Thanks
Eyal
@Anonymous
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @eyalnir_qlik
I talked to our subject matter experts regarding this:
Please post your issue in as much detail as possible in the Integration forum. And before doing so, consider the following:
Verify that you have the claim you want to use exposed in your Azure ID token. You can do so by requesting the ID token manually as described in Qlik Sense: How to request an OIDC token manually and check if correct attributes are included (Powe...
All the best,
Sonja