Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik Sense: How to request an OIDC token manually ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik Sense: How to request an OIDC token manually and check if correct attributes are included (PowerShell)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense: How to request an OIDC token manually and check if correct attributes are included (PowerShell)
This article explains how to request a token manually from your Identity provider token endpoint and verify if the required attributes are included in the id_token.
Qlik Sense Enterprise for Windows reads the attributes from the id_token and is not using the /userinfo endpoint to fetch them.
Environments:
Qlik Sense Enterprise on Windows May 2021 and higher
Qlik Cloud (For "ADFS" and "Azure" Identity provider types only)
First of all, for testing purposes, add the URL "https://test/login/callback" used in this script in your Identity Provider (IdP) allowed redirect URIs. The reason we are doing this is because we want to request the token manually to check its content and not have it getting automatically processed by Qlik Sense.
- Run the below PowerShell script to get your authorization URL. Variables authorization_endpoint, client_id, and scope need to be updated to match your IdP, those information can be found from the /.well-known/openid-configuration endpoint.
$authorization_endpoint = 'https://dc1.domain.local/adfs/oauth2/authorize' $client_id = '592a5672-a360-49da-93a4-20654f42d3c2' $redirect_uri = [System.Web.HTTPUtility]::UrlEncode("https://test/login/callback") #For ADFS, use 'openid%20allatclaims%20profile%20email' for the scope $scope = 'openid%20profile%20email' $code_challenge="7TsROgPKuP0hHoWWwEGqMsIOgzokT3xAz8kWoo7Ivp8" #Paste this URL in your browser to get back the authorization code $authorization_endpoint+'?response_type=code&client_id='+$client_id+'&redirect_uri='+$redirect_uri+'&state=xyzABC123&nonce=3O2bsVV99-kjikCWCxqzxOx007aXbKMUd0YXBwA3sUk&scope='+$scope+'&code_challenge_method=S256&code_challenge='+$code_challenge - Paste the URL output from the script in your browser and log in to your Identity provider, the URL should look like this:
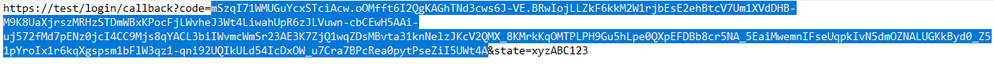
https://dc1.domain.local/adfs/oauth2/authorize?response_type=code&client_id=592a5672-a360-49da-93a4-20654f42d3c2&redirect_uri=https%3a% 2f%2ftest%2flogin%2fcallback&state=xyzABC123 &scope=openid%20allatclaims%20profile%20email
After the authentication is completed, you will be redirected to https://test/login/callback with an authorization code in the URL, copy the authorization code that we will use in the next step.
Copy the value between code= and the next & sign. (The length of the authorization code may vary depending on the IdP) - Request the token from the token_endpoint URL (also found from the /.well-known/openid-configuration endpoint)
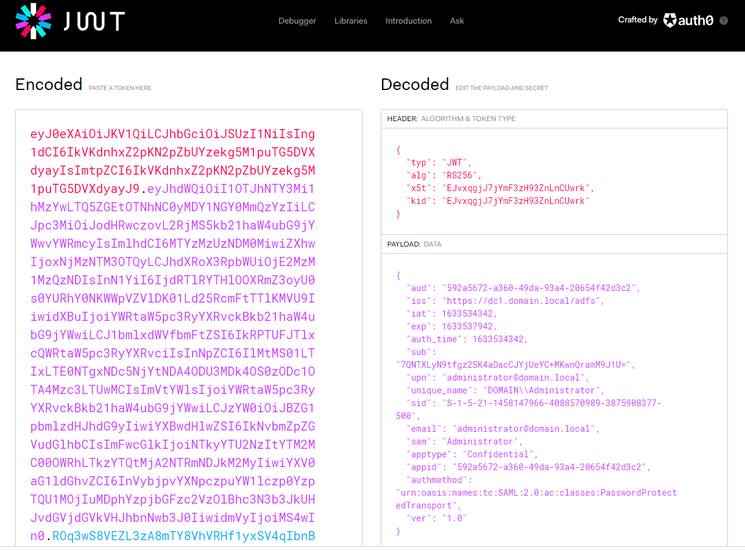
$client_id = '592a5672-a360-49da-93a4-20654f42d3c2' $redirect_uri = [System.Web.HTTPUtility]::UrlEncode("https://test/login/callback") $client_secret = 'Ssxx92jvm6RE_Plf1NnKgduZujE99nd0vWuujE_L' $token_endpoint = 'https://dc1.domain.local/adfs/oauth2/token' $code_verifier="_fqY.Xg5srawq24h9_A57tjY-ycqX0PzzIcM7VcwLZRou_Mvqn-_tCTz4ICWcXoCTO8NXlm3b9RfGOjSZEH68a_gWgaLByddN5y52M06~Z8XlO3XMgOJRWK0DefsxcmC" #Put your authorization code here $auth_code = 'mSzqI71WMUGuYcxSTciAcw.kZdiCG6J2QgNAPRcEZ9A51OMW6g.TMrNMhHPBiG3aNbh_4lbUakFzWoU_MFcDQZcL6_wBIaDd_1_DMWz9OZUSvRcE_zR115HwNXdZYUTjHB6mcnK3u5R2EDxsVKthwQwbP184ujVK1c8LmI-QOMb4jEGRTAm49nbtM8MfO4pTO1fICMSU7CLuhVb8KcCefjPOQ5W0JMKLl7XElvhJDLg5n6v1V2m8L2ZaCQVDy6oTiZygIr20j3TpQnpu2Zwk1KzbttOTGqeJgzCoyPJJJcRjnOrD1zPmBEENrz8fuZwdihRIPZufzhj0gEJ18-stWBz7polztBH7y_jKn-mK6WgIqlLSG2AlmcQa9kBANLmfbal7OUFtA' $pair = "$($client_id):$($client_secret)" $encodedCreds = [System.Convert]::ToBase64String([System.Text.Encoding]::ASCII.GetBytes($pair)) $basicAuthValue = "Basic $encodedCreds" $hdrs = @{} $hdrs.Add("Authorization",$basicAuthValue) $body = 'code='+$auth_code+'&grant_type=authorization_code&redirect_uri='+$redirect_uri+'&code_verifier='+$code_verifier $response = Invoke-WebRequest -Uri $token_endpoint -Method Post -Body $body -Headers $hdrs -ContentType 'application/x-www-form-urlencoded' echo $response.Content - Copy the value in "id_token" from the request response, and decode the JWT token to see what it contains.
For simplicity, you can use the debugger on https://jwt.io :
You can confirm if the expected claims are included in the token payload or not.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I think it's because of your PowerShell version.
Try to replace the line
$redirect_uri = [System.Web.HTTPUtility]::UrlEncode("https://test/login/callback")by
$redirect_uri = "https%3A%2F%2Ftest%2Flogin%2Fcallback"
and try again (Make sure to generate a new code as the old one may already be invalid now)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
It seems It didn't help
Invoke-WebRequest : Not found.
At C:\Users\ansam3\Documents\Untitled1.ps1:18 char:13
+ $response = Invoke-WebRequest -Uri $token_endpoint -Method Post -Body ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (System.Net.HttpWebRequest:HttpWebRequest) [Invoke-WebRequest], WebException
+ FullyQualifiedErrorId : WebCmdletWebResponseException,Microsoft.PowerShell.Commands.InvokeWebRequestCommand
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Here is the one,
$token_endpoint = 'https://abc-icow-test.eu.auth0.com/.well-known/openid-configuration'
And for ref, Script as follows
|
$client_id = 'xxx' #Put your authorization code here $hdrs = @{} $response = Invoke-WebRequest -Uri $token_endpoint -Method Post -Body $body -Headers $hdrs -ContentType 'application/x-www-form-urlencoded' |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This is not the correct token endpoint.
You need to open https://abc-icow-test.eu.auth0.com/.well-known/openid-configuration
in your browser and find the correct token endpoint, it should appear as token_endpoint in there.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Damien_V That is working, But, somehow still issue with 400. Any other clue, where I can think about?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@rockabs Did you check in your id_token that all compulsory attributes (sub, name & email) are included ?
When checking back your virtual proxy settings screenshot, I also noticed that you haven't set the "sub" attribute, which is a compulsory attribute.
An attribute should exist in the id_token called the same value that the one you have set in the virtual proxy.
Please also note that if the value of the "sub" attribute does not contain a domain name, then you also need to set a value in the "realm" field.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Damien_V As I see, It is not mentioned anywhere that it is mandatory?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'll let our documentation team know so that they can add it on the Qlik help site.
Thank you for noticing.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Damien_V Have you got updated the document?
Anyway, now we have added with sub, name, and email in id_token, please refer to attached images and suggest?
I eagerly looking forward to getting success.
This is from QMC, If you can enlighten me where is the mapping issue?