Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- All Forums
- :
- Deployment & Management
- :
- Re: Qlik Sense access doubt with https or http
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense access doubt with https or http
Hi guys,
I need some help with my multi-node Qlik Sense installation.
I have 3 nodes, every node with its virtual proxy.
I have in white list of every node the server name, full server name, local ip and external ip.
My scenario is accessing in the server:
- If I access with https and server name. Acces OK and certificate OK. No problem.
- If I access with http and server name. Can't access. I got the message "Internal server error"
- If I access with https and local ip. Access OK but certificate error.
- If I access with http and local ip. Can't access. I got the message "Internal server error"
- If I access with http and external ip. Access OK. No problem.
- If I access with https and external ip. Access OK but certificate error.
I tried restarting services many times but nothing happens.
I need help to access with any method perfectly.
Many thanks!
- « Previous Replies
-
- 1
- 2
- Next Replies »
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition access via http is activated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
*BUMP * Hi Qlik Community - a little love for Rafael here if you can!
Thanks
Mike T
Mike Tarallo
Qlik
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Mike, i need yo find a solution for my client.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
TLS errors can be obnoxious because OSI Transport layer's can cause issues. In any case, when you get the certificate error what do you see in Google Chrome?
Diagnosing the Cert Misbehavior
1. Open Chrome Browser
2. Hit F12 to open the Developer console
3. Click "Network"
4. Visit the site url where it whines about the cert and click straight through.
5. In the Developer Console, click "Security". It's at the end of the bar, so you might have to use the dropdown.
6. Click the "View certificate" button
7. This should give you a clue about your cert error. In this test case, the url is "http://qliksense", but the certificate was issued to "qliksense.somecompany.net" and browsers won't like that one bit.
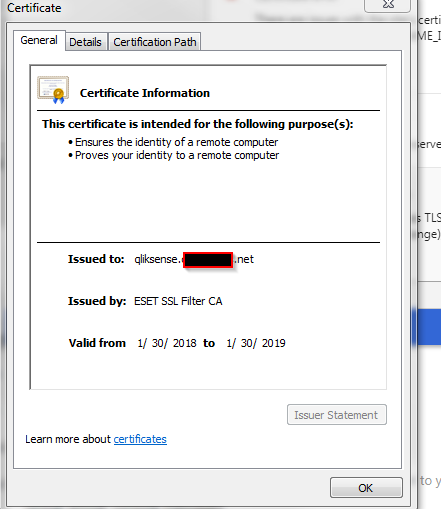
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Justin,
Thanks for your reply.
I tried this steps and i see the certificate is issued to the machine name, no for ip.
But my question is, if i put the different ip's in the white hosts list, the certificate is not valid for every url? I don't have knowledge about certificates.
I need to create a new certificate for every different ip? Exists a procedure to create these certificates in sense or I need external tools? I read in other post if i restart the proxy service, the certificates in sense are regenerated and same happens if we delete them. Maybe i'm wrong.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Rafael Matamoros <span class="icon-status-icon icon-partner" title="Partner"></span> wrote:
...
But my question is, if i put the different ip's in the white hosts list, the certificate is not valid for every url? I don't have knowledge about certificates.
I need to create a new certificate for every different ip? Exists a procedure to create these certificates in sense or I need external tools? I read in other post if i restart the proxy service, the certificates in sense are regenerated and same happens if we delete them. Maybe i'm wrong.
No, certificates are valid for the DNS names specified in the certificate*:
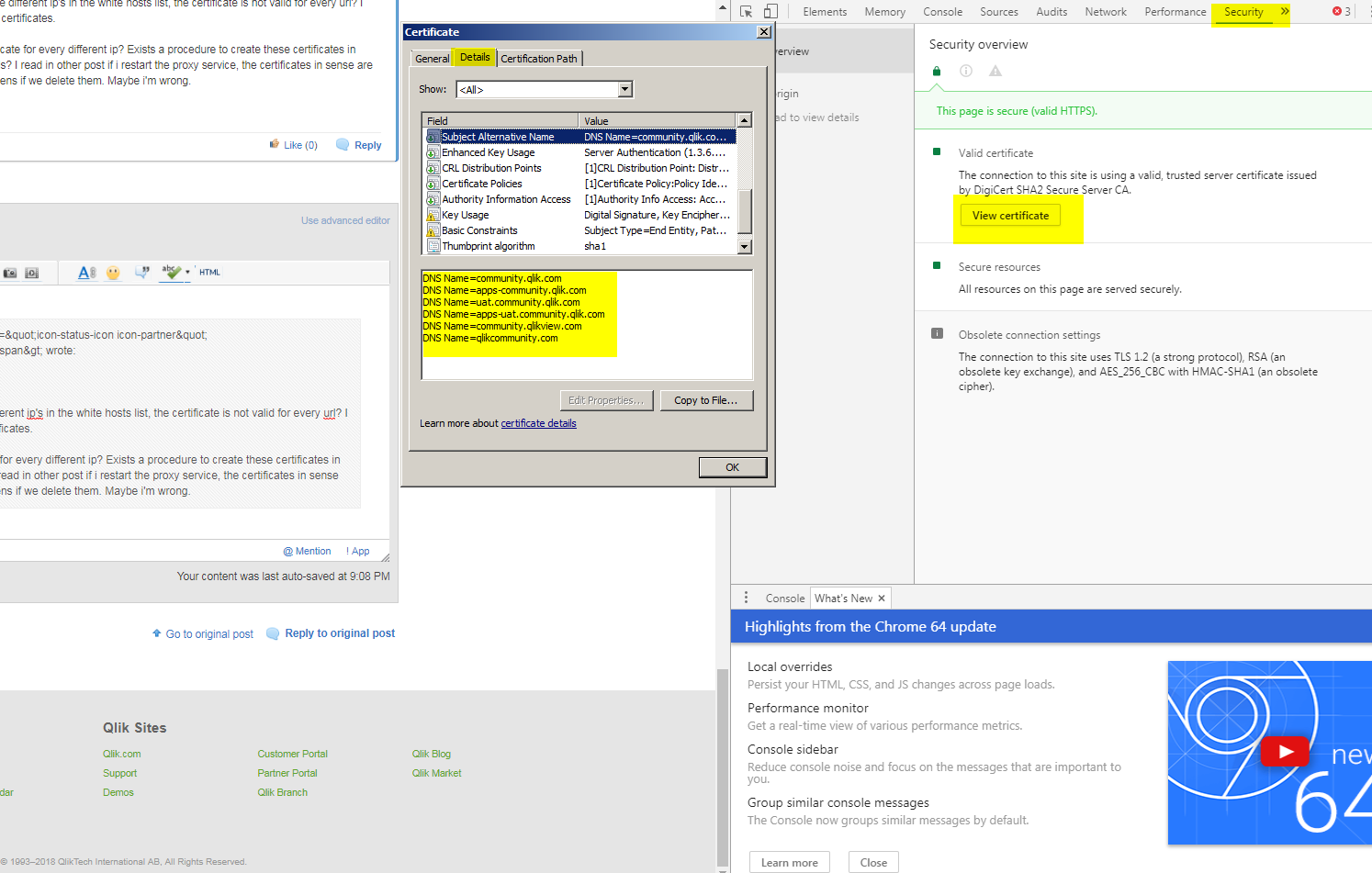
Most browsers have developer tools (commonly accessed by F12) and allow drill down into the certificate specifications for a given site.
* There has been a recent push by browsers to validate based on the DNS Name param rather than the previously used common name: https://www.thesslstore.com/blog/security-changes-in-chrome-58/
Back to your original scenario, are you closing the browser before alternating HTTP vs. HTTPS? Chrome for one certainly does not like getting a cookie issued from a HTTPS site then going to the HTTP variant, I've found.
Hope that helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ideally, no one is reaching your nodes using the IP. And certs only work with DNS names, so that's kind of a moot point. If your client is a Megacorp, they may have a wildcard cert (*.megacorp.com) which you can use. They may not give you the private key, but you should be able to reach out to their Infrastructure group and ask them to install the key on the servers under Service Account.
When you create key request (CSR) you list the domain names you want it to be valid for. So what you would do in your scenario is this.
1. Start a CSR request
2. When you specify the domain, specify MULTIPLE domains qlik.megacorpo.com, qlikrim1.megacorp.com, qlikrim2.megacorp.com...
3. Send off request, receive a keyset
4. Use this single keyset for all your nodes.
The Googleable term for this is "Subject Alternative Names". Take 4 or 5 minutes to read about SANs here, and it should clear things up for you.
SAN Certificates: Subject Alternative Name – Multi-Domain (SAN)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for your reply Levi,
Now i understand much more how the certificates works.
I tried what you say about the access and i will tell you my results.
- « Previous Replies
-
- 1
- 2
- Next Replies »