Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- CVE_2021_44228 - Handling the LOG4J Lookups Critic...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
CVE_2021_44228 - Handling the LOG4J Lookups Critical Vulnerability for Qlik Catalog
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CVE_2021_44228 - Handling the LOG4J Lookups Critical Vulnerability for Qlik Catalog
Jan 25, 2022 7:49:05 AM
Dec 14, 2021 2:03:27 PM
The following two configuration changes may be used to disable the expression evaluation feature of log4j2, and can immediately be applied to single-node Catalog May 2021 through Nov 2021, or any version of multi-node Catalog where log4j2 is on the cluster vendor's Hadoop classpath:
Patches are available. See Vulnerability Testing - Apache Log4j, reference CVE-2021-44228 (also referred to as Log4Shell) for your release and the relevant patch.
Upgrade at the earliest.
Environment
- #QlikCatalog
Resolution for Qlik Catalog (May 2021-Nov. 2021)
Before proceeding, check the first page of Catalog 4.x fix with Log4j 2.17.0. It's highly recommended to apply the fix. However, if you're not ready for the upgrade and you wish to mitigate the vulnerabilities manually, then proceed with the steps below.
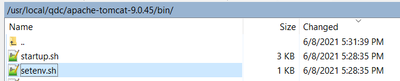
(1) add line to end of bin/setenv.sh:
export JAVA_OPTS="$JAVA_OPTS -Dlog4j2.formatMsgNoLookups=true"
Can't find the file?
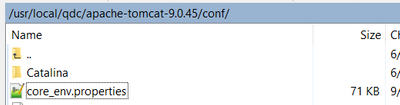
The sample location of the file "setenv.sh":
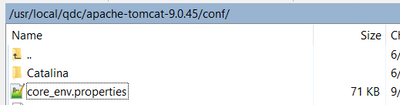
(2) find and edit property in core_env.properties:
# Pipe (|) delimited list of additional arguments to be passed to the Java runtime. Default: none
external.job.runner.extra.java.arguments=-Dlog4j2.formatMsgNoLookups=true
Can't find the file?
The sample location of the file "core_env.properites":
(3) Restart Tomcat.
https://www.lunasec.io/docs/blog/log4j-zero-day-mitigation-guide/
For more information on the Log4j vulnerability, please visit the Support Updates Blog post.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Katie_Davis , @Sonja_Bauernfeind ,
I'd like to add some extra information.
First of all, please check the first page of Catalog 4.x fix with Log4j 2.17.0. It's highly recommended to apply the fix. However if you're not ready for the upgrade and you wish to mitigate the vulnerabilities manually , then the location of the files are (depends on the tomcat version number):
1. the sample location of the file "setenv.sh" :
2. the sample location of the file "core_env.properites":
Hope this helps.
Regards,
John.