Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- CVE_2021_44228 - Handling the log4j lookups critic...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
CVE_2021_44228 - Handling the log4j lookups critical vulnerability for Qlik GeoAnalytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CVE_2021_44228 - Handling the log4j lookups critical vulnerability for Qlik GeoAnalytics
Jan 27, 2022 4:13:15 AM
Dec 13, 2021 3:33:26 PM
Qlik GeoAnalytics Server and the Qlik GeoAnalytics Connector in combination with GeoAnalytics Plus are both affected by the log4j vulnerability.
Patches are available. See Vulnerability Testing - Apache Log4j, reference CVE-2021-44228 (also referred to as Log4Shell) for your release of Qlik GeoAnalytics and the relevant patch.
Upgrade at the earliest.
Mitigation steps are provided below should not upgrade be possible at this time.
The Standard GeoAnalytics Connector for Qlikview and QlikSense (bundled) without GeoAnalytics Plus are not affected by it, they don't use Java.
Environment:
Resolution for GeoAnalytics Server:
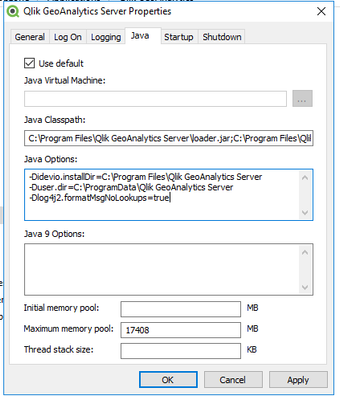
- Start the Configure Service application from the start menu.
- Set the Java options ‐Dlog4j2.formatMsgNoLookups=true inside the Service Properties under the Java tab.
- Restart all GeoAnalytics Services.
Resolution for GeoAnalytics Plus Connector:
- Open C:\Program Files\Common Files\Qlik\Custom Data\QvIdevioConnector\IdevioGeoAnalyticsConnector.exe.config
- Locate the following line (located in appSettings)
<add key="javaArgs" value=""/> - Change the line to:
<add key="javaArgs" value="-Dlog4j2.formatMsgNoLookups=true"/>
This applies only to GeoAnalytics Plus Connector Version May 2021 and higher.
Versions prior to February 2020 uses Log4j v1, which is not vulnerable to this exploit. To prevent any other possible vulnerabilities, we recommend upgrading to a newer version (higher than May 2021) of GeoAnalytics Plus and then applying the mitigation.
Alternatively, you can manually replace the Log4j library files with newer versions:
- Download the binaries of the latest release of Log4j2 (2.17.1 as of this moment): https://logging.apache.org/log4j/2.x/download.html
- Extract the files
- Go to C:\Program Files\Common Files\Qlik\Custom Data\QvIdevioConnector\lib
- For all JAR files starting with "lib4j-"
- Copy the corresponding 2.17.1 JAR file to the lib folder
- Delete the old version of that JAR
For more information on the Log4j vulnerability, please visit the Support Updates Blog post.
As a short update we released:
- GeoAnalytics Server - 4.32.5 - (November 2021 SR3) - 2.17.1
- GeoAnalytics Server - 4.19.2 - 4.27.4 (February 2020 SR2 - May 2021 SR2) - 2.17.1
- GeoAnalytics Plus - 5.31.3 ( November 2021 SR3) - 2.17.1
- GeoAnalytics Plus - 5.29.5-5.30.2 (May 2021 SR3 - August 2021 SR2) - 2.17.1
- GeoAnalytics Plus - 5.27.6-5.28.3 (November 2020 SR2-February 2021 SR2) - 2.17.1
- GeoAnalytics Plus - 5.26.6 (September 2020 SR3) - 2.17.1
- GeoAnalytics Server - 4.32.4 - (November 2021 SR2) - 2.17.0
- GeoAnalytics Server - 4.32.3 - (November 2021 SR1) - 2.16.0
- GeoAnalytics Server - 4.19.1 - 4.27.3(February 2020 SR1 - May 2021 SR1) - 2.16.0
- GeoAnalytics Plus - 5.31.2 ( November 2021 SR2) - 2.17.0
- GeoAnalytics Plus - 5.31.1 ( November 2021 SR1) - 2.16.0
- GeoAnalytics Plus - 5.29.4-5.30.1 (May 2021 SR2 - August 2021 SR1) - 2.16.0
- GeoAnalytics Plus - 5.27.5-5.28.2 (November 2020 SR1-February 2021 SR1) - 2.16.0
- GeoAnalytics Plus - 5.26.5 (September 2020 SR2) - 2.16.0
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@janyfYes, that is Log4j 1 so it is safe from this vulnerability at least.
It is quite old though so I recommend that you upgrade GeoAnalytics Plus when we have a proper patched release out. But you should be ok for now.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can I upgrade GeoAnalytics Plus to May 2021 or newer version regardless of GeoAnalytics Server or GA for Qlik Sense version?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We're using the Qlik GeoAnalytics version February 2020 (5.20.1) together with QlikView April 2019 SR3.
Since this GeoAnalytics version is affected and we're planning updating in early 2022 and you suggested updating in general.
Will GeoAnalytics May 2021 have any issues with the older QlikView April 2019 SR3?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
You can use Qlikview April 2019 with May 2021 even November 2021 see here
For Sense it's September 2019 or newer
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks, that's good news!
So we will update and go with log4j 2.16 (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-45046) to mitigate the risk.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
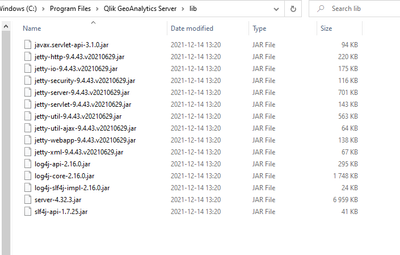
Hi @Sebastian_Linser :
Customer has a GeoQlik Server Version installed. Is there also an action needed due to the current Log4J Bug?
Here is also an screenshot about the log4j version:
This is in use with QlikView. What is your recommendation to do ?
Thanks for your feedback.
Regards
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Qlik is working on a patch for the GeoAnalytics server, for the moment you can only use the workaround with the additional parameter in the Java Settings.
|
GeoAnalytics Server - 4.32.3 |
Log4J Upgrade to 2.16.0 |
Late December |
|
GeoAnalytics Server - 4.27.3 - 4.19.1 |
Log4J Upgrade to 2.16.0 |
Late December
|
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Serkan one more update here. A Patch for GeoAnalytics Server 5.3 has been released and it includes the 2.16 libraries already. Just go tot he download page and get the latest release (Nov2021 SR1)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
As of last weekend it came out that log4j 2.16 doesn't mitigate the security flaw totally. log4j 2.17 seems to completly remove the feature.
Is there any update to 2.17 planned?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Regarding Log4j 2.17.0 / the vulnerability found in 2.16.0 and GeoAnalytics
Here is the description of the vulnerability from the Log4j description of the new CVE:
Apache Log4j2 versions 2.0-alpha1 through 2.16.0 did not protect from uncontrolled recursion from self-referential lookups. When the logging configuration uses a non-default Pattern Layout with a Context Lookup (for example, $${ctx:loginId}), attackers with control over Thread Context Map (MDC) input data can craft malicious input data that contains a recursive lookup, resulting in a StackOverflowError that will terminate the process. This is also known as a DOS (Denial of Service) attack.
And the mitigation:
Implement one of the following mitigation techniques:
- Java 8 (or later) users should upgrade to release 2.17.0.
Alternatively, this can be mitigated in configuration:
- In PatternLayout in the logging configuration, replace Context Lookups like ${ctx:loginId} or $${ctx:loginId} with Thread Context Map patterns (%X, %mdc, or %MDC).
- Otherwise, in the configuration, remove references to Context Lookups like ${ctx:loginId} or $${ctx:loginId} where they originate from sources external to the application such as HTTP headers or user input.
So first I just want to say that this latest vulnerability, unlike the previous ones, is not a remote code execution vulnerability (i.e. an attacker can't trick the software into running their code) but rather a denial of service vulnerability (i.e. an attacker can make the software use more CPU / resources or crash the application due to resource exhaustion).
Secondly, none of the GeoAnalytics products use neither context lookups in our logging patterns nor do we use thread context maps (i.e. the MDC class) that are listed in the description, so this vulnerability does not affect us. Basically we already fulfill the alternative mitigation listed above.
We will however still release patches for this, starting with patches for the November 2021 releases of GeoAnalytics Plus and GeoAnalytics Server. The November patches should be out sometime now in December, and the patches for older versions a bit later due to the holidays.
In related news all of the remaining patches for GeoAnalytics Plus / Server have been sent to the IT team for uploading to the download site and should be available for download as soon as they have had time to upload them.