Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- How To: Configure Qlik Sense Enterprise SaaS to us...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How To: Configure Qlik Sense Enterprise SaaS to use Azure AD as an IdP. Now with Groups!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How To: Configure Qlik Sense Enterprise SaaS to use Azure AD as an IdP. Now with Groups!
May 13, 2024 1:21:30 AM
Jan 11, 2021 8:55:44 AM
This article provides step-by-step instructions for implementing Azure AD as an identify provider for Qlik Cloud. We cover configuring an App registration in Azure AD and configuring group support using MS Graph permissions.
It guides the reader through adding the necessary application configuration in Azure AD and Qlik Sense Enterprise SaaS identity provider configuration so that Qlik Sense Enterprise SaaS users may log into a tenant using their Azure AD credentials.
Content:
- Prerequisites
- Helpful vocabulary
- Considerations when using Azure AD with Qlik Sense Enterprise SaaS
- Configure Azure AD
- Create the app registration
- Create the client secret
- Add claims to the token configuration
- Add group claim
- Collect Azure AD configuration information
- Configure Qlik Sense Enterprise SaaS IdP
- Recap
- Addendum
- Related Content (VIDEO)
Prerequisites
- An Microsoft Azure account
- A Microsoft Azure Active Directory instance
- A Qlik Sense Enterprise SaaS tenant
- The BYOIDP feature in your Qlik license is set to YES. Contact customer support to find out if you are entitled to bring your own identity provider to your tenant.
Helpful vocabulary
Throughout this tutorial, some words will be used interchangeably.
- Qlik Sense Enterprise SaaS: Qlik Sense hosted in Qlik’s public cloud
- Microsoft Azure Active Directory: Azure AD
- Tenant: Qlik Sense Enterprise SaaS tenant or instance
- Instance: Microsoft Azure AD
- OIDC: Open Id Connect
- IdP: Identity Provider
Considerations when using Azure AD with Qlik Sense Enterprise SaaS
- Qlik Sense Enterprise SaaS allows for customers to bring their own identity provider to provide authentication to the tenant using the Open ID Connect (OIDC) specification (https://openid.net/connect/)
- Given that OIDC is a specification and not a standard, vendors (e.g. Microsoft) may implement the capability in ways that are outside of the core specification. In this case, Microsoft Azure AD OIDC configurations do not send standard OIDC claims like email_verified. Using the Azure AD configuration in Qlik Sense Enterprise SaaS includes an advanced option to set email_verified to true for all users that log into the tenant.
- The Azure AD configuration in Qlik Sense Enterprise SaaS includes special logic for contacting Microsoft Graph API to obtain friendly group names. Whether those groups originate from an on-premises instance of Active Directory and sync to Azure AD through Azure AD Connect or from creation within Azure AD, the friendly group name will be returned from the Graph API and added to Qlik Sense Enterprise SaaS.
Configure Azure AD
Create the app registration
- Log into Microsoft Azure by going to https://portal.azure.com.
- Click on the Azure Active Directory icon in the browser Or search for "Azure Active Directory" in the search bar on the top. The overview page for the active directory will appear.
- Click the App registrations item in the menu to the left.
- Click the New registration button at the top of the detail window. The application registration page appears.
- Add a name in the Name section to identify the application. In this example, the name of the hostname of the tenant is entered along with the word OIDC.
- The next section contains radio buttons for selecting the Supported account types. In this example, the default – Accounts in this organizational directory only – is selected.
- The last section is for entering the redirect URI. From the dropdown list on the left select “web” and then enter the callback URL from the tenant. Enter the URI https://<tenant hostname>/login/callback.
The tenant hostname required in this context is the original hostname provided to the Qlik Enterprise SaaS tenant.
Using the Alias hostname will cause the IdP handshake to fail. - Complete the registration by clicking the Register button at the bottom of the page.
- Click on the Authentication menu item on the left side of the screen.
- On the middle of the page, the reference to the callback URI appears. There is no additional configuration required on this page.
Create the client secret
- Click on the Certificates and secrets menu item on the left side of the screen.
- In the center of the Certificates and secrets page, there is a section labeled Client secrets with a button labeled New client secret. Click the button.
- In the dialog that appears, enter a description for the client secret and select an expiration time. Click the Add button after entering the information.
- Once a client secret is added, it will appear in the Client secrets section of the page.
Copy the "value of the client secret" and paste it somewhere safe.
After saving the configuration the value will become hidden and unavailable.
Add claims to the token configuration
- Click on the Token configuration menu item on the left side of the screen.
- The Optional claims window appears with two buttons. One for adding optional claims, and another for adding group claims. Click on the Add optional claim button.
- For optional claims, select the ID token type, and then select the claims to include in the token that will be sent to the Qlik Sense Enterprise SaaS tenant. In this example, ctry, email, tenant_ctry, upn, and verified_primary_email are checked. None of these optional claims are required for the tenant identity provider to work properly, however, they are used later on in this tutorial.
- Some optional claims may require adding OpenId Connect scopes from Microsoft Graph to the application configuration. Click the check mark to enable and click Add.
- The claims will appear in the window.
Add group claim
- Click on the API permissions menu item on the left side of the screen.
- Observe the configured permissions set during adding optional claims.
- Click the Add a permission button and select the Microsoft Graph option in the Request API permissions box that appears. Click on the Microsoft Graph banner.
- Click on Delegated permissions. The Select permission search and the OpenId permissions list appears.
In the OpenID permissions section, check email, openid, and profile. In the Users section, check user.read.
- In the Select permissions search, enter the word group. Expand the GroupMember option and select GroupMember.Read.All. This will grant users logging into Qlik Sense Enteprise SaaS through Azure AD to read the group memberships they are assigned.
- After making the selection, click the Add permissions button.
- The added permissions will appear in the list. However, the GroupMember.Read.All permission requires admin consent to work with the app registration. Click the Grant button and accept the message that appears.
Failing to grant consent to GroupMember.Read.All may result in errors authenticating to Qlik using Azure AD. Make sure to complete this step before moving on.
Collect Azure AD configuration information
- Click on the Overview menu item to return to the main App registration screen for the new app. Copy the Application (client) ID unique identifier. This value is needed for the tenant’s idp configuration.
- Click on the Endpoints button in the horizontal menu of the overview.
- Copy the OpenID Connect metadata document endpoint URI. This is needed for the tenant’s IdP configuration.
Configure Qlik Sense Enterprise SaaS IdP
- With the configuration complete and required information in hand, open the tenant’s management console and click on the Identity provider menu item on the left side of the screen.
- Click the Create new button on the upper right side of the main panel.
- Select OIDC from the Type drop-down menu item, and select Microsoft Entra ID (Azure AD) from the Provider drop-down menu item.
- Scroll down to the Application credentials section of the configuration panel and enter the following information:
- ADFS discovery URL: This is the endpoint URI copied from Azure AD.
- Client ID: This is the application (client) id copied from Azure AD.
- Client secret: This is the value copy and pasted to a safe location from the Certificates & secrets section from Azure AD.
- The Realm is an optional value used if you want to enter what is commonly referred to as the Active Directory domain name.
- Scroll down to the Claims mapping section of the configuration panel. There are five textboxes to confirm or alter.
- The sub field is the subject of the token sent from Azure AD. This is normally a unique identifier and will represent the UserID of the user in the tenant. In this example, the value “sub” is left and appid is removed. To use a different claim from the token, replace the default value with the name of the desired attribute value.
- The name field is the “friendly” name of the user to be displayed in the tenant. For Azure AD, change the attribute name from the default value to “name”.
- In this example, the groups, email, and client_id attributes are configured properly, therefore, they do not need to be altered.
In this example, I had to change the email claim to upn to obtain the user's email address from Azure AD. Your results may vary.
- The sub field is the subject of the token sent from Azure AD. This is normally a unique identifier and will represent the UserID of the user in the tenant. In this example, the value “sub” is left and appid is removed. To use a different claim from the token, replace the default value with the name of the desired attribute value.
- Scroll down to the Advanced options and expand the menu. Slide the Email verified override option ON to ensure Azure AD validation works. Scope does not have to be supplied.
- The Post logout redirect URI is not required for Azure AD because upon logging out the user will be sent to the Azure log out page.
- Click the Save button at the bottom of the configuration to save the configuration. A message will appear confirming intent to create the identity provider. Click the Save button again to start the validation process.
- The validation procedure begins by redirecting the person configuring the IdP to the login page for the IdP.
- After successful authentication, Azure AD will confirm that permission should be granted for this user to the tenant. Click the Accept button.
- If the validation fails, the validation procedure will return a window like the following.
- If the validation succeeds, the validation procedure will return a mapped claims window. If the validation states it cannot map the user's email address, it is most likely because the email_verified switch has not been turned on. Go ahead and confirm, move through the remaining steps, and update the configuration as per the previous step. Re-run the validation to map the email.
- After confirming the information is correct, the account used to validate the IdP may be elevated to a TenantAdmin role. It is strongly recommended to do make sure the box is checked before clicking continue.
- The next to last screen in the configuration will ask to activate the IdP. By activating the Azure AD IdP in the tenant, any other identity providers configured in the tenant will be disabled.
- Success.
- Please log out of the tenant and re-authenticate using the new identity provider connection. Once logged in, change the url in the address bar to point to https://<tenanthostname>/api/v1/diagnose-claims. This will return the JSON of the claims information Azure AD sent to the tenant. Here is a slightly redacted example.
- Verify groups resolve properly by creating a space and adding members. You should see friendly group names to choose from.
Recap
While not hard, configuring Azure AD to work with Qlik Sense Enterprise SaaS is not trivial. Most of the legwork to make this authentication scheme work is on the Azure side. However, it's important to note that without making some small tweaks to the IdP configuration in Qlik Sense you may receive a failure or two during the validation process.
Addendum
For many of you, adding Azure AD means you potentially have a bunch of clean up you need to do to remove legacy groups. Unfortunately, there is no way to do this in the UI but there is an API endpoint for deleting groups. See Deleting guid group values from Qlik Sense Enterprise SaaS for a guide on how to delete groups from a Qlik Sense Enterprise SaaS tenant.
Related Content (VIDEO)
Qlik Cloud: Configure Azure Active Directory as an IdP
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The email isn't mapping because Azure AD does not send a specific claim named "email_verified". This is a claim Qlik Sense SaaS is expecting and not getting, therefore, no mapping your email to the user account created.
We are working on adding the ability to specify the claim that represents "email_verified" so the mapping will work properly. No timeframes of course but I do have an appreciation for the urgency to implement this in SaaS.
The other thing is from your screenshot is you are showing permissions, but not the optional claims you are sending. You need to send the email as an optional claim AND the "primary_verified_email" claim as an optional claim. Once we have the customization in platform (described above) you will be able to tell Qlik Sense IdP config to look for "primary_email_verified" as the claim for email_verified.
jg
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
ok now I got it... all claims are set correctly and I'm geeting it at the diagnose
"verified_primary_email":["henrique@....."]
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Jeffrey_Goldberg
is it on the roadmap to allow anonymous user on SaaS?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Did anybody figure out a workaround or a solution?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Updated configuration now enables to set the email_verified on the IDP config.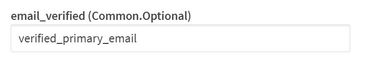
PS:
for current users to get the appropriate email address at the users table (MC) and be able to be notified by emails, you'll need to exclude the current users and ask them to login again as a new user after updating the IDP config. After you'll need to allocate again spaces authorizations. (at least that was the only way for me).
That's not a good idea if you need to exclude app owners as you'll need to reset app ownership on the MC (App Tab) and republish all apps on manage spaces as you can't change it's ownership within the MC. So if you do, do it carefully.
Users IDP Entity remains the same after the new login, so you won't need to update any table used on section access (if its the case).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Nice!
I noticed that too. But using "verified_primary_email" still doesn't make Azure AD provide proper identity mapping. I belive "email_verified": true needs to be in the claims. I can verify at https://xx.eu.qlikcloud.com/api/v1/diagnose-claims that there no such attribute. Any ideas?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
your are not getting the email_verified claim on the diagnose?
I'm getting both email and primary and
"email_verified":["henrique@xxxxxxx"]
"verified_primary_email":["henrique@xxxxxxxx"]
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I do. And that works to add, but it doesn't help with the identity mapping for Azure AD. Tried to sync an app and it loses the owner.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
understood... same here, no idea on how to manage it too...
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi folks, allow me to chime in here. You've stumbled upon the first phase of addressing the email_verified problem some identity providers have with Qlik Sense SaaS configuration. Qlik requires email_verified as a claim in the OIDC handshake because we want to make sure the email is indeed unique and the email intended to be supplied with the credential sent from the IdP.
The email_verified input has been added to the configuration to help you point to a custom claim that you would create in your IdP that would map the custom claim to the email_verified attribute required by Qlik's OIDC implementations.
With respect to Azure AD, just because we've added the input doesn't mean Azure AD will now surface this attribute. In fact, Azure AD will not because Azure AD does not have this claim to send, full stop.
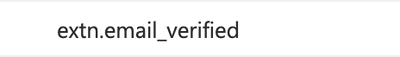
What you can do is add what is called an extension attribute to your app registration (link: https://docs.microsoft.com/en-us/powershell/azure/active-directory/using-extension-attributes-sample...) and then send this as an optional claim using the optional claims configuration in the app registration. You would then map this custom claim to the email_verified input in the Qlik Sense SaaS IdP config for Azure AD.
screenshot of azure ad:
While doable, it's an inelegant solution.
I feel this is a bit clunky, so I've asked our R&D team to investigate implementing a toggle that will set email_verified to true when using AzureAD.
This toggle, in addition to adding group resolution from AzureAD object ids from an Azure AD menu item in the IdP config will be available in the not too distant future.
When it becomes available, I will update the document.
Cheers,
Jeff G