Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Discover
- :
- Blogs
- :
- Product
- :
- Design
- :
- Authorization using a Hierarchy
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hierarchies are very common in all database and business intelligence solutions. Often they are used for authorization purposes, i.e. the permissions to see data follows a hierarchy.
One example is an organizational hierarchy. Each manager should obviously have the right to see everything pertaining to their own department, including all its sub-departments. But they should not necessarily have the right to see other departments.
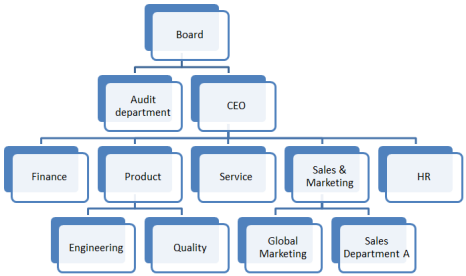
This means that different people will be allowed to see different parts of the organization. The authorization table may look like the following:
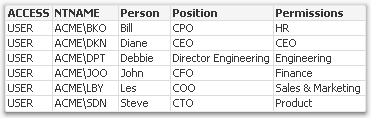
In this case, Diane is allowed to see everything pertaining to the CEO and below; Steve is allowed to see the Product organization; and Debbie is allowed to see the Engineering organization only. Hence, this table needs to be matched against sub-trees in the above hierarchy.
Often the hierarchy is stored in an Adjacent Nodes table, and if so, the above problem is easy to solve: Just load the Adjacent nodes table using a HierarchyBelongsTo and name the ancestor field Tree. See the blog post Unbalanced, n-level hierarchies how this is done.
If you want to use Section Access, you need to load an upper case copy of Tree and call this new field PERMISSIONS. Finally, you need to load the authorization table. These two last steps can be done using the following script lines: (The TempTrees table is the table created by the HierarchyBelongsTo.)
Trees:
Load *,
Upper(Tree) as PERMISSIONS
Resident TempTrees;
Drop Table TempTrees;
Section Access;
Authorization:
Load ACCESS,
NTNAME,
Upper(Permissions) as PERMISSIONS
From Organization;
Section Application;
When you have done this, you should have a data model that looks like the following:
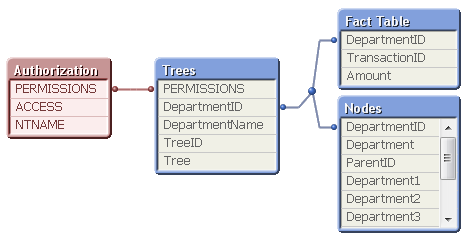
The red table is in Section Access and is invisible in a real application. Should you want to use the publisher for the reduction, you can reduce right away on the Tree field, without loading the Section Access. In either case, this solution will effectively limit the permissions to only the sub-tree as defined in the authorization table.
But what if you have the hierarchy in a horizontal hierarchy? Then you cannot use the HierarchyBelongsTo.
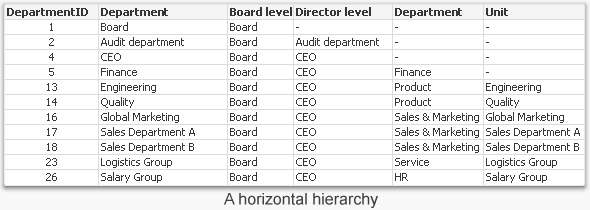
The solution is not very different from the above one. The only difference is that you need to create the bridging table manually, e.g. by using a loop:
Let vHierarchyDefinition = 'Board level,Director level,Department,Unit';
Let vNumberOfLevels = Len(KeepChar(vHierarchyDefinition,',')) + 1 ;
For vAncestorLevel = 1 to vNumberOfLevels
Let vAncestor = Subfield(vHierarchyDefinition,',',vAncestorLevel);
Trees:
Load distinct
Upper([$(vAncestor)]) as PERMISSIONS,
DepartmentID
Resident [Horizontal Hierarchy]
Where Len([$(vAncestor)]) > 0;
Next vAncestorLevel
Having done this, you will have the following data model:
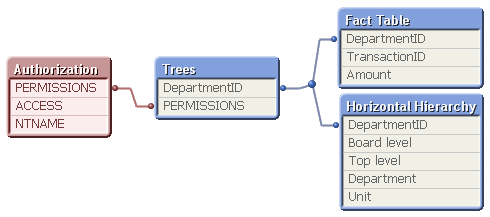
Bottom line is that it is fairly straightforward to implement a hierarchical authorization scheme. See more about Hierarchies in the Tech Brief Hierarchies.
Further reading related to this topic:
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.