Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Discover
- :
- Blogs
- :
- Product
- :
- Support Updates
- :
- QlikView AccessPoint and QMC with HTTPS and a cust...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Here is what we'll need:
- A signed certificate
- A brief (5 minute) downtime of the QlikView WebServer
- (optional) Another brief (5 minute) downtime of the QlikView Management Console
- This blog post 🙂
Note: This blog post does not cover the configuration of Certificate Trust between the QlikView services. For more information about Certificate Trust, check out the QlikView Online Help.
Are the AccessPoint and the Management Console hosted by the same web server?
No. While the AccessPoint is hosted by the QlikView WebServer (QVWS) service, the Management Console is directly served by the QlikView Management Service (QMS).
That means if you wish to swap both from HTTP to HTTPS, both services will need to be individually configured.
But you only need one certificate.
! In this blog post, I will assume that the AccessPoint web server currently in use is the QlikView WebServer (QVWS). The QlikView AccessPoint can be hosted by Microsoft IIS as well, but Microsoft IIS has its own instructions on how to import an SSL certificate for one of its sites.
Certificate options, or: What type of certificate is right for me?
There are three possible types of certificates for us to use:
- A certificate purchased from and signed by a trusted CA (Certificate Authority) such as VeriSign, Thawte, Geotrust, etc.
- A corporate certificate provided and signed by your own Enterprise CA (Certificate Authority).
- And a self-signed one. Those can be created by any number of applications, such as Microsoft IIS, but is generally only recommended for test environments. Since they are not generally trusted or verified, browsers will prompt with warnings if a site was secured using a self-signed certificate. More so, it has the potential side effect of teaching users to ignore browser warnings, which we do not want.
Requirements, or: What to look out for when getting your cert?
- The certificate itself must contain a private key
- Must have an up to date valid from / valid to date range
- Be signed by a valid and OS or browser configured Certificate Authority
As far as formats and algorithms are concerned, the following are confirmed to work with QlikView:
- Certificates that are x509 version 3
- Use signature algorithm sha256RSA
- Use signature hash algorithm sha256
Where to get a certificate and how to do a CSR?
The Certificate Authority you chose will have instructions for this, and if you are looking to get a self-signed one or one from your corporation's CA, then a local administrator can provide the certificate to you.
Either way, you are going to need to generate a Certificate Signing Request (CSR) to pass on to your CA. There are tools out there to get that done with, such as certreq from Microsoft (found here), and SSLhopper has a great article on that, which I often send to customers when they ask us about CSRs and how to do them.
Once you obtain the certificate, we'll move on to installing it and binding it to the desired ports.
This will be done in three steps:
- Import/Install
- Bind the certificate using PowerShell or the Windows command prompt
- Configure the QVWS and, optionally, the QMS
Importing the Certificate
We only need to import/install it once (unless you have your services across multiple machines).
Step 1:
On the QlikView node running the QlikView WebServer, log on with the user running the QlikView services. This is important since the certificate needs to be accessible for this account.
(Optional:) If you want to switch the Management Console to HTTPS as well, and the services are not on the same machine, repeat the step on the node running the QlikView Management Service.
Step 2:
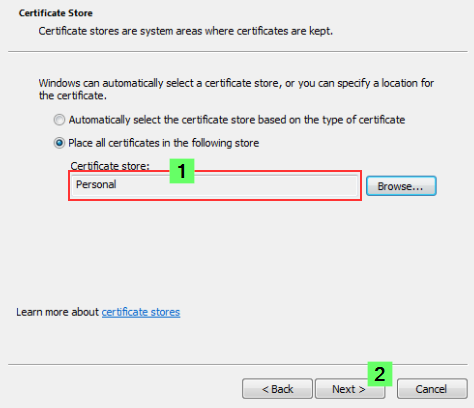
If the certificate was saved in the .pfx format, then all you need to do is double-click the file. Follow the prompt to import the certificate into the Personal store.
Longer Step 2:
If you want to import it manually or verify if it was correctly installed, then we'll need to do a little more work.
- Launch the Microsoft Management Console (mmc.exe) on the QVWS (and QMS) node
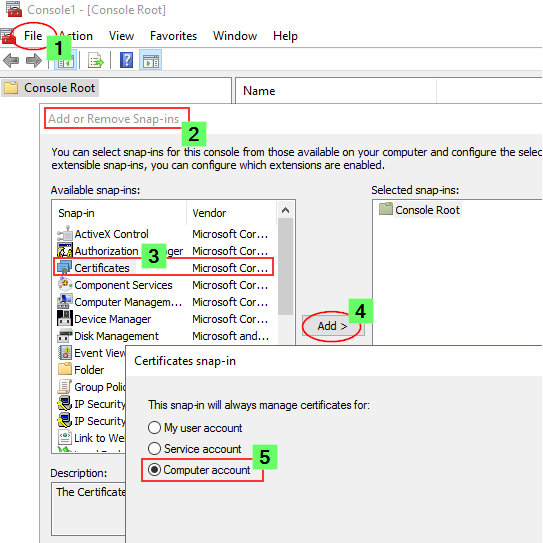
- In the MMC, go to File > Add / Remove Snap-in...
- Select Certificates and click Add
- Select Computer account, click Next, select Local computer and click Finish.
- In the MMC, go to Certificates (Local Computer)/Personal
- In the MMC, go to Actions > All Tasks > Import...
- Browse to the certificate file provided to you from your CA
- Follow the instructions on the screen to import the certificate, including the private key
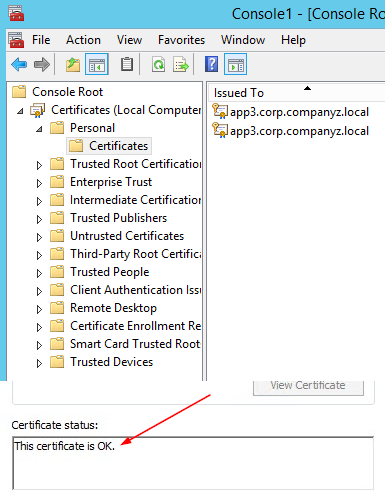
- Verify the new certificate has been imported into Certificates (Local Computer) > Personal > Certificates and that it contains a private key
- Double-click the Certificate > Certification Path and confirm it shows "This certificate is OK"
- Don't close any of this yet, we'll need it in a moment.
Binding the certificate to the correct port and address.
Next, we need to manually bind the certificate to the correct port and IP address. This is done using either PowerShell or the Windows command prompt and the netsh command. For details on netsh, see the official Microsoft documentation.
For this we will need:
- The certificate Thumbprint
- An Application ID (random GUID)
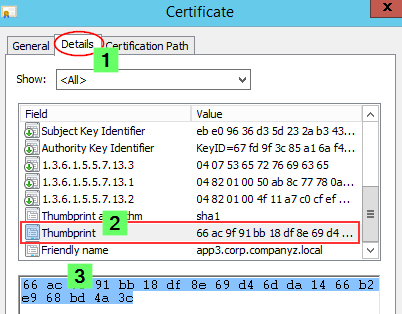
Step 1: Get the Thumbprint
Since we are already in the MMC, let's open the freshly installed certificate again and:
- Switch to the Details tab and scroll down until you find Thumbprint
- Mark the entire thing and copy it into, for example, Notepad.
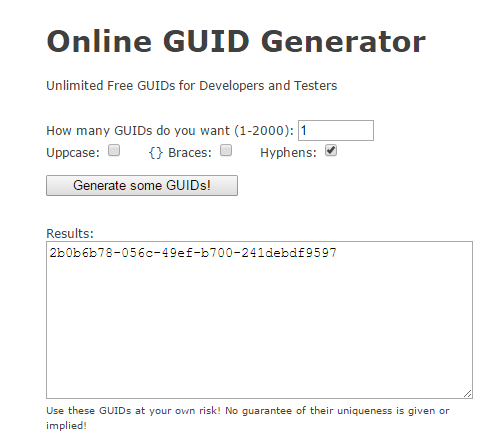
Step 2: Get an AppID (Application ID, GUID)
There is a wide range of different tools available to generate GUIDs. My favorite is https://www.guidgenerator.com/
Click Generate some GUIDs! Copy that into Notepad as well.
(Optional:) Generate and save two if you want to use one for the Management Console as well.
Step 3: Bind the certificate
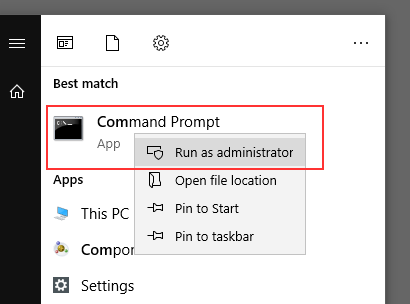
Open either PowerShell or a Windows command prompt with elevated permissions.
Let's assume the thumbprint is 55ab3131fbd585ad3ad817f25aee025a51a2ffb5 and the GUID is e23183e3-c874-467a-bd39-d110cd066f1f. Based on this, we will build the following command:
For the AccessPoint:
netsh http add sslcert ipport=0.0.0.0:443 certhash=55ab3131fbd585ad3ad817f25aee025a51a2ffb5 appid={e23183e3-c874-467a-bd39-d110cd066f1f}
For the Management Console:
netsh http add sslcert ipport=0.0.0.0:4780 certhash=55ab3131fbd585ad3ad817f25aee025a51a2ffb5 appid={UseTheSecondGUID}
We are using ipport=0.0.0.0 in our examples. If you wish to restrict the target IP address, meaning only a specific IP address can be used in combination with this certificate, then specify that here.
Also, note how we are using port 4780 for the Management Console. You can choose a different port. Instructions for that are a little further down.
If you wish to verify the port bindings, use the netsh http show sslcert command line.
It should look like this:
IP:port : 0.0.0.0:443
Certificate Hash : 55ab3131fbd585ad3ad817f25aee025a51a2ffb5
Application ID : {e23183e3-c874-467a-bd39-d110cd066f1f}
Certificate Store Name : (null)
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled
Configuring the QlikView service
Almost done!
The QlikView Webserver
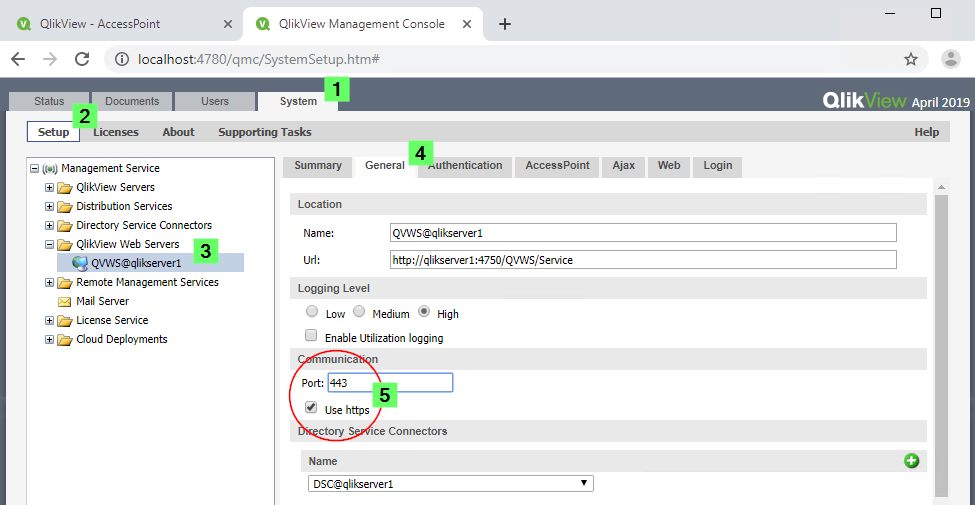
- Open the QlikView Management Console
- Navigate to System > Setup > QVWS@YourQlikServer > General
- Configure Communication to port 443 and tick the Use https checkbox.
- Restart the QlikView WebServer
- You can verify by opening the latest log file in C:\ProgramData\QlikTech\WebServer\Log and checking what port and protocol is now used:
Information register prefix: "https://+:443/scripts/"
Information register prefix: "https://+:443/qvajaxzfc/"
Information register prefix: "https://+:443/scripts/"
Information register prefix: "https://+:443/qlikview/"
Information register prefix: "https://+:443/qvdesktop/"
Information register prefix: https://+:443/qvplugin/
The QlikView AccessPoint can now be opened using https://YourWebServer/qlikview.
If you're looking to implement HSTS (HTTP Strict-Transport-Security) as well, see QlikView HSTS (HTTP Strict-Transport-Security response header).
The Management Service
- Stop the QlikView Management Service
- Open the file C:\Program Files\QlikView\Management Service\QVManagementService.exe.config
- Modify the following tag (set to True😞
<add key="UseHTTPS" value="True"/> - Optional: Find the section:
<!-- ****** QlikView Management Service - FRONTEND ****** -->- Set the value to the port the certificate was bound to in the following tag:
<add key="QMSFrontendWebServicePort" value="YOURPORT"/>
- Set the value to the port the certificate was bound to in the following tag:
- Start QlikView Management Service
- Test the QMC by accessing it through https://YourQMSServer:YOURPORT/qmc
If you're looking to implement HSTS (HTTP Strict-Transport-Security) as well, see QlikView HSTS (HTTP Strict-Transport-Security response header).
Troubleshooting
The parameter is incorrect
If, during the binding process, you are getting an error of The parameter is incorrect, then this is likely caused by a hidden character copied along with the certificate thumbprint. Use your arrow keys to the left and right of the copied key to see if there is a blank space that needs to be removed.
Internet Explorer Plugin complains that "This page contains both secure and non-secure items"
And that’s it 😊
Don’t forget to subscribe to our Qlik Support Update Blogs so you don’t miss out on any new content delivered by #QlikSupport. As always, we’ll be watching for comments and questions and your feedback is always appreciated!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.